
How to avoid phishing scams as we approach this year's tax deadline
U.S. taxpayers beware! Tax scams and malware attacks are running rampant as we approach this year's tax deadline -- mostly driven by phishing scams.
With the looming April 18 US tax deadline, cybercriminals have sprung into action. For one, a devious Emotet malware phishing campaign has been launched, masquerading as official W-9 tax form emails sent from the Internal Revenue Service (IRS) and companies that may be connected to your work life. A malicious group known as Tactical#Octopus is also on the prowl and looking to spread malware through fake file downloads claiming to be related to taxes.

Phishing attacks bounce back after pandemic slowdown
After a tailing off during the pandemic, phishing is back, with more attacks spotted in the second quarter of this year than for the whole of 2021.
The latest phishing and malware report from Vade also shows that malware emails decreased 48 percent month-on-month -- down from 32.9 million in March to 17 million in April -- but rebounded 31 percent May, with 22.4 million malware-weaponized emails detected. June saw even higher malware volumes (28.9 million), a 29 percent increase from the previous month.

Emotet rockets to the top of the malware charts in Q1
The latest Threat Insights Report from HP Wolf Security shows a 27-fold increase in detections resulting from Emotet malicious spam campaigns in the first quarter of 2022.
Based on findings from millions of endpoints running HP Wolf Security, this makes Emotet the most seen malware family in the period accounting for nine percent of all malware captured.

Old botnets make a comeback
Several older botnets have seen a resurgence in activity in the first quarter of 2022, including Mirai, STRRAT and Emotet, according to the latest threat report from Nuspire.
Mirai, known for co-opting IoT devices to launch DDoS attacks and first seen in 2016, showed a spike in activity in February of this year. This corresponded with the discovery of Spring4Shell, a zero-day attack on popular Java web application framework, Spring Core. The attack allows for unauthenticated remote code execution, and data show Mirai exploited this vulnerability to its botnet.

Emotet bounces back at the end of last year following earlier take down
One of the more significant good news security stories of last year was the culmination of an international effort in January to take down the Emotet botnet.
Sadly it seems that you can't keep a bad botnet down for long. The latest Q4 and Year in Review Threat Report from Nuspire shows Emotet bouncing back, with steadily increasing levels of activity throughout December.

Malicious office documents make up 43 percent of malware downloads
Infecting office files has been a popular malware technique for some time but is still popular among cybercriminals as it allows them to evade many detection solutions. New research from AtlasVPN reveals that 43 percent of all malware downloads in the second quarter of this year were malicious office documents.
This is an increase from the same period in 2020 when only 14 percent of malware came in office files. In the third quarter of last year the volume jumped to 38 percent before declining to 34 percent in Q4 2020 and Q1 2021.

FBI hands over four million compromised email addresses from Emotet to Have I Been Pwned
Three months ago, law enforcement agencies from across the planet worked together to bring down Emotet, one of the world's most infamous botnets.
This action resulted in huge numbers of compromised email addresses being obtained by the various agencies, and the FBI has now offered these to Have I Been Pwned (HIBP) to make it easier for anyone to check if their information was harvested and used by Emotet.

International law enforcement effort takes down Emotet from the inside
Law enforcement authorities in the Netherlands, Germany, the US, the UK, France, Lithuania, Canada and Ukraine have collaborated to disrupt Emotet, one of the most significant botnets of the past decade.
The effort, coordinated by Europol the joint European policing agency, gained control of the Emotet infrastructure and took it down from the inside. Infected machines of victims have been redirected towards this law enforcement-controlled infrastructure.

Malware activity spikes as attackers become more ruthless
The latest threat quarterly landscape report from managed security service provider Nuspire shows a 128 percent increase in Q3 over the previous quarter, representing more than 43,000 malware variants detected a day.
The report also shows threat actors developing a more ruthless streak in selecting their targets. Throughout Q3, hackers shifted focus from home networks to overburdened public entities, including the education sector and the Election Assistance Commission (EAC).

How the pandemic has reinvigorated Emotet [Q&A]
The US Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) has recently put out a warning concerning a surge in activity from the group behind the Emotet trojan.
Emotet has been around for some time and has mostly been associated with banking trojans, but this year’s upsurge in activity has seen it branch out into other areas.
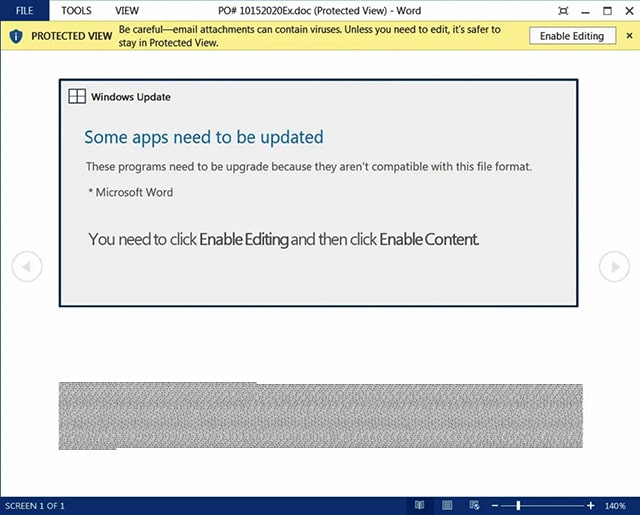
Beware the 'Windows Update' that can install malware, steal your personal information, and encrypt your PC
Emotet began life as a banking Trojan back in 2014 but has since evolved into something much worse -- a self-propagating platform that can deploy multiple exploits and spam campaigns.
The number one malware threat today, Emotet usually takes a break during the summer months while the developers behind it work to add new features and capabilities, and now it’s back with a new 'Windows Update' attachment.
