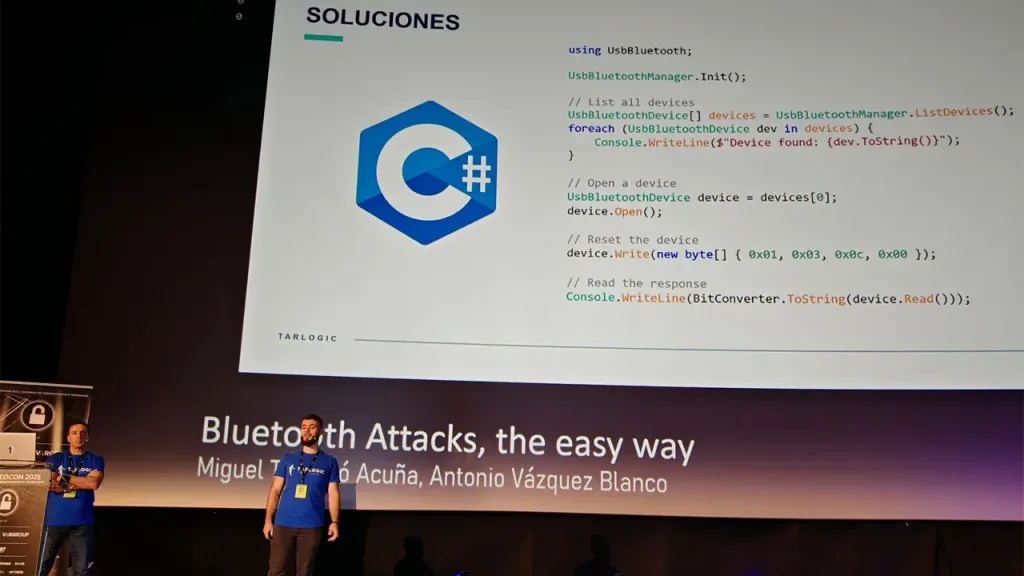
Attackers can use undocumented commands to hijack Chinese-made Bluetooth chips
Security researchers have shared details of newly discovered, undocumented commands in ESP32 Bluetooth firmware that can be exploited by an attacker. The Chinese-made chip is found in millions of devices, meaning the findings are significant.
Speaking at RootedCON in Madrid, researchers from Tarlogic Security, Miguel Tarascó Acuña and Antonio Vázquez Blanco, described the “hidden functionality” they have unearthed as a backdoor, but later conceded that this may be a misleading description. They warn that exploitation could allow “hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls”.

BrakTooth: security researchers reveal 16 serious Bluetooth flaws affecting billions of devices
Security researchers from the Singapore University of Technology and Design have disclosed a new family of security vulnerabilities in commercial Bluetooth stacks used in billions of devices. Collectively known as BrakTooth, the vulnerabilities pose a range of risks including remote code execution and DoS via crashes and deadlocks.
The Bluetooth stacks found to be vulnerable are used in System-on-Chip (SoC) boards from various big-name manufacturers including Qualcomm, Texas Instruments and Silicon Labs; numerous Microsoft products are also affected, including Surface Pro 7, Surface Laptop 3, Surface Book 3 and Surface Go 2.
