LulzSec hack reveals secret tech used by drug cartels
LulzSec's theft and disclosure of "law enforcement sensitive" documents and personal information from the Arizona Dept. of Public Safety has caused quite an uproar over privacy and security, but it has also provided a glimpse into crime in the American Southwest, where cross-border drug trafficking is a major concern. For us, It has provided a look into the impact consumer technology has had on the criminal underworld in the last three years.
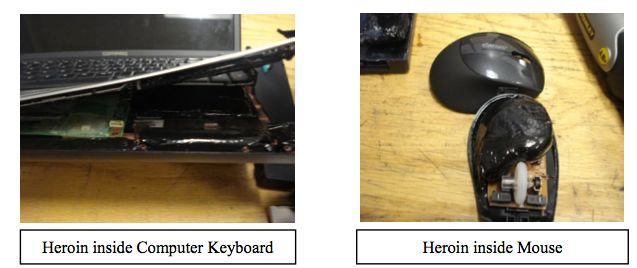
1. Laptop Drug Mule -- According to an intelligence bulletin from the El Paso Intelligence Center (EPIC), a passenger flying on Copa Airlines from Colombia to New York in March was caught with 1.6 kilos of heroin smuggled inside an HP laptop, mouse, external hard drive, ipod speakers, digital picture frame and mp3 player.
2. GPS Tracking Bugs -- A Situational Awareness Bulletin from the Arizona Counterterrorism Information Center warned that drug trafficking organizations were using GPS tracking devices on their rivals to set up home invasions and raids. The bulletin also warned that when vehicles are seized, they should be swept for commercially available tracking bugs so the status of the impounded vehicle is no longer trackable.

3. Home-made Tanks -- A June 15th bulletin from the City of Phoenix Homeland defense bureau warned of so-called "Narco Tanks," armored consumer trucks with swiveling turrets, snipers' peepholes and "gadgets to dump oil and scatter tire-puncturing nails on roadways." Two vehicles plated in inch-thick armor were discovered in Ciudad Camargo in Tamaulipas, not far from the Texas border.

4. Social Networking to broaden gang influence -- A 2009 report from the McAllen Intelligence Center in South Texas outlined the many ways regional gangs were using social networking sites like Facebook and Twitter to grow bigger than they'd been in the pre-internet era.
Gangs display their affiliation via the internet; youth gangs are no longer only in conflict with a rival gang from the same town or where their turfs connect. Social websites provide the primary means for gangs from different cities across the Rio Grande Valley to widen their area of operation. What results is gangs that would ordinarily not be competing with one another because of their geographic location, they are now competing through the Internet.
5. Social Networking to overturn an Officer's credibility in court -- A bulletin from the Washington Regional Threat and Analysis Center warned police officers of the "perils of social networking" and that their conduct on sites like Facebook has a direct impact upon their police work. The bulletin cited cases where a police officer's own web presence was used against him.
Convictions rest on the credibility of the officer(s). The defense strategy was to show the jury that what the officer writes about himself on social network websites is how he "really" conducts police work. The suspect in this case claimed that the officer used excessive force on him and broke three ribs…The officer in this case had made questionable social network postings but claimed it was simply bravado, similar to what might be said in a locker room. But the difference between jokingly "talkin' trash" in person and posting it on the Internet is that postings are preserved indefinitely on a digital server.
6. Cop Camouflage -- In gang-on-gang raids, gangs often try to look like cops to fool other gangs or to confuse or arouse less suspicion from civilians. LulzSec's dump brings up many instances of gangs and drug traffickers who buy law enforcement gear online and use it to disguise themselves.
7. YouTube -- In a bulletin entitled "Crown Vic Issue," it is warned that a video was circulating on YouTube and other video sites that explained how to break into the trunk of a locked Police Crown Victoria without setting off the alarm, for the sole purpose of stealing weapons, radios, body armor and so forth. Also included in the LulzSec dump was a police report of two 17-year old kids who had used that very technique to steal a policeman's gear from his car as it was parked in front of his own house.
8. Dummy cell phone weapons -- Calibrepress, a website that tracks concealed or unusual weapons posted a report that showed a commercially available 180,000 volt cell phone stun gun and a .22 caliber pistol that can be broken down to fit inside a gutted cell phone. The pistol had not yet been seen in the US, but Calibrepress said it expected it to hit the states "shortly."

The guns are loaded by twisting the phone in half. The rounds fit into the top of the phone under the readout screen and the lower half, under the keyboard, holds the firing pins. The bullets fire through the antenna by pressing the keypad from numbers 5 to 8.
9. Cell phone "kill pills" -- A Department of Justice cybercrime awareness entitled "Find My Phone" warned that the ability to remotely wipe a cell phone of its contents is not only beneficial to consumers who have had their phone stolen, but also to criminals whose phones have been claimed as evidence.
The ease of restoring an iPhone to it's (sic) last backup condition may encourage users who's (sic) phones have been temporarily seized by law enforcement to wipe all data to prevent law enforcement from gaining access to it… Law enforcement and the courts should be made aware of the potentially exigent circumstances that have been created by this remote wiping feature that requires rapid actions to be taken to safeguarding and or image iPhones encountered during criminal investigations to prevent the loss of valuable evidence or investigative information.