New platform helps protect IoT devices
There are likely to be around 31 billion IoT devices by the end of this year and we already know that they can be vulnerable to attacks.
Israeli company Karamba Security is launching its XGuard Monitor platform aimed at managing the security of large numbers of IoT devices.

Spammers get better at pretending to be banks
As always, spammers and cybercriminals seek to take advantage of the peak online shopping season covering Black Friday and the Christmas holidays.
The Bitdefender Antispam Lab has identified a series of campaigns impersonating online banking and financial organizations. In October six in 10 emails (58.84 percent) relating to the banking industry were fraudulent.

DNS threats expected to surge over the holidays
With more people shopping online than ever before, 78 percent of cybersecurity professionals say they expect to see an increase in DNS-related security threats over the next month.
This is according to a new report from information services and technology company Neustar's International Security Council which also finds that 59 percent have altered their DNS security methods in the run up to the holiday season.

Number of 2020 vulnerabilities set to overtake last year
The latest report from Risk Based Security reveals that the number of vulnerability disclosures this year is back on track to reach or surpass 2019 after a decline in the first quarter.
Earlier in the year there had been a sharp decline of 19.2 percent in the number of vulnerabilities disclosed. But on the latest figures Risk Based Security's VulnDB team aggregated 17,129 vulnerabilities disclosed during the first three quarters of 2020, marking a mere 4.6 percent gap when compared to last year.

Insider threats now more common than external ones
A new report from Netwrix shows that cybersecurity risks related to insiders are now more common than external threat actors.
In fact, since organizations have increased remote working, four of the top six types of cybersecurity incidents they experienced have been caused by internal users. These are: accidental mistakes by admins (27 percent), accidental improper sharing of data by employees (26 percent), misconfiguration of cloud services (16 percent) and data theft by employees (14 percent).

Linux Foundation launches open source identity and access management platform
Verifying digital identity is fundamental to building trust in online security and conducting commercial and personal transactions safely. But it can also prove a performance headache for businesses.
Non-profit organization, The Linux Foundation, is today announcing the launch of the Janssen Project, a cloud native identity and access management software platform that prioritizes security and performance.

User experience wins out over security
While security is clearly a concern for IT professionals, providing the best application experience is more important, with 87 percent saying that security will need to better support the user experience.
This is among the findings of a new study of IT decision makers from Menlo Security, which shows slow access speeds (46 percent), poor connectivity (33 percent), no/ loss of access to resources (28 percent), downtime (27 percent) and decreased productivity due to increased security (27 percent) are all experience-related issues cited by respondents.

Open source developers spend less than three percent of their time on security
The latest FOSS (Free and Open Source Software) contributor survey from the Open Source Security Foundation (OpenSSF) and the Laboratory for Innovation Science at Harvard shows respondents spend on average, just 2.27 percent of their total time on security and express little desire to increase that time.
The survey of almost 1,200 respondents working on FOSS software shows the majority of respondents (74.87 percent) are already employed full-time and more than half (51.65 percent) are specifically paid to develop FOSS.

ID fraud surges during pandemic as more people turn to crime
Over the past year the average identity document (ID) fraud rate has increased by 41 percent over the previous year and first-time fraudsters appear to be more prevalent.
A new report from identity verification and authentication provider Onfido shows activity peaked in July and August. But with large parts of Europe encountering a 'second wave' and re-entering lockdown, coupled with the spike in online activity for the holiday shopping season, Onfido predicts fraud rates will start to climb again as the year closes.

5G adoption brings new security risks
Most professionals say their organizations are concerned about cybersecurity risks related to 5G adoption according to a new poll from consulting firm Deloitte.
The findings show those at organizations planning to adopt 5G in the year ahead are slightly more worried (80.7 percent) than those currently using 5G (76.4 percent).

Education sector not prepared for cybersecurity in the age of COVID
New research from Malwarebytes reveals that 46.7 percent of IT decision-makers in schools say that no additional requirements have been introduced for students, faculty, or staff who connected to the school's network remotely during the pandemic.
In addition 50.7 percent of IT decision-makers surveyed say that no one was required to enroll in cybersecurity training before the new school year began

IBM discovers hackers targeting COVID vaccine supply chain
The recently announced COVID-19 vaccines require a 'cold chain' -- a temperature-controlled supply chain that maintains the desired temperature range throughout distribution.
New research from IBM Security X-Force reveals that this cold chain is being targeted in a precision phishing campaign.

Dashlane names the password 'worst offenders' of 2020
This year more than ever we've all been spending large amounts of time online and that often means relying on passwords to access systems and sites.
According to password management app company Dashlane the average internet user has over 200 digital accounts that require passwords, and that figure is projected to double in the next five years.

How security operations centers can beat 'alert overload' and reach maturity [Q&A]
Security operations centers are on the front-line of any organization's battle to protect itself from threats. But many of the teams in these vital facilities are working without the time, staff and resources they need to operate at peak capacity. One of the major problems facing SOCs is 'alert overload', a phrase which describes the difficulty in dealing with the avalanche of alerts generated every day of the week.
To find out how SOCs can beat this problem and achieve operational maturity, we spoke to Faiz Shuja, co-founder and CEO atrisk-based security specialist SIRP.
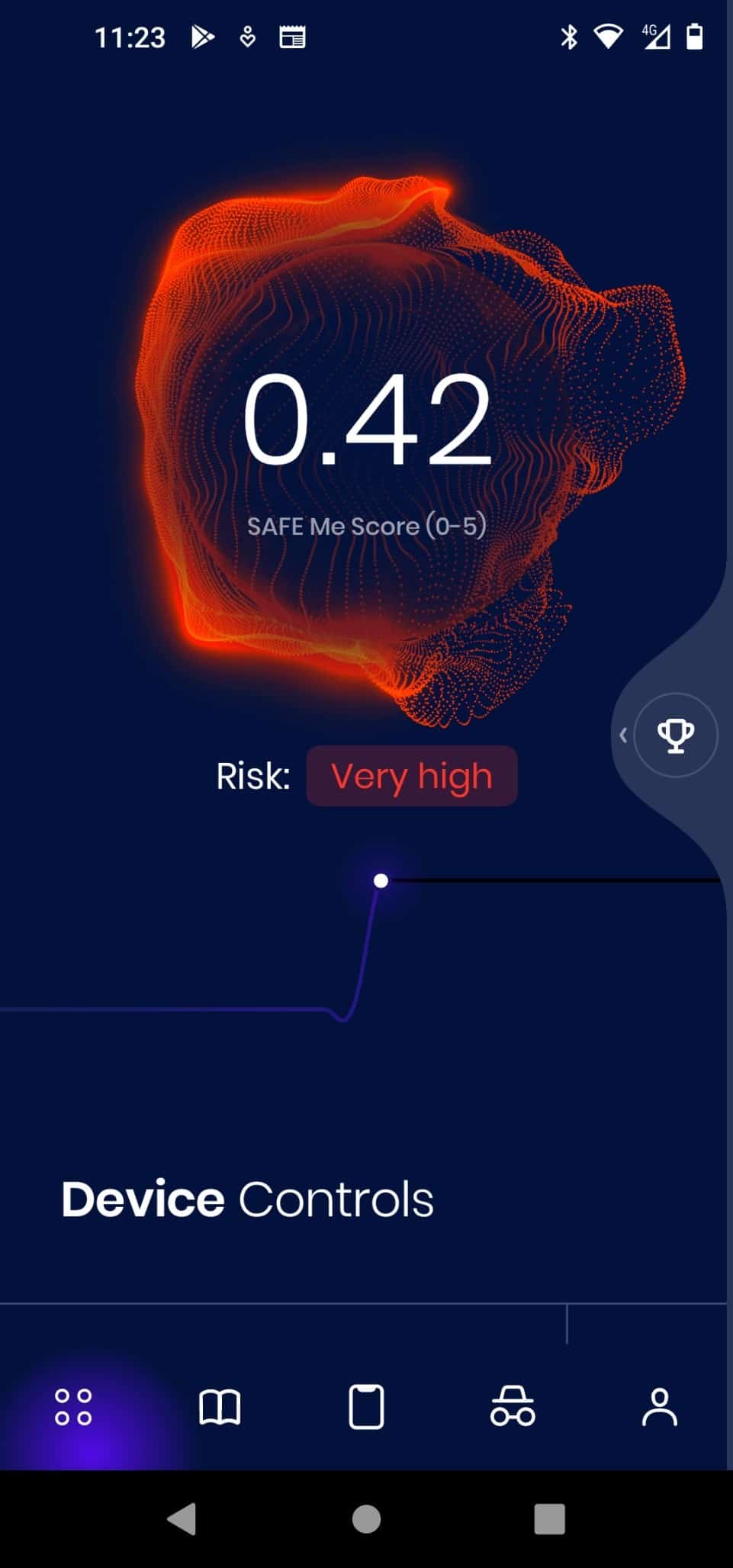
Free app helps consumers understand and reduce their cyber risk
Cybercrime is a major concern and many people worry about the threat of their personal data being stolen, leading to identity theft.
A new free app from cybersecurity and digital business risk quantification specialist Lucideus aims to fundamentally change the way consumers secure and protect their digital lives.
