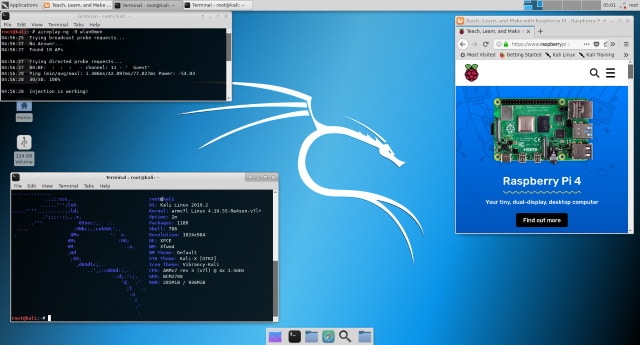
Kali Linux arrives on Raspberry Pi 4
Offensive Security has released Kali Linux for Raspberry Pi 4.
The new build of the security-focused distro comes just two weeks after the launch of the Raspberry Pi 4, the most powerful version of the mini-computer yet. Offensive Security says that the new build takes advantage of everything the Pi 4 has to offer.

Ubuntu-maker Canonical's GitHub account hacked
Canonical -- the company behind the Ubuntu Linux distro -- is investigating an attack on its GitHub account over the weekend.
On Saturday, hackers were able to break into Canonical's GitHub account and create a number of new repositories. Named CAN_GOT_HAXXD, the eleven repositories were empty and have now been removed. Canonical says that no source code was accessed, but it is not yet known who carried out the attack.

Companies turn to instant messaging in response to rising email threats
In a new study of IT decision makers by Barracuda Network, 94 percent of participants admit that email is still the most vulnerable part of their organization's cyber security.
The survey of 280 decision makers focused on the email threat landscape and email security practises. It discovered that 75 percent have been hit with brand impersonation emails, the largest threat as identified in the survey with ransomware coming in second on 47 percent.

Microsoft launches Threat and Vulnerability Management for enterprises
Scheduled vulnerability scanning can leave blind spots between scans leaving organizations vulnerable.
In response to this problem, Microsoft has partnered with a number of enterprise customers to create a new Threat and Vulnerability Management solution as a built-in feature of Microsoft Defender Advanced Threat Protection.

EA fixes a 'chain of vulnerabilities' that could have put millions of Origin gamers at risk
EA has fixed a series of security issues on its Origin gaming service which could have been exploited by attackers to take control of user accounts and gain access to personal data.
EA Origin's security flaws meant that more than 300 million gamers were put at risk. Israeli security firms Check Point said that attackers could take advantage of a "chain of vulnerabilities" to attack players of games such as FIFA, Maden NFL, NBA Live, UFC, The Sims, Battlefield, Command and Conquer, and Medal of Honor.

5 tips to improve your company's IT security
According to a 2018 IBM study, the average cost of a data breach for a U.S. company is $7.91 million, while the average cost of a lost or stolen record that contains sensitive or confidential information is $148. Unfortunately, these figures are only rising.
Cyber attacks continue to not only cost companies more money but have also grown larger and more aggressive because of how profitable cybercrime has become. Despite the ongoing advances in IT security, threats continue to emerge just as fast as security measures evolve. Though cybercriminals will continue to find new, creative ways to gain access to business data, there are simple tactics you can implement to better protect your company.

Do mobile operating systems provide enough protection against cyber threats?
Every year a new iPhone hits the market and there are thousands of different Android devices in circulation. Both Apple and Google are constantly adding new features and functions to incorporate emerging technologies, maintain competitiveness, and cement their reputations as innovators.
Commercial focus typically sits with the clamor of more surface-level, UI related features like Memojis, Group FaceTime, gesture navigation, the features that consumers are drawn to rather than the patching of CVE-2018-4249. It’s all a matter of priorities, people want a device with all the mod cons, a mobile device just needs to be secure enough, meeting minimum expectations. It also doesn’t help that there has been a long held misconception that mobile OSs are secure enough and users don’t need a security solution. Despite mobile OSs becoming relatively hardened, usage is very different compared to traditional form factors, and there are a number of threat vectors that an OS can’t protect against.
Millions of Microsoft Excel users vulnerable to remote DDE attack as new exploit is discovered
Security researchers from Mimecast Threat Center have discovered an Excel exploit that could leave 120 million users vulnerable to attack.
The security flaw means that it is possible to use Excel's Power Query tool to dynamically launch a remote Dynamic Data Exchange (DDE) attack on a spreadsheet and actively control the payload. The researchers also found that Power Query could be used to embed malicious code in a data source and spread malware.

Is Google Safe Browsing falling short on mobile?
Google has a pretty good record when it comes to protecting its users against online threats. Part of this is its Safe Browsing technology which scans billions of URLs each day to discover dangerous websites.
But research by mobile threat defense specialist Wandera has discovered a disparity between the protections available within Google’s desktop browser compared to its mobile browser.

New offering gives enterprises greater flexibility in security training
Cybersecurity is often as much about people as it is about technology. But despite increasing their spending, organizations are still struggling to close the cybersecurity skills gap.
Training and certification company Offensive Security is launching a new program for enterprises designed to simplify the cybersecurity training process and allow organizations to invest more in cybersecurity skills development.

Major vulnerability found in EA's Origin gaming client
Researchers at Check Point working with CyberInt have uncovered a chain of vulnerabilities in the Origin gaming client developed by Electronic Arts (EA). If exploited, the vulnerabilities could have led to player account takeover and identity theft.
Researchers have responsibly disclosed the vulnerabilities to EA, in accordance with coordinated vulnerability disclosure practices, to fix the vulnerabilities and roll out an update before threat actors could exploit the flaw.

Sumo Logic launches threat benchmarking for AWS
As more and more apps and data move to the cloud, identifying and ranking threats becomes an increasingly difficult task.
Machine data analytics platform Sumo Logic is launching a new Global Intelligence Service for Amazon GuardDuty that delivers almost real-time actionable insights to allow customers to benchmark themselves against other adopters of Amazon Web Services cloud infrastructure, strengthen cloud security posture, improve threat detection, and enhance regulatory compliance.

Cloud identity solution lets developers deliver passwordless login and MFA
Identity specialist Ping identity is announcing an update to its PingOne for Customers IDaaS solution that means developers can now deliver passwordless and advanced multi-factor authentication from custom mobile applications.
Enhancements include a mobile SDK that allows development teams to send push notifications to custom mobile applications for MFA, APIs for logins via social media accounts, and support for single sign-on via Security Assertion Markup Language (SAML).

Carbon Black adds Linux support and more to its endpoint protection solution
Endpoint protection company Carbon Black is adding a number of features to its platform, including Linux support and Amazon Web Services and container protection.
The cloud-native platform gives security and IT teams remote access to cloud workloads and containers running in their environment, making it easier to resolve configuration drift, address vulnerabilities in real time, confidently respond to incidents and demonstrate compliance with business policies and industry regulations.

Impersonation attacks focus on payroll and supply chain
Impersonating a company's CEO or other senior executive has become a favorite technique for cybercriminals seeking to extract payments from businesses.
Historically this has been aimed at accounts payable departments, but the latest email threat report from FireEye shows attackers using two new variants to target payroll and supply chains.
