Adam Mosseri suggests highlighting ‘real media’ rather than AI content on social media
Instagram head Adam Mosseri has ended 2025 in a reflective mood, looking at the social media trends he sees being the hallmarks of the year ahead. Perhaps unsurprisingly, he sees the onslaught of AI continuing, and has some thoughts about what this means and how to handle it.
Mosseri makes a couple of statements that are difficult to disagree with: “Deepfakes are getting better and better”, and “AI is generating photographs and videos indistinguishable from captured media”. Interestingly, though, he does not necessarily see this as a problem.

Why keeping old customer records could cost millions [Q&A]
The modern world thrives on data, but what happens when that data has outlived its usefulness? Legacy data can become a weak link in corporate security. These records don’t just take up space; they expand the exposure surface in a breach and can damage both finances and reputations.
We spoke with Rob Shavell, co-founder and CEO of DeleteMe, about why companies can’t afford to ignore legacy data and what they can do to address it.

Maturing ID wallets, investment for compliance and confidential AI -- privacy predictions for 2026
Privacy has been increasingly in the news over the last year with plans for government digital IDs and age verification for websites, as well as concerns about how eCommerce businesses and others use personal data.
What can we expect from the privacy landscape in 2026? Some industry experts give us their views.
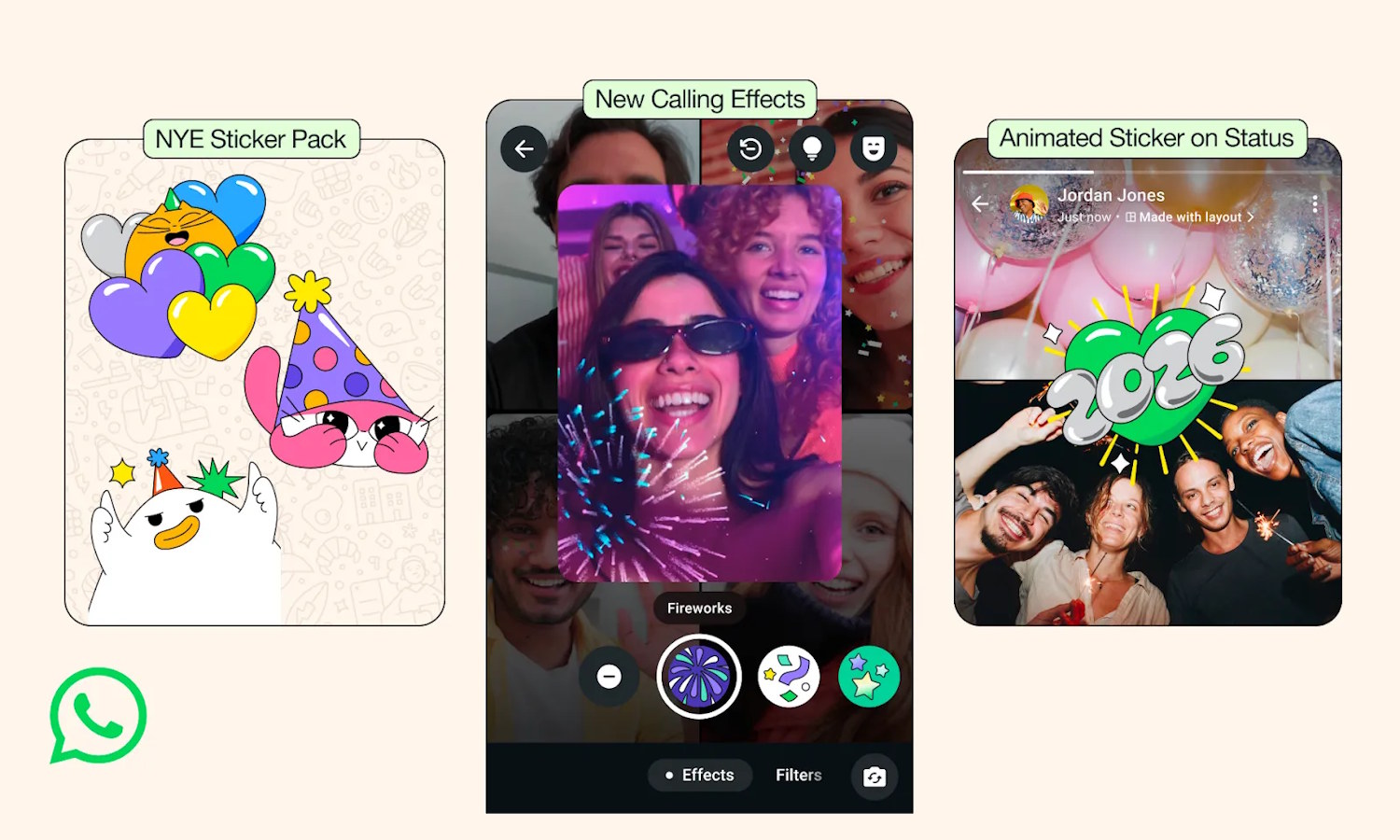
WhatsApp celebrates the new year with a festive update
With the end of 2025 drawing ever closer WhatsApp is getting ready for its busiest period. As the clock strikes midnight around the world, a surge of messages will be sent over the platform, and Meta is using the arrival of 2026 as a launchpad for new features and options – as well as highlighting recent additions which lend themselves to this time of year.
The company has focused on the celebratory and connective nature of New Year, providing new ways to liven up the messages you send to friends and family. There is quite a lot here, from new stickers and call effects, to the arrival of animated stickers in Status updates.
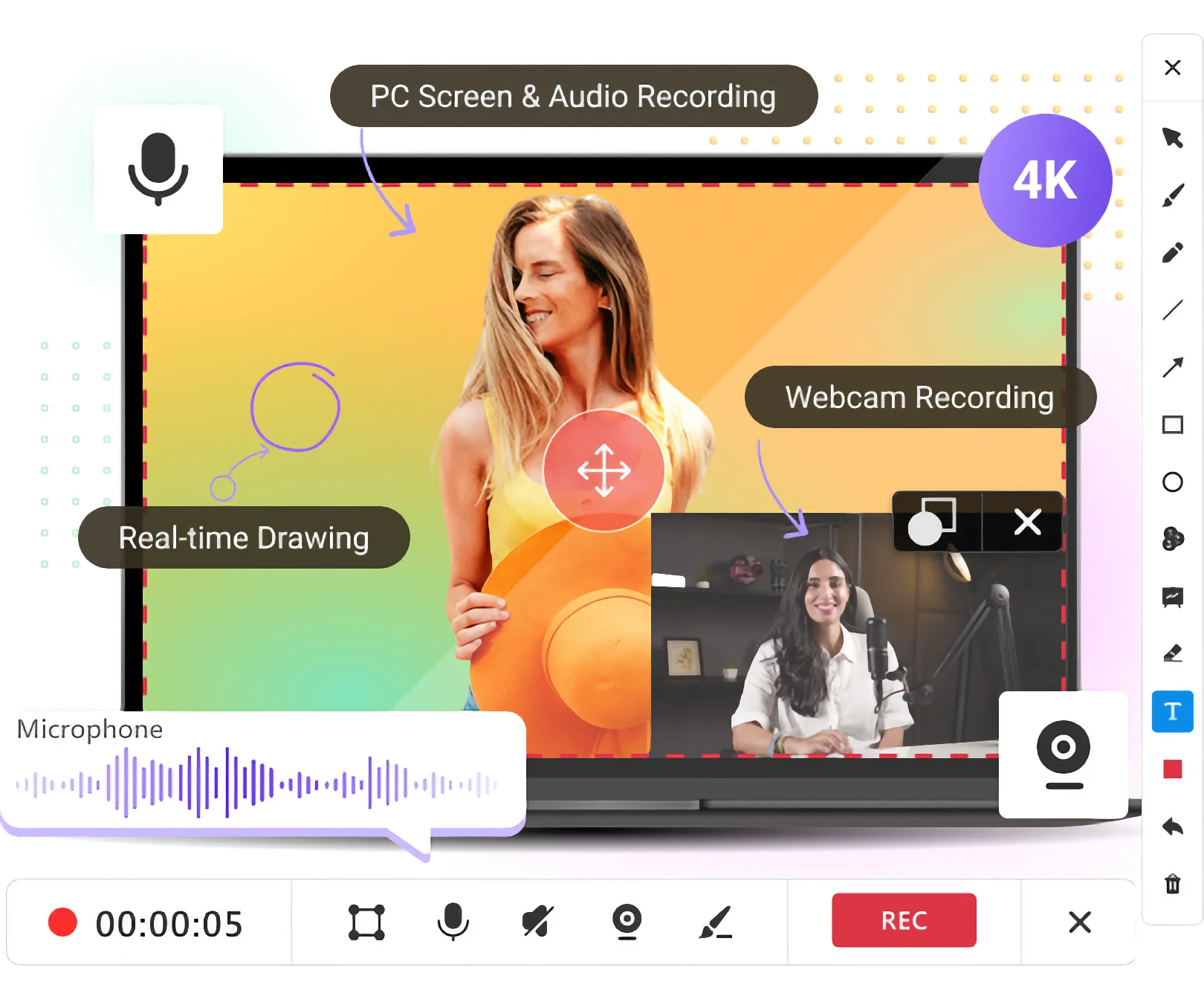
MiniTool releases a free screen recorder without watermarks or time restrictions
MiniTool has released Screen Recorder 1.0, a free screen recording tool for Windows designed to handle basic screen, audio, and webcam recording tasks without watermarks or time limits.
The app offers a limited but familiar set of features rather than advanced tools or editing functions. It can be used to record tutorials, presentations, videos, or general on-screen activity with minimal configuration.

How AI can supercharge fraud in the enterprise [Q&A]
The FBI reports that complaints around deepfake AI videos have more than doubled, and financial losses have nearly tripled this year.
Agentic AI is set to accelerate this process, making it even easier to commit fraud with deepfakes. We spoke to Alix Melchy, VP of AI at Jumio, to discuss the threat and how to combat it.
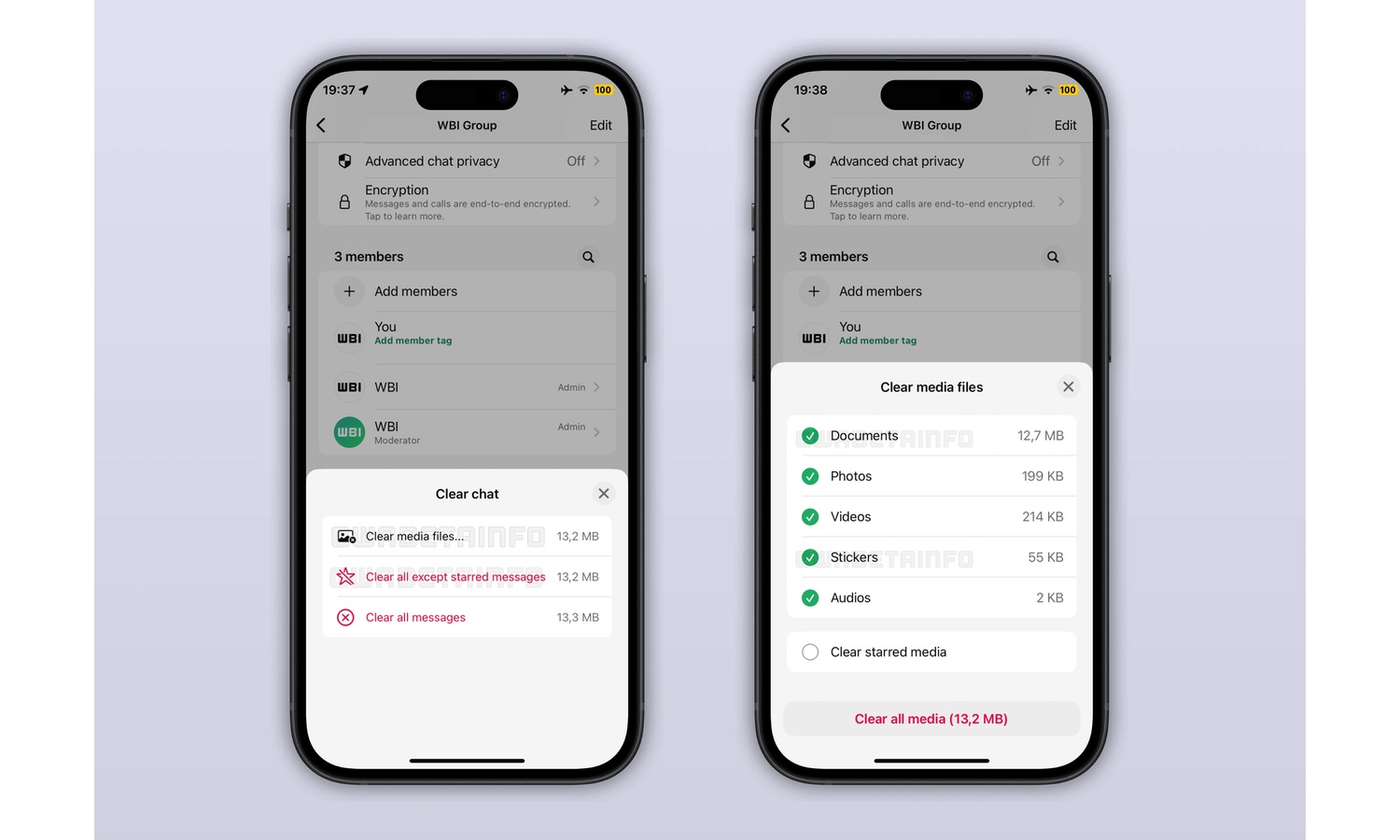
WhatsApp for iOS gains an enhanced Clear Chat feature
Currently in beta testing, iPhone users are being given access to an enhanced and updated version of WhatsApp’s chat cleanup tool.
The feature – which allows for the deletion of messages and media in different ways – is not completely new, but it now offers greater control over what is deleted. The cleanup tool now provides a better balance between freeing up space and retaining the files that were shared in a chat.

Microsoft makes securing files faster with hardware-accelerated BitLocker
If you have use BitLocker to secure files within Windows 11, you will almost certainly have noticed something of a performance hit. Microsoft is not unaware of this, and is taking steps to help improve things.
The company is rolling out hardware-accelerated BitLocker, which should help to provide a speed boost on systems with NVMe drives. The new approach helps to avoid bottlenecks which can massively impact on performance.
Google is making it easier to change your Gmail address
Depending on when you signed up for a Gmail account, and factoring in the uniqueness or otherwise of your name, your email address may be one you are happy with, or it could feel like a burden.
If you have become unhappy with the @gmail.com address you chose years ago, you have always been able to sign up for another account. But actually changing your email address is a different matter – and it is something that Google appears to be experimenting with.

Data sovereignty, cloud and security [Q&A]
As more and more information is stored in the cloud, often with hyperscale providers, the issue of data sovereignty -- where the information resides and who can access it -- becomes increasingly crucial.
We spoke to Sergej Epp, CISO at Sysdig, and previously CISO at Palo Alto Networks, to explore the theme of data sovereignty, cloud and security.
Maingear now lets buyers bring their own RAM to avoid DDR5 price spikes
Maingear has introduced a new option called BYO RAM Builds, letting customers order a desktop without buying memory from the company. The move comes at a time when DDR5 pricing has become unpredictable, with significant increases across many kits. BYO RAM gives buyers a way to manage system cost by supplying their own compatible memory.
The price of DDR5 kits have skyrocketed recently as AI infrastructure demand continues to steal memory supply away from consumers. Retail availability is uneven, and pricing swings have made it difficult to plan a new build without watching the prices almost daily.

Lemon Slice 2 turns any single image into a real time, talking AI avatar
Lemon Slice, a new research and product lab focused on interactive video technology, has released Lemon Slice 2. The latest model turns a single image into a real time conversational avatar. It works with a wide range of images and is available as both an API and an embeddable widget.
The company describes its new model as a zero shot system that produces a live video call from one input. The tool accepts many types of visuals, including portraits, illustrations, and stylized artwork. Once uploaded, the model generates a moving avatar that responds in real time during a conversation, as you can see in the video at the bottom of the page.
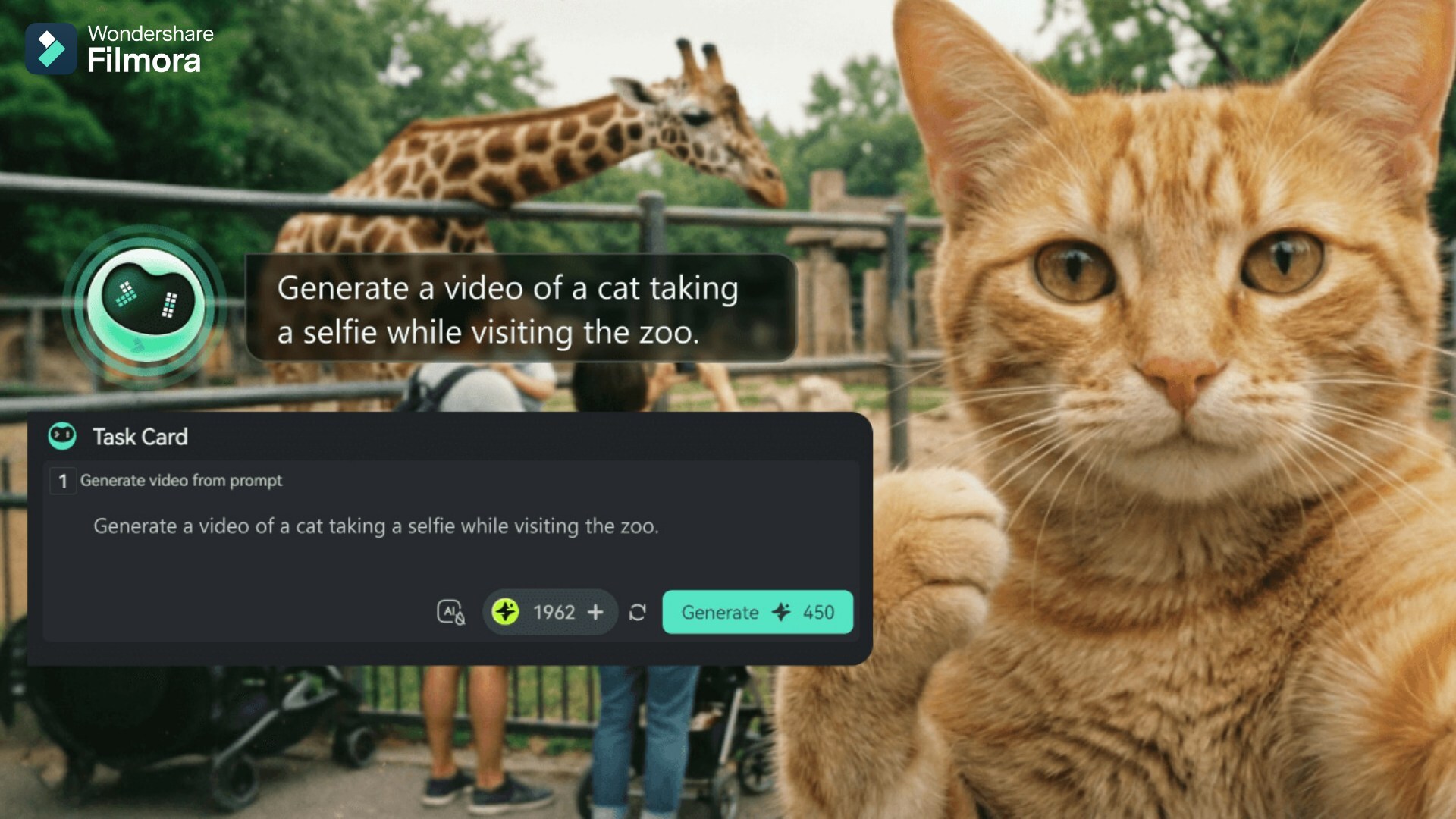
Wondershare brings new AI Mate editing assistant to Filmora V15
Wondershare has added a new intelligent assistant called AI Mate to Filmora V15 for Windows and macOS. The tool, built into the editor, can help users plan ideas, understand how features work, automate multi step tasks, and complete common actions with less manual effort.
AI Mate offers four options:
AI video tools and how they’re changing business communication [Q&A]
The use of AI video has exploded in the past year. But while it’s deepfakes that make the headlines the technology also has the potential to change how businesses create and use video content in their messaging.
We spoke to Victor Erukhimov, chief executive officer of CraftStory, to find out more about AI video and how businesses can exploit it to their advantage.

AI risks, greater regulation and remote consultations -- healthtech predictions for 2026
Understandably perhaps the health sector has been slower than some to embrace the rush to AI. But more medical devices are now connected and AI is having an impact, offering benefits to patients but also opening up new risks.
We spoke to some leading industry figures to find out how they see healthtech developing in 2026



