ZoneAlarm Pro misidentifies Yahoo Messenger as a Trojan...again
It's getting more difficult to keep track of the various stages and permutations of malware, whose definition has expanded to mean "anything you didn't ask for and don't want running." But since when did Yahoo IM become malware?
It's no secret that a lot of our Windows-based production systems, and even some of our virtual ones, run ZoneAlarm Pro. There are a lot of software-based firewalls available now, but for the most part, we've been able to trust ZoneAlarm, even now that its originators have been absorbed into Check Point Software Technologies.
True, we've had bits and pieces of trouble with ZoneAlarm over the years, most notably its strange inability to correctly identify the auto-updating agent in Sophos Anti-Virus, and to lock it out from Internet access instead. Yesterday, we noticed ZoneAlarm Pro's anti-malware scanner detecting what appeared to be a Trojan, on a system we usually trust to be quite clean. ZAP identified it as a known piece of malware dubbed Win32.Trojan.Yspy.
The Detail breakdown identifies the file in question as yacscom.dll, installed in the Yahoo Messenger directory. Indeed, the file is actually part of Yahoo Messenger itself -- specifically, the audio conferencing ActiveX control for the IM client, a critical component. In BetaNews tests, we noted ZoneAlarm Pro identified that ActiveX control library for version 7 and version 8.1 of Yahoo Messenger.
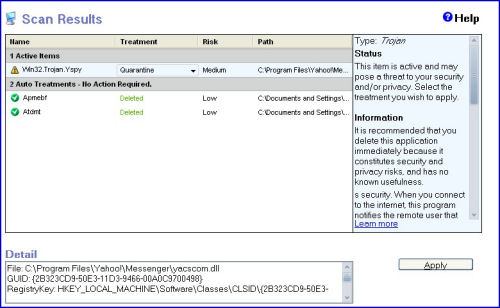
In an ongoing thread on Check Point's malware discussion board, ZoneAlarm Pro users are also noticing what they are coming to recognize as a "false positive." One user reports having noticed this behavior at least once before, perhaps exactly one year ago, with regard to the same two products.
Meanwhile, other security vendors are cataloguing yacscom.dll as malware, most likely because ZoneAlarm Pro already does.
Curiously though, a question posed by a user to one of Yahoo's own message threads was responded to by a regular contributor who wrote, "False-positive detections are the anti-malware industry's dirty little secret. They happen a lot."
But the contributor went on to suggest that, rather than have ZoneAlarm Pro delete the suspect file automatically, the user should instead have kept the file under quarantine, submitted the filename to Check Point for further analysis, and then deleted it after a few months if he didn't notice anything peculiar. The contributor may have been interested to know the file belongs to the company to which he contributes.