
Dashlane names the password 'worst offenders' of 2020
This year more than ever we've all been spending large amounts of time online and that often means relying on passwords to access systems and sites.
According to password management app company Dashlane the average internet user has over 200 digital accounts that require passwords, and that figure is projected to double in the next five years.

How security operations centers can beat 'alert overload' and reach maturity [Q&A]
Security operations centers are on the front-line of any organization's battle to protect itself from threats. But many of the teams in these vital facilities are working without the time, staff and resources they need to operate at peak capacity. One of the major problems facing SOCs is 'alert overload', a phrase which describes the difficulty in dealing with the avalanche of alerts generated every day of the week.
To find out how SOCs can beat this problem and achieve operational maturity, we spoke to Faiz Shuja, co-founder and CEO atrisk-based security specialist SIRP.
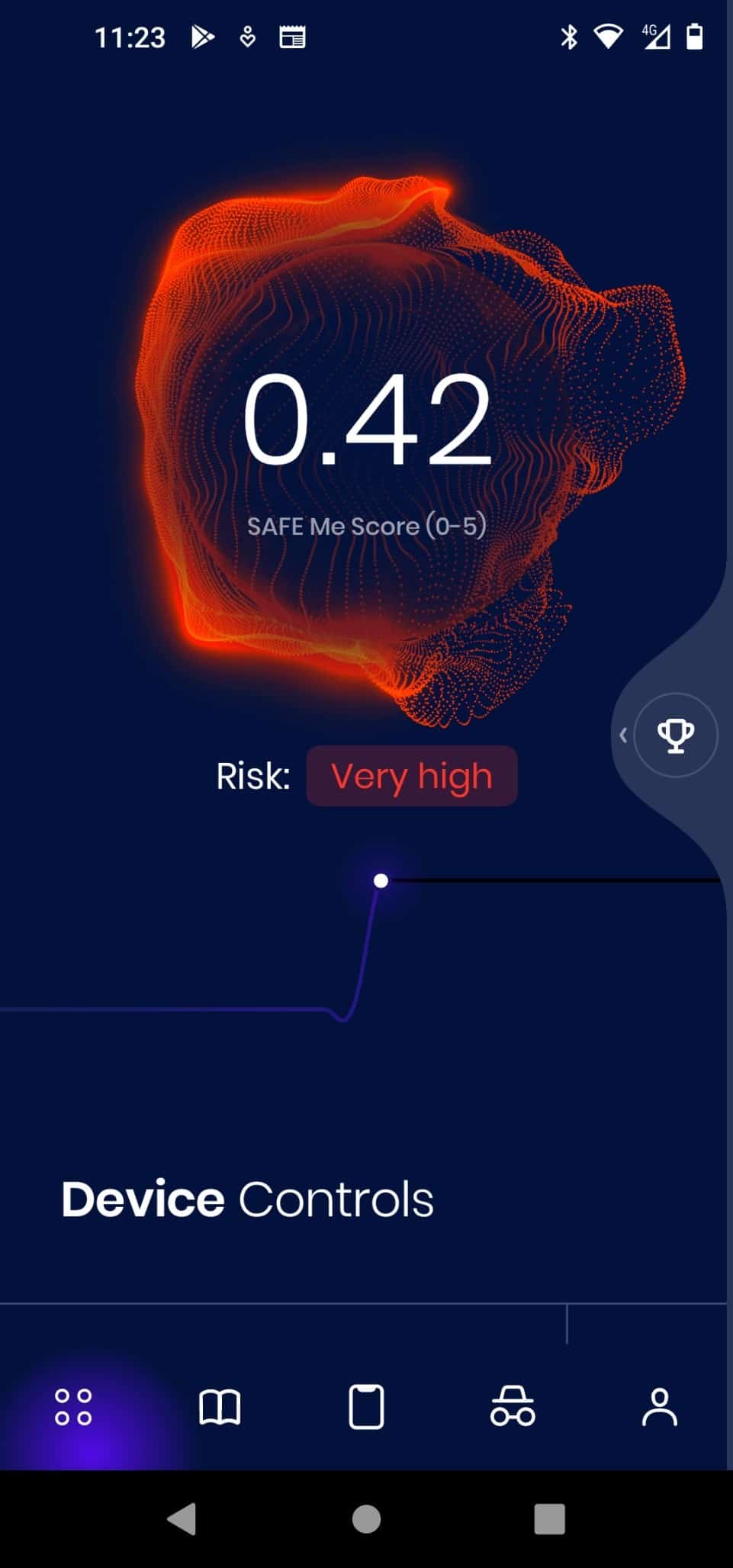
Free app helps consumers understand and reduce their cyber risk
Cybercrime is a major concern and many people worry about the threat of their personal data being stolen, leading to identity theft.
A new free app from cybersecurity and digital business risk quantification specialist Lucideus aims to fundamentally change the way consumers secure and protect their digital lives.

Get 'Mastering Linux Security and Hardening -- Second Edition' ($31.99 value) FREE for a limited time
From creating networks and servers to automating the entire working environment, Linux has been extremely popular with system administrators for the last couple of decades. However, security has always been a major concern.
With limited resources available in the Linux security domain, this book will be an invaluable guide in helping you get your Linux systems properly secured.

Secureworks delivers businesses an alternative to SIEM
In the face of rising threat levels many businesses have turned to security information and events management (SIEM), but it isn't the right approach for all.
Software-driven security specialist Secureworks is offering an alternative with improvements to its Threat Detection and Response (TDR) product. It allows security operations teams to detect, investigate and respond to security incidents.

Malwarebytes expands business protection for remote workers
Malwarebytes has announced updates to its business protection suite and industry partnerships which incorporate more features to help secure remote workers.
New product features include the addition of Malwarebytes Brute Force Protection and Malwarebytes' next-generation scan and detection engine. The company has also announced a partnership with cyber insurance provider, Coalition to offer a combined solution of endpoint security and cyber insurance to protect organizations from cyberthreats.

Regular tech updates are a key factor in security success
Security teams that proactively refresh their technology regularly have then most success in fending off threats according to a new report from Cisco.
On average, programs that include a proactive, best-of-breed tech refresh strategy are 12.7 percent more likely to report overall security success. However, not all organizations have the budget or expertise to make this happen, but a strategy to migrate to cloud and SaaS security solutions can help.

Parcel delivery phishing scams up 400 percent in November
Researchers at Check Point have seen a 400 percent increase in phishing scams using DHL, Amazon and FedEx branding to try to get people to part with information during the peak online shopping period.
Two weeks ago, Check Point researchers documented an 80 percent increase in malicious phishing campaigns targeting online shoppers with 'special offers.' The latest spike uses subject lines like 'track your shipment' and 'delivery problem.'

Users underestimate level of attacks on home networks
Internet users in the US vastly underestimate how often their home networks are targeted by cyber threats according to a new report from Comcast.
The first Xfinity Cyber Health Report combines data from a new consumer survey with threat data collected by the xFi Advanced Security platform and finds 95 percent of survey respondents underestimate the volume of attacks they face each month.

Zero trust access, VPN, both? The changing face of remote network access [Q&A]
Virtual private network (VPN), software defined perimeter (SDP), zero trust network access (ZTNA), there are plenty of technologies around for protecting remote access to enterprise networks.
This is an area that's been thrown into sharper focus this year, but what's the best option for keeping remote access secure? We spoke to Scott Gordon, CISSP for Pulse Secure to discuss the value of the different options available.

Employees' home networks could lead to SMEs failing security assessments
With the pandemic forcing more people to work from home, businesses in the UK -- particularly smaller ones -- may not have considered the fact that their employees' home networks now fall under the scope of regulatory and certification requirements.
According to a report from support solutions company A&O IT Group, if an individual works from home more than half of their time, their network must be compliant with current regulations.

How the banking sector is adapting to security and regulatory requirements [Q&A]
Banks and other financial services institutions have been moving more and more towards digital in order to streamline processes and improve customer service.
The pandemic has accelerated this process but has also brought a rise in cyberattacks. Regulators have also begun to take more notice of security practices surrounding accounts. We spoke to Michael Magrath, director, global regulations and standards, at specialist in anti-fraud and digital identity solutions for financial institutions OneSpan, to discover more.

If you're still using Windows 7, you need to install this important, free 0-day patch
Windows 7 may be rather long in the tooth, but there are still millions of people using it globally. And just because the operating system has been around for years, that does not mean all of the bugs and security issues have been ironed out; far from it, in fact.
Earlier this month a security researcher discovered a local privilege escalation vulnerability in both Windows 7 and Windows Server 2008 R2. There's no indication that Microsoft will issue a patch even for organizations the paid for extended support, but the vast majority of Windows 7 users will be left vulnerable. Or at least that would be case if it wasn't for 0patch stepping up to the plate and making a micropatch available for free.

Pirated data risks: Remote teams need to become a first line of defense
The increasing number of news headlines that mention data piracy, theft and database hacking makes it clear that businesses need to treat data as a valuable asset. This is especially true of businesses with teams that work remotely, as these set-ups usually have fewer security protocols.
Most remote workers are working from their homes, and unless those team members are conscious of cybersecurity, they’re not likely to have intrusion detection systems and firewalls on their personal networks.

More than 5,000 Black Friday-related scam sites registered in November
While the holiday season is a peak time for retailers, it also represents an opportunity for cybercriminals. This is particularly true of 2020 when more people than ever are likely to be shopping online.
Research from Comparitech analyzed around 30 million websites registered this month to identify efforts by cybercriminals to trick consumers looking for holiday shopping deals.
