
antiX 23.2 launches with Debian 12 base and no systemd for lightweight Linux experience
Linux distribution antiX-23.2, dubbed “Arditi del Popolo,” has been released. If you’re already on antiX-23 or antiX-23.1 there is no need to reinstall. This update is all about cleaning things up and keeping things running smoothly, staying true to the antiX tradition of avoiding systemd and elogind altogether. It’s perfect for folks who like to keep their systems lightweight and free from those dependencies.
If you’re familiar with antiX, you know it offers a range of options. antiX-23.2 supports both 32-bit and 64-bit systems and lets you pick between sysVinit and runit. The antiX-full version comes in at about 1.8GB and packs in four window managers: IceWM (which is the default), Fluxbox, JWM, and Herbstluftwm. It comes with LibreOffice too. If you’re rocking the 64-bit version, you’ve got a choice of two kernels -- Legacy 5.10 and Modern 6.1.

Defending healthcare systems against ransomware attacks [Q&A]
Ransomware attacks target industries across the board, but they're of particular concern in the healthcare sector where an attack can mean not only data is at risk but lives too.
We spoke with Amitabh Sinha, chief strategy officer and co-founder of Workspot, to discuss the productivity and patient care aspects of these attacks as well as how modern ransomware recovery strategies can help to ensure mission-critical operations can continue, even during an attack.

Google removes Kaspersky apps from its store
Google has unceremoniously evicted Kaspersky’s apps from the Play Store. While the Russian security firm insists that the removal is temporary, it comes after the company’s software was banded from being sold in the US.
The move not only means that it is no longer possible to download Kaspersky apps from Google store, but also that existing users are unable to obtain updates. Google did announce the removals ahead of time.

5 best Linux distros to replace Windows 11 and take control of your PC
If you’re anything like me, dear BetaNews readers, you are tired of Windows 11’s constant updates and telemetry concerns. If you have the urge to escape the grasp of Microsoft, switching to Linux might be exactly what you need. Linux has matured over the years into a versatile and user-friendly alternative to Windows. Whether you’re a casual user, gamer, or developer, there’s a Linux distribution (distro) out there for you.
Here are 5 Linux distros for those ready to break free from Windows 11.

Save $33.99! Get 'High Performance with Java' for FREE
Building high performance into your applications is key to creating an optimal user experience, although it is not the only consideration for the performant nature of your apps.
High performance applications can lead to cost-effective resource utilization, especially when scalability and cloud computing are involved. They can also provide highly reliable systems that are easier to maintain. High Performance with Java begins by helping you explore the Java Virtual Machine (JVM) and understand how to push it to its limits to further optimize your programs.

Addlink G55 and G55H NVMe SSDs deliver blazing PCIe Gen5 speeds
In a world where speed and performance are more important than ever, Addlink is stepping up to the plate with its G55 and G55H series of NVMe SSDs. These drives are engineered for power users who demand top-tier storage solutions, whether it’s for gaming, content creation, or heavy-duty computing. With blistering speeds that push PCIe Gen5x4 NVMe 2.0 technology to the max, these drives are not only fast but designed to stay cool under pressure -- especially with the G55H variant, which comes equipped with a heatsink.
The Addlink G55 and G55H SSDs are available in 1TB, 2TB, and 4TB capacities, offering flexibility based on your storage needs. Both models are built with 3D TLC NAND flash, which delivers impressive read and write speeds across the board. The 1TB version boasts read speeds up to 10,200MB/s and write speeds of 8,300MB/s, while the 2TB and 4TB options push even further, with 10,300MB/s read and 9,000MB/s write speeds. These kinds of numbers ensure lightning-fast load times, quick data transfers, and smooth performance in demanding applications.

Save $35.99! Get 'Mastering PowerShell Scripting, Fifth Edition' for FREE
Mastering PowerShell Scripting, Fifth Edition, can help you overcome any fears and become proficient in navigating PowerShell's capabilities. This edition includes new chapters on debugging, troubleshooting, and creating GUIs.
You will learn about the latest features of PowerShell 7.3, including working with parameters, objects, and .NET classes.

Patriot launches Viper Gaming V30 A2 microSD card
Patriot has introduced the Viper Gaming Series V30 A2 microSD card, offering a powerful storage solution designed with gamers in mind. This new addition to the Viper Gaming brand comes in capacities ranging from 128GB to 1TB.
With the Viper Gaming V30 A2 microSD card, gamers can take advantage of read speeds up to 100MB/s and write speeds up to 90MB/s. Built on U3, Class 10, A2, V30, and UHS-I technology standards, it is optimized for loading large AAA games and running high-performance apps. Its is ideal for expanding storage on portable gaming devices such as the Nintendo Switch, Steam Deck, ROG Ally, as well as smartphones and tablets.

Malwarebytes Browser Guard gains new identity features
Browser Guard, the free browser extension from Malwarebytes, has added some new features aimed at enhancing users' privacy and protecting their identity online.
Users will now receive a pop-up alert if a website they visit was involved in a recent breach, offering the ability to click and scan their digital footprint to evaluate if private information was exposed.
Best Windows apps this week
Six-hundred-fifteen in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released Windows 11, version 24H2. It is available for seekers only at this time and introduces support for Wi-Fi 7 and new AI features among other things.
It's finally time to say goodbye to Windows 11 -- Nitrux Linux 3.7.0 is the OS you've been waiting for!
Let’s be honest. Too many of us use Windows 11 out of habit and convenience, not because it’s any good. If you’ve been thinking about leaving Microsoft’s OS for a while now but aren’t sure where to go for your next step, we have the answer.
Nitrux offers a smoother, more streamlined OS experience without the bloat. This Linux OS is built on a lightweight foundation and offers a stylish system tailored for modern users. With its unique NX Desktop, the OS is fast, responsive, and provides a visually appealing interface, making it a compelling alternative for those tired of Windows’ sluggish updates and resource-heavy performance.
How to unlock the power of real-time analytics [Q&A]
The increased need for real-time analytics is driven by the rise of the on-demand economy, where consumer expectations for immediate access to products, services, and information are transforming how businesses operate and compete.
We spoke to Kishore Gopalakrishna, co-founder and CEO of StarTree, to discuss the need for real-time data capabilities, the strategic utilization of real-time data to enhance operational efficiency and competitiveness, and the essential technology and operational considerations for building a robust analytics infrastructure.

Microsoft confirms numerous bugs in the Windows 11 2024 Update and blocks rollout to many
It is just a few days since Microsoft unleashed Windows 11 24H2 (or the Windows 11 2024 Update). But the release of the eagerly awaited update has been more than a little problematic.
We’ve already seen various issues with the controversial Recall feature, but Microsoft has also confirmed a number of known issues with the update. So significant are some of the issues that some users are being denied the opportunity to perform the upgrade. Gamers are among those hit by the problems.

Spotify adds Offline Backup feature that automatically creates offline playlists
With mobiles connected to the internet on a near-permanent basis, it is easy to take for granted. This means that whenever a connection is not available, it is very apparent. Now Spotify is taking steps to help reduce the impact of a loss of connection.
While it is already possible to create offline playlists, this is something that needs to be done manually and it’s all too easy to find yourself on a flight with the sudden realization that you forgot to set it up. And this is precisely where the new Offline Backup mode helps, creating offline playlists automatically, based on your recent listening.
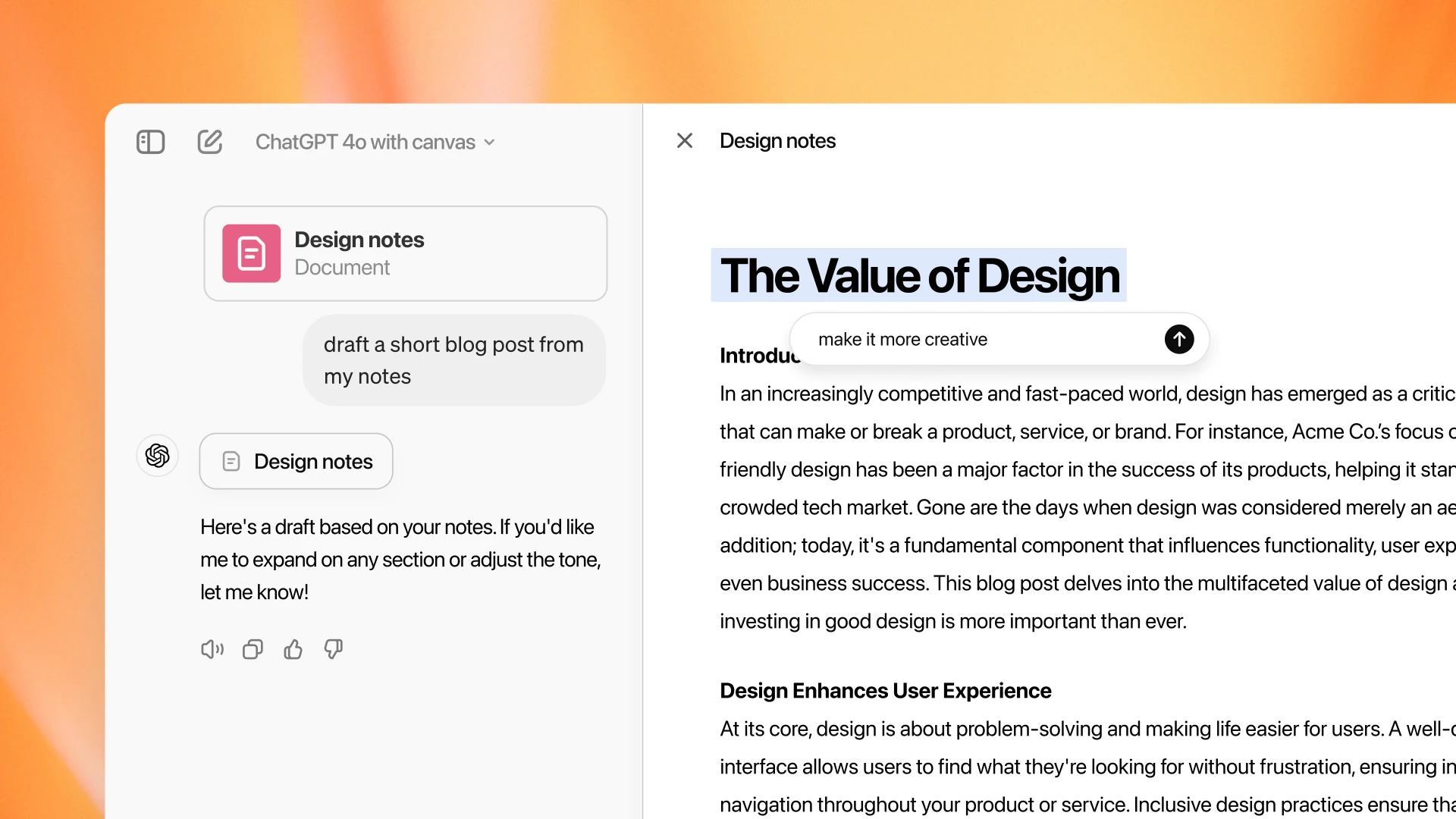
OpenAI introduces Canvas: A new way to collaborate with ChatGPT for writing and coding
OpenAI has introduced a new interface called “Canvas,” designed to enhance collaboration with ChatGPT for writing and coding projects. Unlike the standard chat interface, Canvas allows users to interact with their projects more dynamically by opening in a separate window where users and ChatGPT can work side by side. This feature, currently in beta, is available for ChatGPT Plus and Team users, with plans to extend access to Enterprise and Edu users soon. Once the beta phase is complete, the feature will eventually be made available to ChatGPT Free users.
Canvas uses GPT-4o and can be manually selected in the model picker. The aim is to offer a better interface for tasks requiring multiple revisions and edits, such as writing content or coding. The chat interface works well for many tasks, but canvas is designed to address the needs of users working on more complex projects that benefit from a more structured environment.



