
Meta is discontinuing Windows and Mac Messenger apps
Meta has confirmed that the Windows and Mac versions of its Messenger desktop app are to be discontinued. While no reason has been given for the deprecation, the company is probably trying to cut back on the number of products it has to develop and support.
There are just two months to go until the Messenger desktop apps cease to function, and users should start to see notifications to this effect when they log in.

Addressing the data protection challenges of rolling out AI [Q&A]
Artificial intelligence is transforming the way that many areas of business operate. But with the benefits also come new risks to corporate data.
We spoke to Rohan Sathe, CEO and co-founder of Nightfall AI, to find out how AI risks exposing sensitive information and what companies can do to protect themselves.

Other World Computing announces new accessories for Apple's new M5 MacBook and iPad Pro
Following Apple’s launch of its new M5-powered MacBook Pro and iPad Pro yesterday, Other World Computing has announced a range of docks and external drives built to work with the updated products.
The company says the accessories expand connection and storage options for users adopting Apple’s latest chip generation.

Microsoft remains the most imitated brand in phishing scams
Microsoft was the most impersonated brand in worldwide phishing attacks during the third quarter of 2025. 40 percent of such attempts used the company’s name, according to Check Point Research’s Brand Phishing Report for Q3.
Google took the second spot with 9 percent of global phishing activity, while Apple was third with 6 percent. Together, those three names accounted for more than half of all brand impersonation attempts in the period.

Outdated finance systems drive away talent
Nearly 40 percent of finance professionals would consider changing employers due to outdated financial systems according to new research.
The report from insightsoftware shows businesses are struggling with the need for real-time insights and the younger generation’s demands for tools that eliminate inefficiencies and foster collaboration.

ARC ON·EAR brings studio-accurate sound to headphones
IK Multimedia has released ARC ON·EAR, a portable system that corrects the sound of headphones and recreates how music feels on studio monitors. The small DAC and headphone amplifier gives engineers and producers a way to hear an honest mix anywhere, without relying on extra software or plug-ins.
Mixing with headphones can be tricky. Even the best pairs can push certain tones too hard or make the stereo field seem wider than it really is. ARC ON·EAR deals with that by adjusting how supported models respond, creating a balanced image that feels closer to sitting in front of real speakers.

Q3 ransomware attacks up 36 percent year-on-year
New data from BlackFog shows publicly disclosed ransomware attacks continued to set new records in the third quarter of this year, with 270 attacks -- a 36 percent increase compared to the same quarter in 2024 (198 attacks). This also represents a 335 percent increase since Q3 2020, underscoring the continued rise in attacks over the last five years.
Between July and September, publicly disclosed attacks were attributed to 54 ransomware groups. As in Q2, the Qilin ransomware gang was the most active, responsible for 20 incidents during the period. Notably, approximately 40 percent (107) of reported attacks have not yet been attributed to any known ransomware group.

AI delivers time gains but people are still key to productivity
Workers say they are saving an average of two hours per day thanks to AI use. But these perceptions of productivity gains are at odds with the reality experienced by many organisations according to a new report.
A study from the Adecco Group draws on insights from 37,500 workers across 31 countries and 21 industries. It finds confidence in AI usage has surged, with a staggering 71 percent of respondents suggesting that nothing holds them back from using AI, a significant jump from 19 percent in 2024.

Microsoft has broken Active Directory for some Windows Server users
With the most recent security updates released this month, Microsoft has introduced an issue for some Windows Server users. The KB5065426 update was released a few days ago, including not only security fixes, but also new features.
The unexpected payload, however, is the appearance of a problem with active Directory. Microsoft summarizes the problem in an advisory notice entitled “Directory synchronization fails for AD security groups exceeding 10,000 members”.
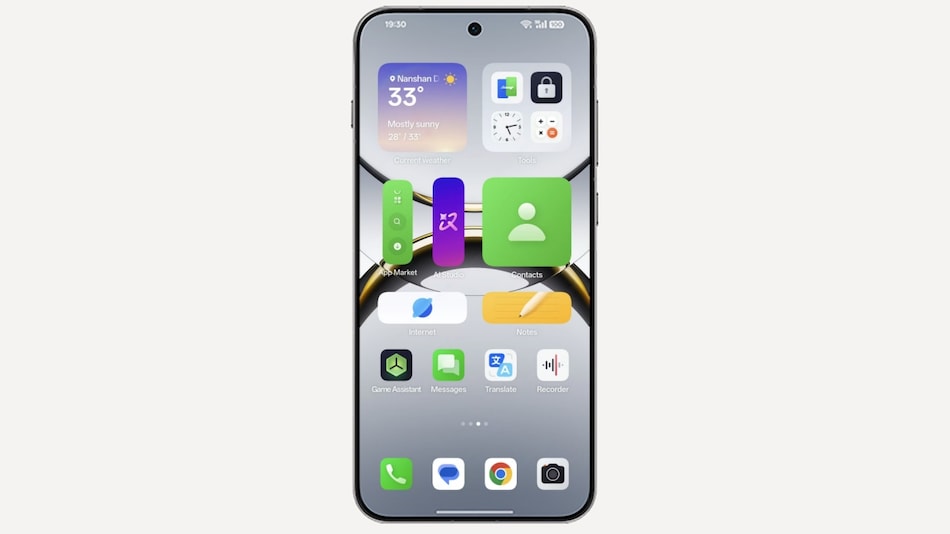
OPPO unveils ColorOS 16, the latest version of its smartphone software with AI and design upgrades
Chinese smartphone maker OPPO has taken the wraps off ColorOS 16, the latest version of its Android-based operating system which is set to debut with its upcoming Find X9 Series.
The update builds on the groundwork of ColorOS 15, introducing improvements to performance, animation, and design, and adding improved AI tools and multi-device connectivity.
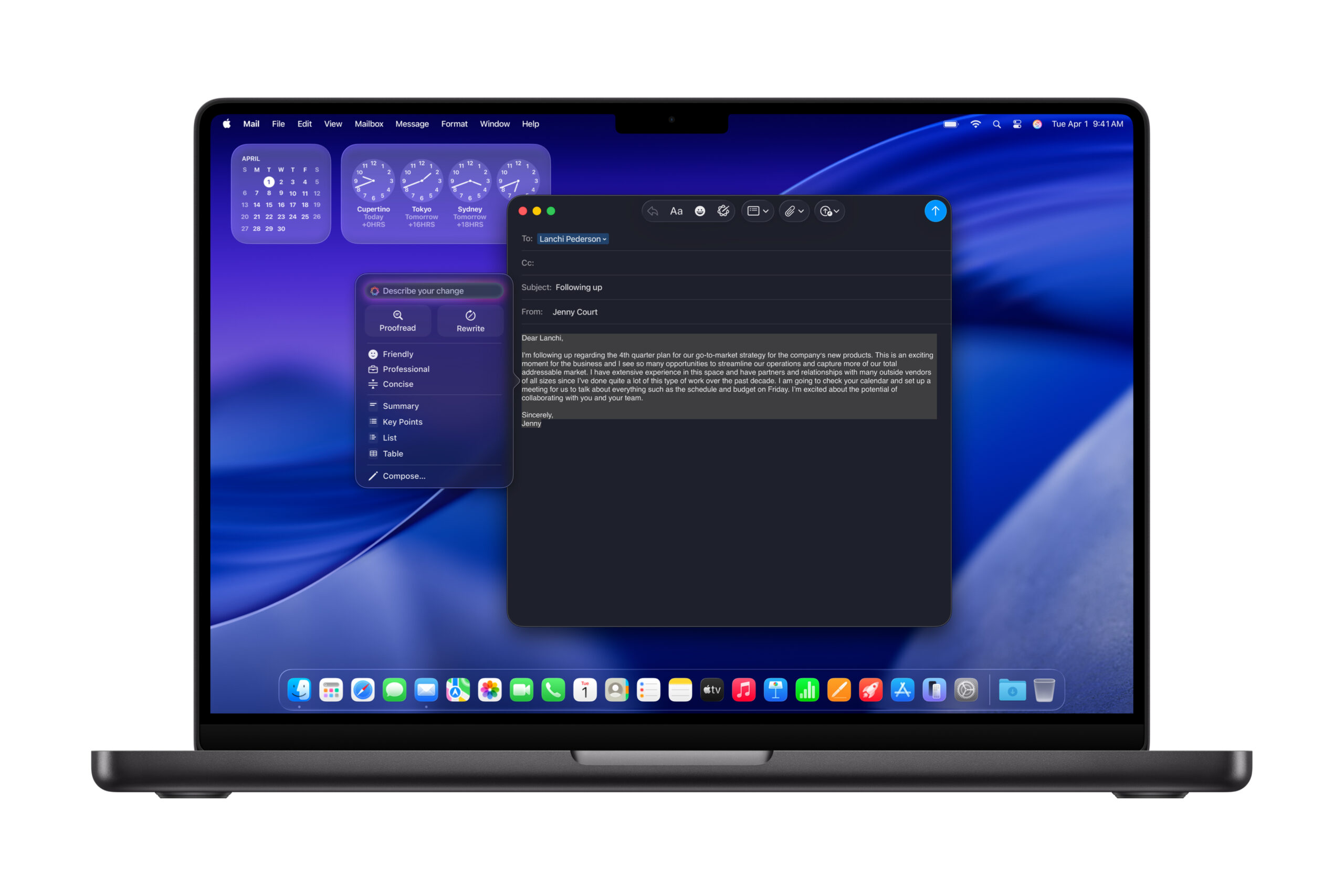
Apple upgrades MacBook Pro with M5 chip, improved battery life, and faster AI performance
As well as announcing a new iPad Pro powered by its M5 processor, Apple today also introduced a new 14-inch MacBook Pro powered by the same chip. The latest model focuses naturally enough on AI and efficiency improvements, blending faster performance with extended battery life and the new macOS Tahoe operating system.
The M5 chip builds on Apple’s push toward on-device AI. It features a 10-core GPU with a Neural Accelerator in each core and a faster 16-core Neural Engine, offering up to 3.5 times more AI performance than the M4 and as much as six times faster than the original M1.

Apple unveils iPad Pro with M5 chip and major focus on AI performance
As was widely expected, Apple has taken the wraps off its latest iPad Pro powered by the M5 processor, which includes a 10-core GPU, new ray-tracing support, and a 10-core CPU split between performance and efficiency cores.
The new device, available in 11-inch and 13-inch sizes, offers faster AI processing, upgraded connectivity, and an improved display, while iPadOS 26 arrives with new tools designed to make the tablet better suited for work and productivity tasks.

Gen Z targeted by AI-driven extortion scams
New research looking at high pressure extortion scams reveals that Gen Z is being particularly impacted by AI-powered threats. All mobile users are at risk, however, with one in three having been targeted by an extortion scam, often threatening to expose pictures or browsing history, and nearly one in five falling victim.
The research from Malwarebytes shows a distinct target profile for extortion. 69 percent of victims and 64 percent of targets are Gen Z or Millennial (compared 52 percent of victims and 40 percent of targets of other types of scams). 65 percent of victims and 60 percent of targets are male (vs. 48 percent/45 percent)

Google steps up the fight against scams with new tools and more education
Scams and fraud are an ever present threat on the internet and the rise of AI means that they’re getting harder to spot with the old giveaways of bad grammar and dodgy attachments largely eliminated.
Google is announcing a range of new tools and initiatives to help people remain safe online. These include improved app features, new account recovery tools and better education and awareness programs.
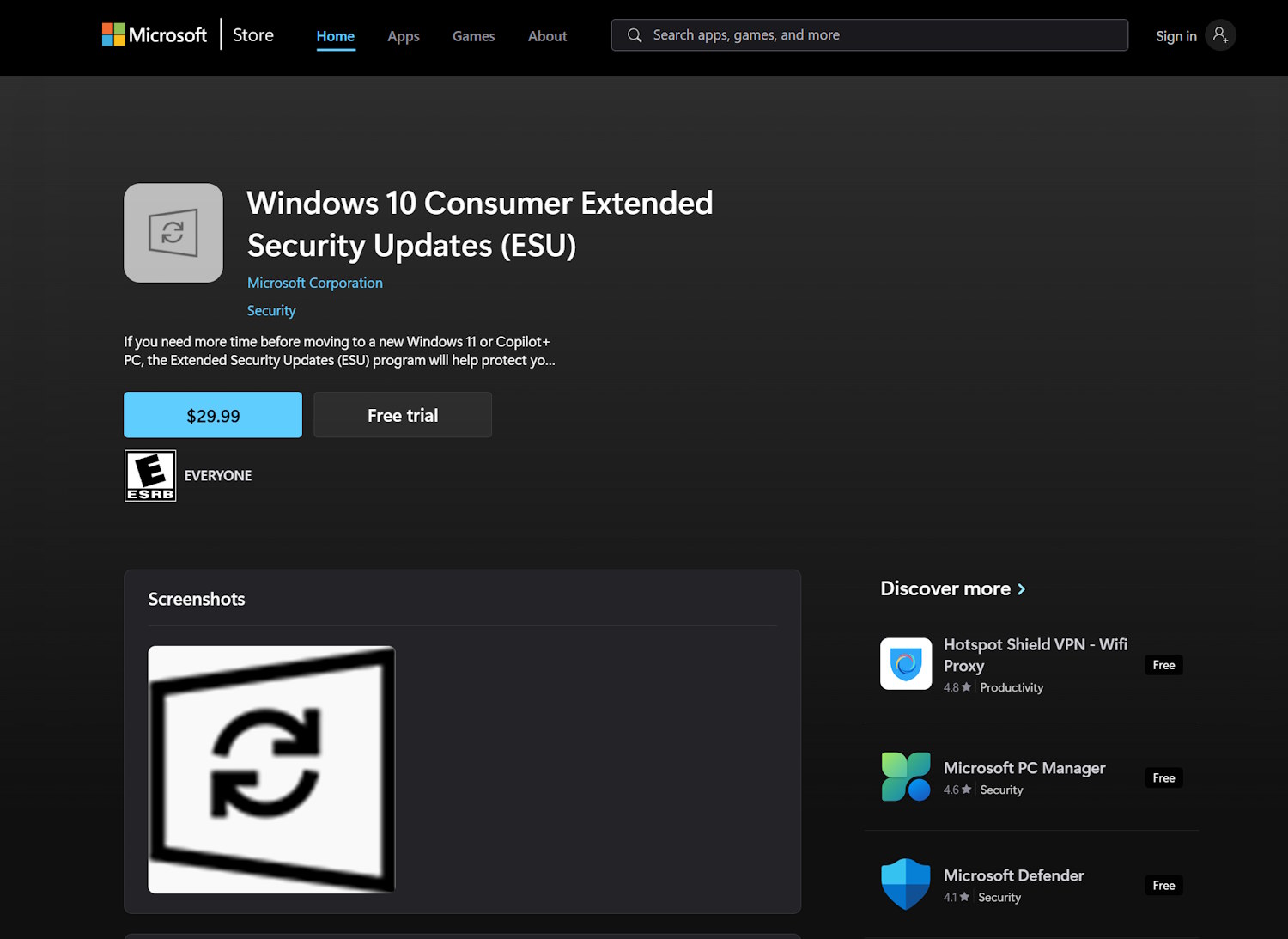
Windows 10 Consumer Extended Security Updates slide into the Microsoft Store
The day has come and gone: Microsoft no longer supports Windows 10 for users who are not signed up for Extended Security Updates. Much has been made of the price and availability of these updates, including the difference between the EU – where they are free – and the rest of the world.
There are various ways to access and sign up for Extended Security Updates (ESU), and Microsoft has just added a new one. It is now possible to access the ESU program via the Microsoft Store – but there is no change to pricing.



