
Legacy modernization: Why observability is the way forward
Technology is critical to the survival of nearly every modern business, and it is advancing at a whirlwind pace to continue supporting these vital digital infrastructures. One such change includes a shift towards Observability. In the past year, log management, unified monitoring and event management vendors have adopted Observability to understand the internal state of their IT systems through the system’s telemetry data outputs.
Why are vendors navigating toward Observability? Telemetry data, including logs, metrics and traces, allow DevOps and SRE teams to quickly understand service-disrupting incidents in their IT systems, analyze the root cause and mitigate the issue. The visibility into these systems is increasingly more essential as IT infrastructures become more distributed, complex, interconnected and, as a result, fragile. In short, Observability helps IT teams work faster and smarter and improve service assurance in extremely complicated production environments.

Malware is being geared to evade AI-based defenses
The latest Cyber Threat Landscape Report out this week from Deep Instinct reveals that bad actors are clearly investing in anti-AI and adversarial attack techniques and integrating these methods into their larger evasion strategy.
It also highlights a change in the way attacks are carried out and says we are now witnessing some groups opting to inflict maximum impact over a shorter time span. These short duration attacks are carried out with the goal of damaging data (its confidentiality and availability), destabilizing a business, and impairing business continuity.

Ransomware is top threat to financial services
The financial, operational, and reputational risks of ransomware make it the top threat facing financial services organizations, a new report from F-Secure says.
The three most common routes used to spread ransomware are phishing, exposed remote desktop protocol (RDP) ports, and the exploitation of vulnerable software.

Microsoft is bringing a much-improved 'Open with' app picker to Windows 11
For time immemorial (almost), when you double click a file in Windows, it will open in the default app that it is associated with. It has long been possible to open files in something other than its default app, using the Open with option; but as anyone who has used this cumbersome menu can attest, this is far from being an elegant solution.
And so with the latest build of Windows 11, Microsoft is making some changes. As well as giving the menu a new look and support for light and dark modes, it is now easier than ever to change the default app associated with a particular file type. Here we show you how to enable it.

The rise of the analytics engineer
The rise of the analytics engineer pays homage to the evolving complexity of modern data analytics. The role encompasses many fields, and is closer to software engineering than traditional analytics, as it involves writing programing scripts and maintaining data as a set of software-producing artifacts.
It’s within the context of a rising awareness of the data ecosystem that the demand gap between data scientists and analytics engineers is closing. Once heralded as the 'sexiest job of the 21st Century', analytics engineers are set to soon steal this accolade away from their antecedents.

Ukraine conflict: Anonymous (and the internet) vs. Russia [Continuously updated]
A few days ago, Russia launched a full-scale invasion of the sovereign nation of Ukraine. Likely most of you have seen at least some of the endless coverage that currently blankets the airwaves. But TV is only giving you part of the story; you can learn a lot more by nosing around online. For the past several days I have kept a running update of what hacktivist collective Anonymous has been up to. The group has been busy and they have made the Russian government even busier, hacking their various state-run 'news' services, such as RT (Russia Today). You can look back at the original post and the multiple updates that were added to it on a daily basis.
Now it’s time to start again and unlike the original story, this time we are letting you know there will be updates that you’ll want to check back in on. We will post them as they happen, which could be once or more in a day. We will begin with what is happening today, March 2.

Microsoft releases Windows 11 Build 22567 with a big new security feature
A month ago, Microsoft announced a change to the Windows Insider program that would see Dev Channel releases becoming "more experimental". As a result of this, the last two builds have introduced bigger changes and new features.
Today’s new flight, Build 22567, continues this trend and comes with some new features and a load of changes and improvements.

Get 'Everyday People, Extraordinary Leadership' ($15 value) FREE for a limited time
Learn how you can tackle everyday leadership challenges regardless of your title, position, or authority with this insightful resource
A book about leadership for people who are not in formal or hierarchical leadership positions, Everyday People, Extraordinary Leadership provides readers with a comprehensive and practical approach to addressing leadership challenges, no matter the setting or circumstance.
OT and ICS vulnerabilities increase in the second half of 2021
Operational technology and industrial control systems saw a 110 percent increase in the number of vulnerabilities disclosed in the second half of last year.
The latest Biannual ICS Risk & Vulnerability Report from Claroty shows that remotely exploitable vulnerabilities are still causing problems, demonstrating the importance of securing remote connections.
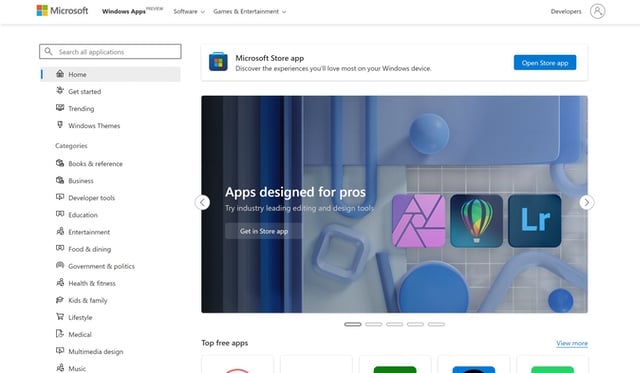
The Microsoft Store undergoes a dramatic Windows 11 redesign online
Microsoft is in the process of rolling out a dramatic redesign of the web version of the Microsoft Store, heavily inspired by Windows 11.
The Fluent design makeover brings the Microsoft Store website more closely in line with the look and feel of Windows 11. This means rounded corners, updated typography and new icons, but the app installation process has also been revamped.

API attacks increase almost 700 percent in the last year
Malicious API traffic has increased 681 percent in the last year, set against a 321 percent increase in overall API traffic.
A new report from API security specialist Salt Security shows 95 percent of surveyed organizations have experienced an API security incident in the past 12 months.

Less than a quarter of directors see ransomware as a top priority
Only 23 percent of board of directors consider ransomware to be their top priority. Yet 59 percent of organizations have fallen victim to ransomware.
A new study from email security company Egress, independently conducted by Arlington Research, polled 500 IT leaders across the US and UK. It finds 52 percent of organizations allocate less than a quarter of their security budget to anti-phishing measures, yet 84 percent were hit by phishing and 42 percent had credentials stolen.

The password hygiene message still isn't getting across to consumers
According to a new report from SpyCloud, 70 percent of breached passwords are still in use and 64 percent of consumers repeat passwords across multiple accounts.
Researchers identified 1.7 billion exposed credentials, a 15 percent increase from 2020, and 13.8 billion recaptured personal identifiable information (PII) records obtained from breaches in 2021.

Certificate outages are an entirely preventable disaster
These days, I wince anytime a major digital service outage makes headlines. Outages happen, of course -- and sometimes they are unavoidable. Servers crash. Cybercriminals get lucky. People make mistakes.
That’s not why I wince, though. I wince because anytime an email exchange goes down, a music service crashes, or a mobile provider loses service, I know there are good odds that the culprit is none of those things. All too often, major service outages come down to two simple words: "expired certificate."

Google explains how it is helping in Ukraine
Google's president of global affairs, Kent Walker, has detailed the various ways in which the company is offering support to the people of Ukraine following the Russian invasion.
The announcement comes after Microsoft made a public declaration of support for the Ukrainian nation and condemned the actions of Russia. Google is offering not only financial support, but also helping to improve security, safety and the dissemination of trustworthy information about the unfolding situation in the country.
