
Chameleon phishing attack brings bad karma to email users
New research by Trustwave SpiderLabs has uncovered a phishing attack that is able to adapt itself to the user's email service in order to trick them into revealing their login credentials.
The attack acts like a chameleon, putting up a fake login page tailored for whatever email service the victim is using. So Gmail users for example will see a different page from Apple, Outlook or Yahoo! Mail users.

Linux and Raspberry Pi machines become top targets for credential hacking
New research shows that hackers are regularly gaining access to servers with the same commonly used -- often default -- passwords.
The data from Bulletproof also reveals that default Raspberry Pi usernames and logins feature prominently on the list of top default credentials used by hackers.

Hard truths from Ukraine: The government cannot save us in cyberwar
Amid our first global, multilateral, wholly unpredictable cyberwar, it is up to each of us to defend ourselves. No intelligence agency is certain how the cyber dimension of the Ukraine conflict will evolve; no military can stop a cyberattack. The situation catapults every digital organization into unknown territory.
If you think the battles on air, land and sea so far have defied expectations, consider the parallel cyber conflict. Three sober truths make this a perilous moment for us all -- especially as the Russian army’s logistical setbacks may make heightened cyber aggression against private interests more enticing.

1Password launches new tools to help developers build secure software
Generating, managing and accessing secrets within development workflows can be a complex process and lead to the inadvertent introduction of risks.
Security and privacy specialist 1Password is launching a new set of developer tools that aim to simplify complex processes and improve security practices to ensure data is protected, without slowing down the development pipeline. This will also provide developers with secure access to the secrets they need wherever they are.

Ukraine conflict puts organizations’ cyber-resilience to the test
Russia’s invasion of Ukraine has provoked a massive rally of hackers to join both sides of the conflict and take up arms in the cyber-war. As has been the case in cyberattacks of recent years, the consequences of this will affect organizations way beyond the initial intended target. For example, in June 2017 French company Saint-Gobain was forced to halt its operations as a result of the NotPetya attack, a Russian cyberattack targeting Ukraine that resulted in over €80 million of losses in company revenue.
As a result of a sharp increase of cyber-attacks since the beginning of the conflict, from DDoS, new data wipers, phishing campaigns and malware, organizations worldwide should take immediate action to improve their cyber-resilience and limit the damages that any spillover could have on their business.

Cloud security tool sprawl leads to missed issues, false positives, burnout and more
A new survey of more than 800 IT professionals finds that 55 percent of respondents are using three or more cloud providers and 57 percent have five or more cloud security tools.
But the study from Orca Security shows this combination of multi-cloud adoption and disparate tooling is overwhelming security teams with inaccurate alerts. For example, 59 percent of respondents receive more than 500 public cloud security alerts a day, and 38 percent receive more than 1,000 a day.

Cyberwarfare plays growing role in the Russia-Ukraine conflict
As we reported last week, cyberattacks are being used on both sides of the Russia-Ukraine conflict. Two new reports out today take a deeper look at how the cyber aspect of the conflict is developing.
Accenture's Cyber Threat Intelligence team has been looking at how threat actors have been dividing along ideological lines. Meanwhile Aqua Security's Team Nautilus has been analyzing the cloud technologies used in the conflict.

Do traditional antivirus solutions still have a role in the age of AI? [Q&A]
Antivirus software was one of the earliest cybersecurity solutions, with the first commercial programs appearing in the 1980s, and it remains at the core of protecting computer systems today.
But as threats evolve and become more sophisticated, does traditional antivirus still have a role to play or will it be overtaken by technologies like artificial intelligence?

Web application attacks soar as attackers get more professional
The number of malicious web application requests grew 88 percent between 2020 and 2021, with broken access control and injection attacks making up over 75 percent of them.
The latest threat analysis report from Radware shows the most attacked industries were banking and finance, along with SaaS providers, together accounting for more than 28 percent of web application attacks.

Almost 90 percent of cyberattacks in March targeted against Russia and Ukraine
We're used to a high volume of cyberattacks originating from Russia, but in an interesting turnaround following the invasion of Ukraine, 70 percent of cyberattacks in March have been targeted at Russia.
Research from Atlas VPN shows a further 19 percent of attacks targeting Ukraine. The USA is the third biggest target but attacks targeting the country accounted for only five percent of the total.
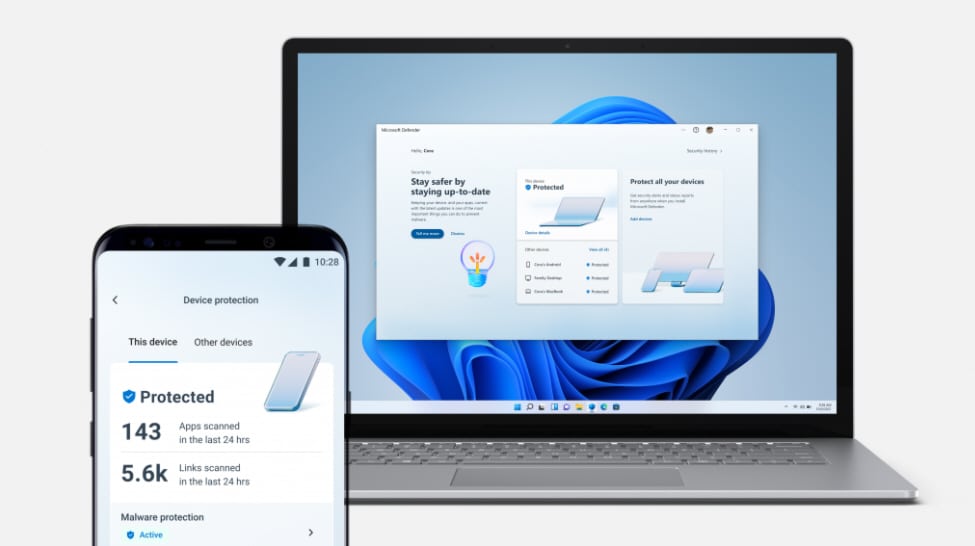
New Microsoft Defender preview now available for Windows, Android and iOS
Microsoft has been working on a new security tool for a while now and today announces a preview build for Windows Insiders to try out, although there are some restrictions to be aware of.
The Microsoft Defender app, which is available for Windows, Android, and iOS, helps protect you and your family’s data and devices against online threats, such as malware and phishing attacks.

Beware the three percent -- tiny proportion of users account for most malware incidents
A new report and infographic released today by Elevate Security shows that a mere three percent of a company's internal users are to blame for 92 percent of malware incidents, while just four percent are responsible for 80 percent of phishing incidents.
The research, carried out for Elevate by the Cyentia Institute, also shows 12 percent of users are responsible for 71 percent of browsing incidents with one percent triggering 200 events every week.

Don't panic! Knowledge, skill and judgment are key to cybersecurity responses
Humans are often the weak link in the cybersecurity chain, but it's human capabilities that are also key to dealing with attacks and their aftermath, according to a new report from Immersive Labs.
The inaugural Cyber Workforce Benchmark report analyzed cyber knowledge, skills and judgment from over half a million exercises and simulations run by more than 2,100 organizations over the last 18 months.

Majority of attacks on SaaS platforms come from Russia and China
Analysis of security events across more than 120,000 user accounts last year shows that the vast majority of attacks on top SaaS platforms such as Microsoft 365, Google Workspace, Slack and Dropbox are coming from Russia and China.
The latest SaaS Application Security Insights (SASI) Report from SaaS Alerts also suggests these countries may be coordinating attack efforts. Attack trend lines that compare Russia and China show almost exactly the same pattern.

Bitdefender launches new password manager for consumers
We all know that we should use complex passwords and different ones for each account but managing them is undoubtedly a chore. It's no surprise then that Bitdefender research shows 50 percent of people use a single password for all online accounts and 32 percent reuse just a few passwords across multiple accounts.
To simplify the creation and management of secure passwords for online accounts across multiple platforms, including mobile, Bitdefender is today launching its own Password Manager.
