How automation will impact education

There has been a lot of hype around how new technologies like automation will impact our way of life. Some live in fear that their jobs will be lost to humanoid robots, while others excitedly welcome bots like Amazon Alexa into their home. The impact of 'robots' -- itself an ill-defined category -- is widely discussed and hotly contested.
In the business world, most industries have much to gain from automation and robotics, but what this looks like in practice is a far cry from the wider speculation.
IT and the rise of connected cars

Volkswagen recently revealed that it is exploring using an innovative form of distributed-ledger (i.e., blockchain) technology called the IOTA "Tangle" to deliver software updates to its autonomous cars. The technology may be available to customers as early as Spring 2019. It’s just the latest in a seemingly unending stream of news about connected cars, a broad term that encompasses everything from cars with built-in GPS systems to fully autonomous, AI-driven semi trucks in the emergent IoT space.
While the topics of conversation are spanning everything from legislation to programming ethics, not enough air-time has been devoted to discussing exactly how the arrival of this new technology will change the charter for the IT teams who will be tasked with supporting the future of transportation.
Advanced SystemCare 12 includes a new privacy shield

Should you keep your system optimized or simply allow Windows to keep your computer in-check? A few years ago, data would build, junk would collate and it was relatively easy to cause a blue screen of death or even stop Windows from booting at all, requiring a system restore.
These days Windows 10 is far better engineered and will do a good job keeping your system maintained. With this in mind, system maintenance suites are turning their hand to security, adding features to enable you to keep yourself safe and secure whilst you browse the internet (although your security software should be more than capable…).
TeamViewer 14 Preview is here with new augmented reality Pilot mode

We handle support for novice computer users and you’ll be surprised how many of these customers do not understand the basics of computing. Sell them security software and many can’t install the new suite as they’ve never fully removed the previous one. So frustrating.
The easiest solution is to employ TeamViewer and remotely advise the user via their computer, that than either over the phone or by email. It’s quicker to perform a task yourself than guide someone, which has made the software a godsend for any remote support facility.
Flashback Friday: How two university dropouts created Microsoft

Bill Gates is a legendary figure, and not just in the world of technology. With countless awards and titles attached to his name, he has over the years been consistently recognized as one of the world's wealthiest, most powerful and most influential individuals. Also, anybody who can call themselves a 'philanthropist' in today's world has, more often than not, probably achieved something pretty grand.
However, back in the day, Gates was merely a university dropout with a thirst for hacking computer systems. True, the university was Harvard, but Gates wasn't exactly on course to becoming the multi-billionaire entrepreneur he is today.
Creating the next generation of cybersecurity leaders

In today’s cybersecurity landscape, the value of good cybersecurity tools is undeniable. What is more valuable are the people behind the tools -- however, the amount of open cybersecurity positions worldwide is growing year over year. Currently, there are more than 300,000 open cybersecurity roles in the U.S. alone, but by 2021, Cybersecurity Ventures expects that number will reach 3.5 million.
This gap is felt by cybersecurity leaders; in fact, a recent study found that more than 70 percent of the cybersecurity decision makers agree that their organizations do not have the staff or necessary resources to monitor all cybersecurity threats that their organizations face. With the number of cybersecurity openings growing yearly and the sophistication and frequency of cyberattacks increasing, in order to build the cybersecurity leaders of tomorrow, business leaders must turn their attention to things that they can control: investing in the right solutions and their staff.
Can the infosec community ever be as well-organized as digital criminals?
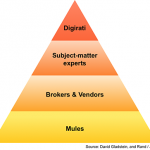
Brian Gladstein, a security marketing strategist at Carbon Black, discussed the question posed in this headline at RSA Conference 2018. In his presentation entitled "Endpoint Security and the Cloud: How to Apply Predictive Analytics and Big Data," Gladstein observes that digital crime is structured like an economy consisting of several tiers. At the top is the "Digirati," a term used by Gladstein for the class of high-ranking controllers responsible for executing digital attacks. The Digirati consists of the ones who hide on the network and gather information, usage patterns, and intel. They then share this information and build upon what knowledge they’ve already gathered from other actors in the online criminal community.
Below the Digirati are the subject matter experts. Malware writers, identity collectors, and individuals who hoard zero-day vulnerabilities and other exploits sit on this level of the digital crime economy. These individuals oftentimes sell access to their goods and services to the next tier, which consists of botnet owners, cashiers, spammers, and other brokers and vendors.
How voice search is changing the way we shop

Over the years, the way we interact with the world around us has changed considerably. Where once analog and physical interactions ruled, now we value digital, virtual and simulated experiences -- some of which bridge the gap between these worlds.
For example, buying goods online or through a mobile app and then picking them up at a local store is a cross-platform experience for the modern age.
Love Dynamic Desktop? Move up to 24 Hour Wallpaper

We’ve worked for years with potential eye strain and it’s only recently we’re taking it seriously. The first step was Apple adding a warmer edge to the desktop panel, so by the end of the day you wouldn’t be looking at an LCD displaying sharp blue light.
Mojave introduced Dynamic Desktop, which will transition your wallpaper, so it matches both the time of day, your location and the ever-changing sunrise/sunset. Dynamic Desktop will show a bright wallpaper middle of the day, but by 10pm you’ll be seeing a nighttime scene.
NightOwl is a must-have app for all Mojave users

Dark mode is a fantastic addition to any operating system, enabling late-night work to more productive. We have the theme switched on as default on Windows 10, which has always suited a darker user-interface.
Apple introduced a system-wide dark mode with Mojave and some of the recent apps look hugely better on a dark background. iPhoto is a very good example, making photos pop on the dark shade and editing easier on the eyes.
3 questions startup founders should ask about data privacy

Modern startups are awash in information, from real-time customer insights collected via mobile applications to employee data received through online portals.
Founders are constantly making decisions about where to invest, when to hire, how to hire and, most importantly, how to grow. In the rush to cultivate clients and consider business scalability, many startups may fail to truly appreciate the immense responsibility that comes with gathering and storing data in the current digital environment, a place where cybercriminals roam and users are painfully aware of the risks that come with sharing private information online.
Your future vacation: Brought to you by AI-assisted travel planning

Thirty years ago, those of us who wanted to go on vacation or just visit friends and family for a weekend had to go through a travel agent to make arrangements. Then came the internet, and with it the launch of online travel agencies like Orbitz and Expedia, which enabled customers to research, find, and book their own vacations for the first time. Soon after that, the emergence of new "sharing economy" companies like AirBnB and VRBO transformed the travel industry by leading customers to consider new destinations and accommodations outside of a traditional hotel -- or B&B. Given how the pace of transformation has accelerated, the travel planning industry is ripe for another major transition to AI (Artificial Intelligence)-assisted travel planning.
The rise of the sharing economy, combined with increased household net worth and persistently low airfares led to record summer travel, with more than a quarter of a billion travels -- the most in TSA history. Given how the pace of transformation has accelerated, the travel planning industry is ripe for another major transition to AI-assisted travel planning.
End-user performance monitoring in the cloud and multi-cloud era

Online shoppers weren’t the only ones encountering dog images on this year’s Amazon Prime Day. Amazon Web Services (AWS) -- which supports thousands of websites globally -- experienced its own problems, as businesses attempting to access their management consoles also got puppy images.
These issues may have slipped under the radar, but they were significant -- reinforcing, once again, that even the most reputable service providers can and do experience outages (sometimes at the most inopportune times). The companies using them need to take proactive, diligent steps to insulate themselves.
VMware releases Workstation 15 Pro and Fusion 11

Using a virtual operating system has its merits. For developers, it’s the ideal tool for sandboxing your computer so you can test software for bugs before it’s released to beta testing. You can also install your software across a range of operating systems for compatibility.
As a consumer, there are valid reasons why you may want to consider a virtual system. You may need to use a Windows computer for work but would like to experiment with a Linux installation. A virtual OS enables you to test new bleeding-edge software or tools where you are wary of the source. Problem? Simply revert back to a previous snapshot.
5 ways to regain control of your privacy in Windows 10

Ever since Microsoft introduced Windows 10, which allowed users more insight and control over their privacy, the concern that Windows and other third-parties gather too much information has been growing.
Although Microsoft increased the transparency of privacy policies that doesn’t mean you should leave it at that, because there are some important settings to consider. In this article, I’ll show you 5 ways to regain control of your privacy in Windows 10.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.
