
Carpet bomb DDoS attacks rise 300 percent
A new report shows that 2022 saw a 300 percent increase in 'carpet bomb' DDoS attacks compared to 2021. Carpet bomb attacks, also known as spread-spectrum or spray attacks, distribute traffic across large IP address spaces.
Legacy technology, like standard victim-oriented detection and mitigation detection techniques, often fails to accurately identify these attacks, leading to incomplete mitigation or false positives. Legacy solutions can also simply be overwhelmed by the number of IP addresses involved.

Why automation can help continuously validate security policies [Q&A]
Security professionals all know that they should test their security hardware and software periodically to make sure it's working as intended. Many normal IT activities have unintended consequences that cause security configurations to 'drift' over time and make the organization more vulnerable.
But testing is frequently postponed or ignored because it never becomes a high enough priority. We spoke to Song Pang, SVP of engineering at NetBrain, to find out how automation can be used to detect when security products or network traffic are no longer behaving as intended.
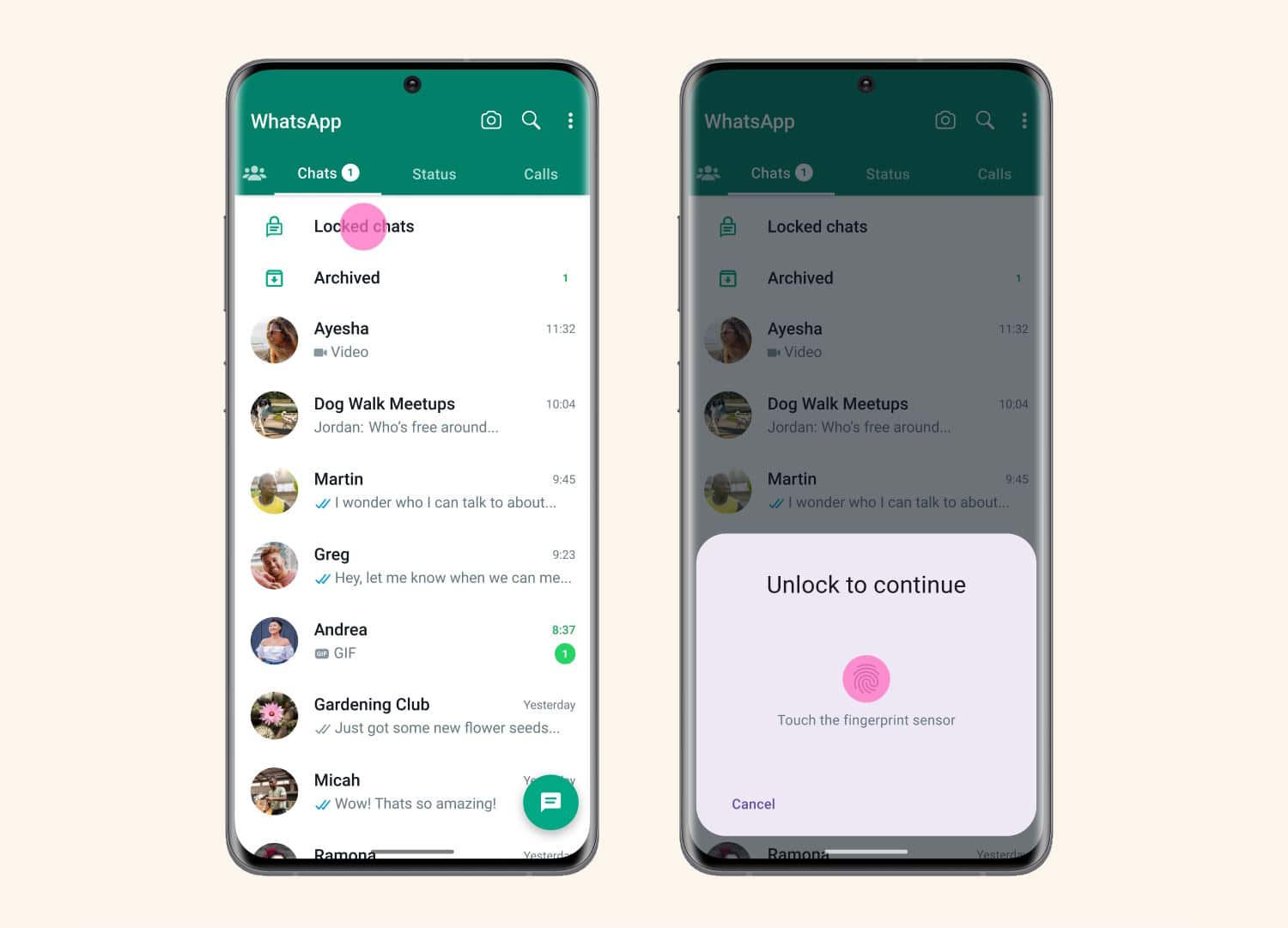
WhatsApp introduces Chat Lock to protect sensitive messages
WhatsApp has long been one of the more secure messaging apps with mass appeal, largely thanks to end-to-end encryption. This has been boosted further by features such as disappearing messages, and now Meta has added Chat Lock.
The company says that the feature "lets you protect your most intimate conversations behind one more layer of security"; what this means in practice is that message can be password or fingerprint protected. But there is more to Chat Lock than this.
Microsoft is able to look inside your password protected zip files
Microsoft has been spotted scanning for malware within password protected zip files stored on its cloud services.
Security researcher Andrew Brandt was among those to notice that Microsoft appears to be bypassing passwords added to zip archives in order to check for malware. While the intentions of the company may be good, the practice raises serious questions about privacy and security.

How likely are you to be a victim of identity theft?
It's human nature to have an, 'it can't happen to me' approach to life's mishaps, whether it's being involved in a traffic accident or falling victim to cybercrime.
But of course these things do happen to someone. When it comes to identity theft, Home Security Heroes has taken a more scientific approach to determining how likely you really are to become a victim.

Is this the year we take quantum threats seriously? [Q&A]
Quantum computing is something that seems to have been hovering just out of reach for a decade or so -- in fact research into the concept first began back in the 1980s.
More recently quantum has come closer to a commercial reality, with big players like IBM publishing a road map with a clear, detailed plan to scale quantum processors and build the hardware necessary to take advantage of the technology and other big players like Google, Amazon, and Microsoft having since followed suit.

Brave is gaining 'Forgetful Browsing' to dramatically improve online privacy protection
Web browser Brave has long had a focus on privacy, making it the browser of choice for those with concerns about online tracking and the like. Although Brave may be regarded as one of the most private browsers available, its developers continue to work on new innovations; the latest is Forgetful Browsing.
This new feature makes it possible to always clear cookies and other storage when a site is closed, helping to eliminate the potential for tracking and bringing other benefits. Forgetful Browsing can be enabled on a site-by-site basis, or applied across the board, and it prevents sites from using trackers to identify you, bypasses article viewing limits, and ensures that you are logged out of sites when you leave them.

Three lesser-known endpoint vulnerability strategies you might be missing
Modern IT environments continue to become more and more distributed, driving the growth of endpoints across the enterprise. Some research estimates that enterprises now manage more than 135,000 endpoints and Enterprise Strategy Group estimates that more than 70 percent of employees use more than four devices daily for work. That’s a lot of endpoints. And when you combine this endpoint growth with the fact that 560,000 new pieces of malware are detected every day, how can you not wonder if your organizations is the next target for a ransomware or phishing attack.
Security pros are overwhelmed by endpoints and struggle to find the right mix of solutions and strategies that can effectively secure their organizations. The more diverse they are, the more difficult they are to manage and secure (especially with mobile and IoT device proliferation). Just look at recent attacks against Twitter, Slack, Taco Bell, and more. For many organizations, endpoint security is really hard. This is why their security teams need to constantly assess and adjust their endpoint security strategies.

Safety in the metaverse: What are the risks for businesses?
Like any new innovation, the metaverse is currently at the center of a 'risk versus reward' debate. Unsurprisingly, the 3D virtual world has received a lot of attention, with McKinsey confirming that more than $120 billion was invested in building out metaverse technology and infrastructure in the first five months of 2022.
Promises of extraordinary use cases, from teaching virtualized university lectures to performing surgeries for patients in other countries -- not to mention the potential cost saving and accessibility benefits -- have garnered curiosity. But while it could be some time until we see mass adoption of the metaverse, the security community is already apprehensive of the evolving security risks.

Business leaders don't understand cybersecurity
A new survey from Delinea of over 2,000 IT security decision makers (ITSDMs) reveals that only 39 percent of respondents think their company's leadership has a sound understanding of cybersecurity's role as a business enabler.
In addition, over a third (36 percent) believe that it is considered important only in terms of compliance and regulatory demands, while 17 percent say it isn't seen as a business priority.

Cybersecurity awareness education: The beginnings of change
More than eight in 10 data breaches globally can be attributed to human error.
People are the weakest link in cybersecurity. And this weakness comes from a lack of awareness about our cyber risk and the behaviors that influence it. Many people see cybersecurity as an IT concern. In truth, cybersecurity concerns everyone. When our hospitals get infected with ransomware, we can’t receive care. When our organizations experience a cyberattack, we lose our jobs. Still, we tend to underestimate the importance of cybersecurity to our society and economy.

Twitter admits a 'security incident' allowed private Circles messages to be seen by anyone
Following numerous complaints from users concerned that the Circles feature of Twitter was broken, the company has conceded that tweets that were supposed to be visible to only a select number of people were in fact accessible by anyone.
The idea of Twitter Circles is that messages can be seen only by people who have been added to a Circle. But Twitter has now revealed "a security incident that occurred earlier this year" that ignored privacy settings.

From details to big picture: Five approaches to improve security
Improving your organization’s cyber security posture is essential to maintain brand trust. The challenge for the C-suite is to look at both the big picture and the finite details, translating your overall strategy for managing risk into actionable processes and priorities that will, over time, lower your risk exposure.
Qualys’ Threat Research Unit (TRU) looked at trillions of anonymized data points gathered from across our customer base to analyze where the biggest risk areas were for businesses. Based on this data, we can see specific areas where you can help your team increase their performance effectiveness, as well as how these changes add up to a significant improvement in security results overall. Building on these details will improve how you manage risk, reduce your attack surface and maintain trust with your customers.

Cybersecurity teams are overconfident of their ability to deal with threats
A study from Immersive Labs finds that while businesses have high confidence in their overall resilience, teams are insufficiently prepared for threats.
The study, carried out by Forrester, surveyed 316 global cybersecurity training strategy decision-makers in the UK, US, Canada, Germany, and Sweden, finds that 82 percent agree they could have mitigated some to all of the damage of their most significant cyber incident in the last year if they were better prepared.

Don't get stuck in a honeypot
Honeypots have been around for years and are a tried and tested cybersecurity mechanism. By creating a fake environment with attractive assets, organizations use honeypots to lure attackers into a trap where their actions can be studied and learned from to improve cybersecurity measures. Simultaneously, they are protecting the business’ real assets by preoccupying the attacker with the decoys.
However, honeypots have a narrow field of view as the only activity that they detect is those that target them directly. If an attacker gains access to a network, but not through the honeypot, the business would be none the wiser. It is, therefore, crucial to have more than one honeypot -- a honeynet -- to make it effective. Yet, honeypots are very time-consuming to apply as they need to be installed in networks and systems in data centers. It can take as long as an hour to install just one and it lacks any level of scalability.
