
Nearly 60% of older adults have fallen for cyber scams, report finds
Online scams are evolving quickly, and while younger people often adapt with ease, older adults may not be keeping up.
According to Avast, nearly 60 percent of older loved ones have already fallen victim to cybercrime. Even when younger family members raise the alarm, the message does not always get through. Although 84 percent of adults say they have spoken to older relatives about potentially risky online habits, only 53 percent of those warned have taken the advice seriously and made changes

Windows Restrictions Fixer 2.0 restores disabled features with ease
Windows Restrictions Fixer is a lightweight tool that can detect disabled Windows features and give you the opportunity to re-enable them in just a few clicks.
While it's possible to manually reverse many restrictions through the registry or Group Policy Editor, this app offers a much simpler route for those who prefer not to dig around in system files, or just don’t know where to begin.

SMEs need to get a grip on their cloud costs
According to the Office for National Statistics, in late May 2025, 77 percent of UK businesses with 10 or more employees reported that their staffing costs, covering wages, bonuses, national insurance (NI) and pension contributions, had increased over the preceding three months; a rise of 41 percent since late February 2025, and a 17 percent rise from the year before.
In the light of this Brian Sibley, Virtual CTO at Espria, says clear and concise billing models for the cloud are needed for a wholly comprehensive understanding and urges businesses to urgently assess their MS Azure subscriptions to reduce costs and improve services.

Open-source malware targets data exfiltration
Supply chain security company Sonatype has released the Q2 2025 edition of its Open Source Malware Index, uncovering 16,279 malicious open source packages across major ecosystem.
This brings the total number of open-source malware packages Sonatype has discovered to 845,204. Compared to the end of the same quarter last year, the total volume of malware logged by Sonatype has surged 188 percent, underscoring the growing sophistication and scale of attacks aimed at developers, software teams, and CI/CD pipelines.
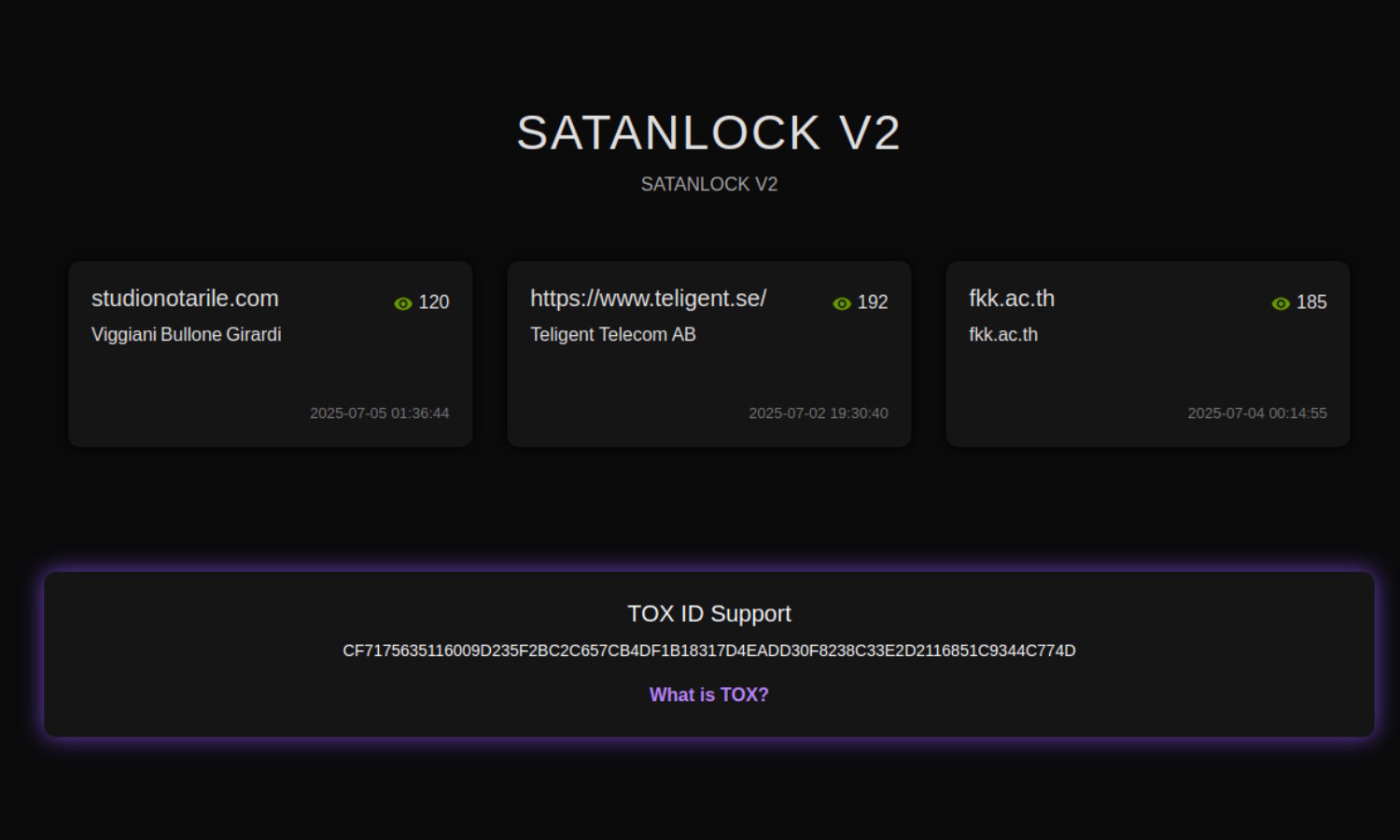
Short-lived ransomware group SatanLock to close down and leak data
There are large numbers of ransomware groups operating around the world, some of which have been conducting their nefarious work for years. There are older which are rather less long in the tooth, such as the recently formed SatanLock.
The group has been in existence for mere months, popping up in April this year. Responsible for a spate of attacks over a number of weeks, the ransomware group has announced that it is already shutting up shop. More than this, it plans to leak any data it has stolen.

Thunderbird 140 'Eclipse' offers a simpler, more flexible way to manage email across platforms
Thunderbird 140 “Eclipse,” is officially here. Released as the latest Extended Support Release, it offers long-term stability and fewer changes over time, handy for users who prioritize reliability over rapid updates.
The latest build introduces new visual tools, improved usability, and behind-the-scenes improvements to one of the most established open-source email clients available today.

Jack Dorsey’s latest project is the Bluetooth mesh network app bitchat
Jack Dorsey – the co-founder of Twitter and Block, and the founder of Bluesky – took to X to share some enticing details about the latest project he is working on.
Called bitchat, this is a messaging app that not only has security at its very core, but does not require internet access to work. A messaging app without internet? Dorsey explains that this is a secure, decentralized, peer-to-peer messaging app that works over Bluetooth mesh networks.

Windows 11 is finally more popular than Windows 10
It took a long time, undoubtedly much longer than Microsoft would have liked, but Windows 11 is now more popular than Windows 10. The most recent version of Microsoft’s desktop operating system is now installed on more desktop computers than its predecessor.
Is this a cause for celebration at Microsoft HQ? Probably not. While Windows 11 may finally have a larger install base than Windows 10, it took four long years for this landmark to be reached. In the world of software development, that is an age.
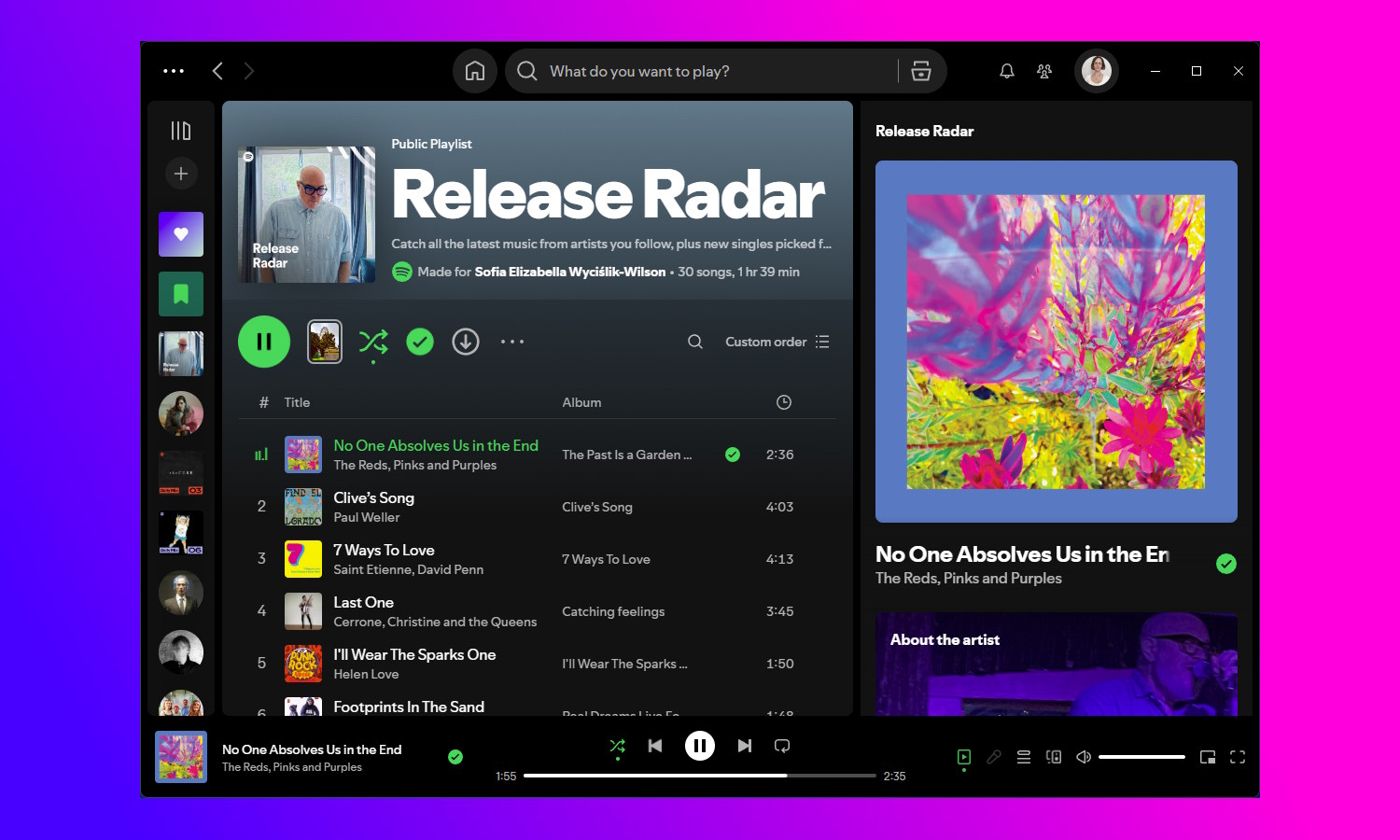
Android Auto’s Spotify update adds new playlist options for long trips
Spotify and Android Auto is a perfect pairing, and with the latest update to the app things just got even better. There is something of a UX-enhancing face-lift to the app, but the update also sees the arrival of new collaborative playlist options.
Jams are not usually a good thing on car journeys, but in the case of Spotify Jam it’s a little different. The feature lets everyone in the vehicle add their own music to a queue and create a playlist that will include something for everyone’s taste.
Windows 11 25H2 has a new option to remove all unwanted Microsoft apps
It is not long until the next big update for Windows 11 is released. We don’t yet have an exact date for the availability of Windows 11 25H2 (although October looks likely a candidate) but we already know a lot about what to expect from it.
One of the changes that will be welcomed by many users, but business and enterprise users in particular, is the arrival of a new way to remove all unwanted Microsoft apps in one fell swoop. Via Group Policy, the new Remove Default Microsoft Store Packages policy helps to debloat Windows 11 in a flash.

AI is quietly taking over enterprise cybersecurity -- this is what you need to know
AI is reshaping how companies protect themselves against cyber threats, according to new research from ISG Software Research.
Enterprises are building layered cybersecurity defense systems that combine access controls, endpoint monitoring, and data recovery, and artificial intelligence is helping these systems adapt faster and work more effectively.

7-Zip 25 maximizes CPU threads, compresses files faster -- download it now!
Developer Igor Pavlov has released a new version of 7-Zip, his long-standing and hugely popular file archiving tool.
The 25th edition of the software introduces improvements in compression speed and support for modern multi-core systems, helping power users handle large archives more efficiently.

Infostealers blamed for surge in identity attacks
Advanced phishing kits and info-stealing malware have accounted for a 156 percent jump in cyberattacks targeting user logins.
A new report from cybersecurity company eSentire shows attackers are increasingly opting for obtaining login credentials and session cookies via phishing or malware. This then allows them to carry out Business Email Compromise (BEC) attacks, gain access to bank accounts, or steal cryptocurrency.

Why Active Directory remains a popular target for attackers and what to do about it [Q&A]
Microsoft Active Directory (AD) turned 25 earlier this year -- remarkable longevity in the technology world. It’s the identity backbone for more than 80 percent of enterprises, meaning a breach could be catastrophic.
We spoke to Sean Deuby, principal technologist at Semperis, to look at the top considerations for protecting AD for the future, as most organizations he talks to have no plans to move on from the aging technology.
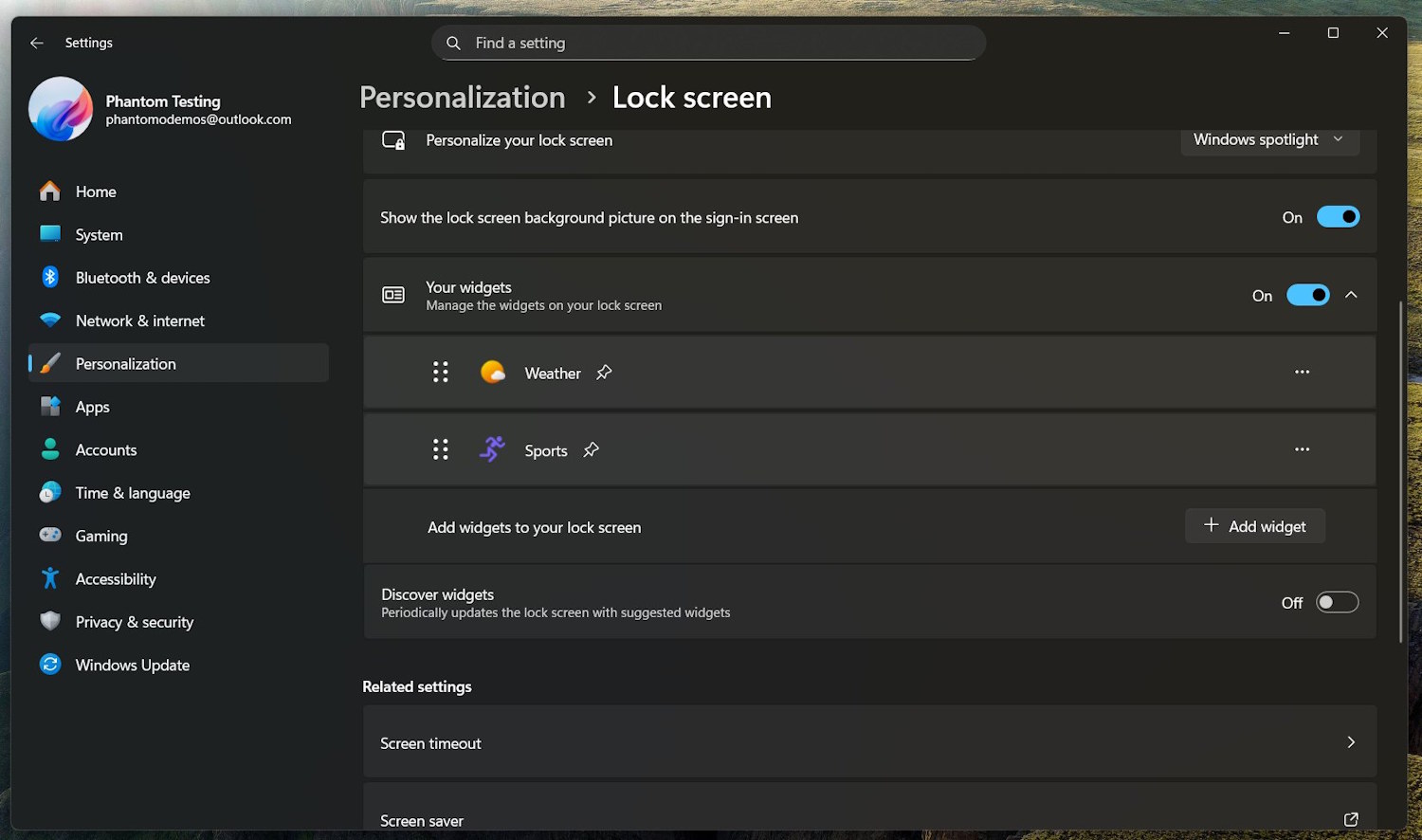
Microsoft will use the Windows 11 lock screen to recommend widgets
It took Microsoft a long time to embrace widgets, but the company is now doing so wholeheartedly. While smartphone and tablet users – and, indeed, Mac owners – have developed a relationship with widgets, the same cannot be said of Windows 11 users.
But this is something Microsoft wants to change. In a move that will almost certainly prove to be popular and controversial in equal measure, the company is going to the Windows 11 lock screen to recommend widgets you might be interested in.
