
Ransomware revenue rises to $1bn
A new report from Trend Micro has revealed that the use of ransomware by cyber attackers increased by 752 percent in 2016.
In the last year alone, the security software company estimates that Locky, Goldeneye and other malware designed to extort a ransom from its victims earned attackers $1 billion.

WannaCry was most Americans’ first experience of ransomware
Although ransomware in some form has been around since 2005, a new survey of 5,000 US consumers reveals that for 57 percent the recent WannaCry attack was their first exposure to how it works.
The study by endpoint security company Carbon Black also shows that seven out of 10 consumers would consider leaving a business if it were hit by ransomware.

XData ransomware starts wreaking havoc
The dust hasn’t even settled around WannaCry, another ransomware appears. This one was detected by ESET and identified as Win32/Filecoder.AESNI.C.
Security researchers dubbed it XData ransomware. It appears mostly in Ukraine (96 percent of cases). The outbreak seems to have started on May 17, reaching its peak on May 19.

It's Windows 7 -- not Windows XP -- that's to blame for the spread of WannaCry ransomware
It’s been a week since the WannaCrypt/WannaCry ransomware cyber attacks began, and the repercussions are still being felt. It became clear quite early on that the ransomware was hitting older Windows systems hard (Windows 10 wasn’t affected), with a lot of talk focusing on the number of at-risk Windows XP systems still in service.
But here’s the interesting thing. Most of the affected systems -- over 98 percent -- were actually running Windows 7.

WannaCry: How to recover encrypted files
The WannaCry ransomware has made a huge mess across the globe, affecting hundreds of thousands of PCs, including critical devices in the healthcare sector. It is so dangerous that Microsoft released a public patch for Windows XP, after it dropped support three years ago.
Of course, the patch did not stop Windows XP users from getting infected, but, thankfully, a decryption tool, called WannaKey, is now available and should help recover your locked files. And the good news is that it works on other operating systems too, including Windows 7 (the x86 version, anyway) and Windows Server 2008!

After WannaCry chaos, ShadowBrokers threaten 'Data Dump of the Month' service, including Windows 10 exploits
News over the past week has been dominated by the fallout from the WannaCry ransomware. Now the hacking group that released the NSA's hacking tool kit into the wild has announced plans to start an exploit subscription service in June.
ShadowBrokers used a blog post to announce that next month will see the launch of "TheShadowBrokers Data Dump of the Month" service. Described as "being like wine of month club," such a subscription service would attract a great deal of interest from intelligence agencies and would-be hackers alike, particularly if -- as the group suggests -- it includes access to Windows 10 exploits.
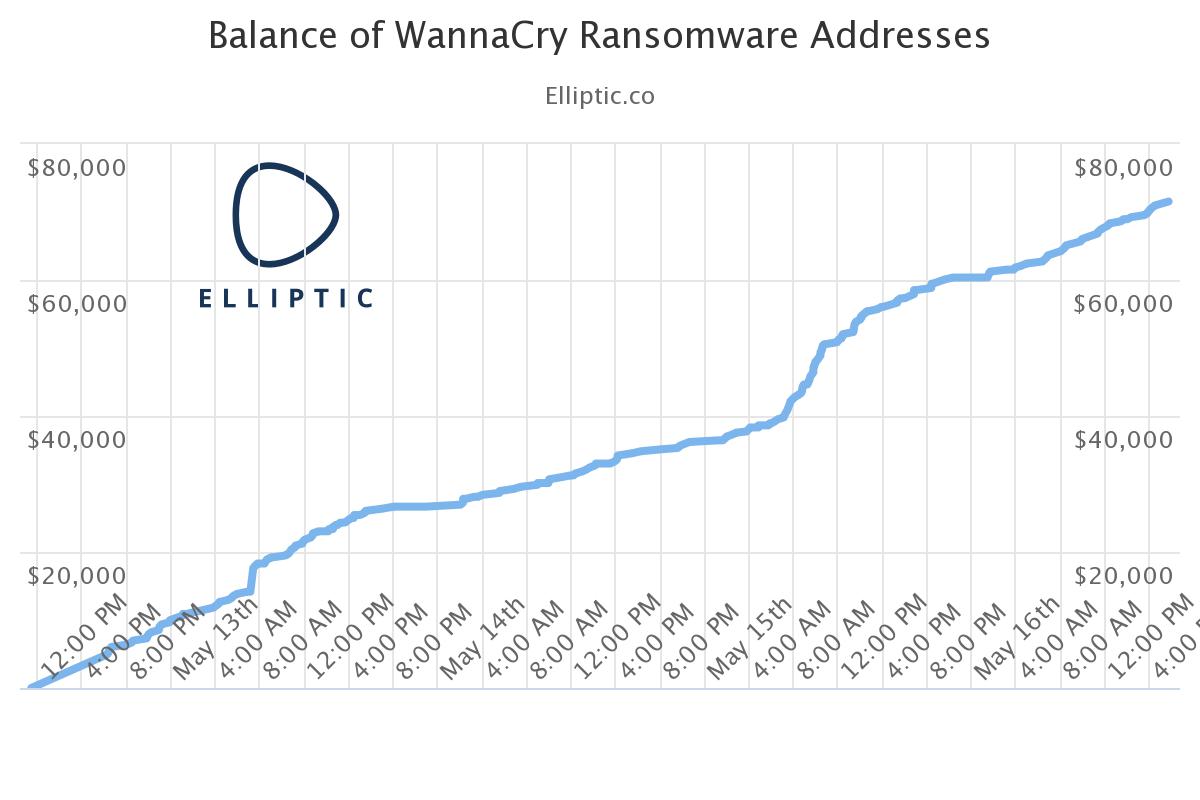
Watch how much money WannaCry generates in ransom -- in near real time
The WannaCry/WannaCrypt ransomware attack has hit businesses and individuals hard. It has now infected and locked over 300,000 computers across more than 150 countries.
It’s the most successful -- and damaging -- cyber attack in years, despite being rather poorly executed. If you’ve wondered how much money such an attack generates we have the answer -- and it’s not as much as you might think, given the scale.

Vladimir Putin says the WannaCrypt cyber-attack is nothing to do with Russia
With Russia being blamed for having a hand in fixing both the US and French elections, Russian President Vladimir Putin must be feeling at least a little smug that the WannaCrypt ransomware currently wreaking havoc around the world has nothing to do with his country.
Asked about the threat while at an international summit in Beijing, Putin said it was "worrisome" but that the United States, not Russia, was to blame.

The WannaCrypt attack -- what we know and how to protect yourself
What seemed to have begun as just another ransomware attack hit the headlines last Friday (May 12th) when it began to attack hospitals and healthcare services in the UK. It became clear pretty quickly that this was in fact something much bigger however, with problems reported at businesses and government bodies around the world.
Infections by the malware known as WannaCrypt or WannaCry, began in Spain with the Telefonica telecommunications giant one of the first to be hit. It then quickly spread to the United Kingdom, Russia, Japan, Taiwan, the United States, and many others. In total, over 150 countries have been affected by the ransomware since Friday, according to Europol.

Microsoft should be applauded for its response to the WannaCrypt crisis
I’ve certainly been highly critical of Microsoft in the past, particularly last year when the company began forcing Windows 10 on to users.
But in the past couple of days I have to admit that I’ve been impressed by the software giant’s response to the global WannaCrypt/WannaCry crisis, and not just in patching Windows XP.

Microsoft blames US Government for 'WannaCrypt' ransomware disaster
The "WannaCrypt" ransomware has proven to be a disaster globally. This malware will encrypt a user's files and then demand some Bitcoin ransom to decrypt them. While the amount being demanded is relatively low at $300 or $600, the scam can be modified for even larger amounts. Heck, even after the ransom is paid, there is no guarantee that the bad guys will follow through with the decryption, making it quite the gamble. As the ransomware has disrupted government agencies, medical services, and other critical computers, the ransom is being paid by some, as it can literally be the the difference between life and death -- surgeries and other procedures have been delayed.
While there are many directions in which you can point the finger of blame, Microsoft should absolutely not shoulder any of the responsibility. After all, the vulnerability that led to the disaster was patched back in March. It never even affected the most recent version of the operating system, Windows 10. The company has even since patched the archaic Windows XP! So who is to blame? Users and administrators that failed to keep their systems up to date are partially at fault. The biggest blame belongs to an unlikely party -- the US Government! You see, an agency of our own government -- the NSA -- knew about the exploit, and rather than alert Microsoft, it chose to stockpile it for intelligence purposes. Sadly, the exploit itself got leaked, and as a result, it landed into the hands of evildoers.

Microsoft patches Windows XP to fight the WannaCrypt ransomware attacks
Microsoft stopped supporting Windows XP back in 2014, but today it releases one more security update for the ancient OS.
The software giant is taking this "highly unusual" step to fight back against the WannaCrypt ransomware cyber attacks that have so far hit nearly 100 countries around the world. And XP is not the only unsupported system receiving this patch.

Over-reliance on one defensive layer leads to ransomware attacks: prepare early, check often
Since its first appearance more than 20 years ago, ransomware has become one of the most discussed cyber threats -- affecting companies of all sizes, across all industries.
We cannot go a couple of days without seeing a new breach headline as a result of a ransomware attack (today's attack on healthcare is a prime example). The threat environment is becoming more dangerous because enterprises are not adequately prepared to protect, defend, respond or remediate.

NHS hospitals hit by ransomware attack [Update: Now spreading globally]
Hospitals and doctors' surgeries across the UK have been hit by what is being described as a large scale ransomware attack.
The attack is believedto have begun at around 1:30 pm today. Areas affected include East and North Hertfordshire, North Cumbria, Blackpool, and Barts Health in London.

Ransomware continues to dominate the cyber threat landscape
A new report from Panda Security's PandaLabs research arm reveals that real time attacks that involve direct interaction with the victim are on the rise.
It also shows the increasing professionalism of cyber criminals. Highly specialized groups are forming in fields like the creation and distribution of malware and exploits. An example covered by PandaLabs is the RDPatcher attack, the purpose of which is to put the victim’s computer up for sale on the black market for use in a bot network.
