Can malware detect that it's running in your sandbox?
If you think an application is suspicious, then you might run it in a sandbox, a virtual machine, maybe use a debugger, and watch what it does. And if nothing happens then that means it’s safe. Right?
Well, maybe not. Malware will often try to detect this kind of trickery, and if it thinks it’s being watched, won’t do anything to raise an alarm.
Paranoid Fish is a tiny open-source tool which uses various techniques to detect sandboxes, VMs, debuggers and more. Run it in your testing environment and you’ll get a feel for how transparent it really is.
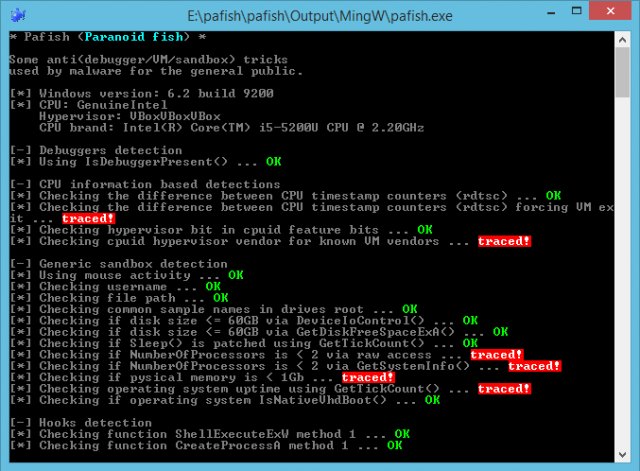
Double-click pafish.exe, the program opens a command window and begins running its tests. These can sometimes take a while -- it may appear to hang for three or four minutes -- but the individual test names and results are displayed as the program works.
Although it’s aimed at experts, many of these tests are easy for experienced users to understand. The program looks for VMware Registry keys and adapters, VirtualBox windows and network shares, and uses simple generic ideas like checking whether the system has a single processor, less than 1GB RAM, or a hard drive of under 60GB.
If you’ve not thought about this before, just browsing these tests may give you some ideas. Like, if you’re creating a VM to test suspicious programs, give it as many CPUs and as much RAM/ hard drive space as you can spare.
Other test names are either vague ("Checking file path") or experts-only ("Checking function ShellExecuteExW method 1"), but ignore them -- you don’t have to understand every detail.
All that really matters is the verdict after each test. A green "OK" mean the program hasn’t detected any anti-malware tricks, but a red "traced" means it’s spotted your monitoring. And malware could, too.
Paranoid Fish is a free application for Windows XP and later.
