
Fedora Linux 36 is finally here and it is much better than Ubuntu
Ubuntu is a great Linux-based operating system that seems to get all the attention. Truth be told, however, Fedora is the better Linux distribution. Hell, some would argue it is the overall best distro. Quite frankly, if you are an open source champion, you should be using Fedora. It is the perfect no-nonsense distribution, and best of all, it largely focuses on truly free and open source software.
Today, following some delays, Fedora 36 finally becomes available for download. While hardly an exciting update, this new version of the Linux-based operating system is notable for utilizing GNOME 42 and kernel 5.17. Plus, for those using an NVIDIA GPU and driver, you will now get Wayland by default. You can read full release notes here.
Tackling the problems of the future with today's data: What the Government can do to prepare itself
How can we best use data to reach our goals? This is a question that every business and public sector organization often asks themselves. Data is an incredible asset, and Government has some of the richest data sets available. The potential of data to drive efficiencies, improve policy making and, ultimately, drive better outcomes for citizens, is well documented.
The UK Government’s National Data Strategy shows its commitment to placing data at the heart of a concerted national effort to improve citizen services. There are numerous Initiatives focused on helping improve the use of data across government. One such example is the collaboration between the Global Government Forum, the Office for National Statistics, NTT DATA UK, and the Cabinet Office, to produce the Civil Service Data Challenge (CSDC), which pushes data innovation a step further.

What it takes to build a successful remote team in today's climate
You've probably spent the majority of your career in an office. The commute, the quick chats at the coffee maker, the cleanest bathroom on the third floor -- these trivial details became as much a part of your workday as spreadsheets and meetings.
Then, just like that, everything changed. IT teams scrambled to find a secure way to keep people working from home. Managers questioned how to keep productivity up, and the C-suite kept a wary eye over everything (that, at least, didn’t change).

Old botnets make a comeback
Several older botnets have seen a resurgence in activity in the first quarter of 2022, including Mirai, STRRAT and Emotet, according to the latest threat report from Nuspire.
Mirai, known for co-opting IoT devices to launch DDoS attacks and first seen in 2016, showed a spike in activity in February of this year. This corresponded with the discovery of Spring4Shell, a zero-day attack on popular Java web application framework, Spring Core. The attack allows for unauthenticated remote code execution, and data show Mirai exploited this vulnerability to its botnet.
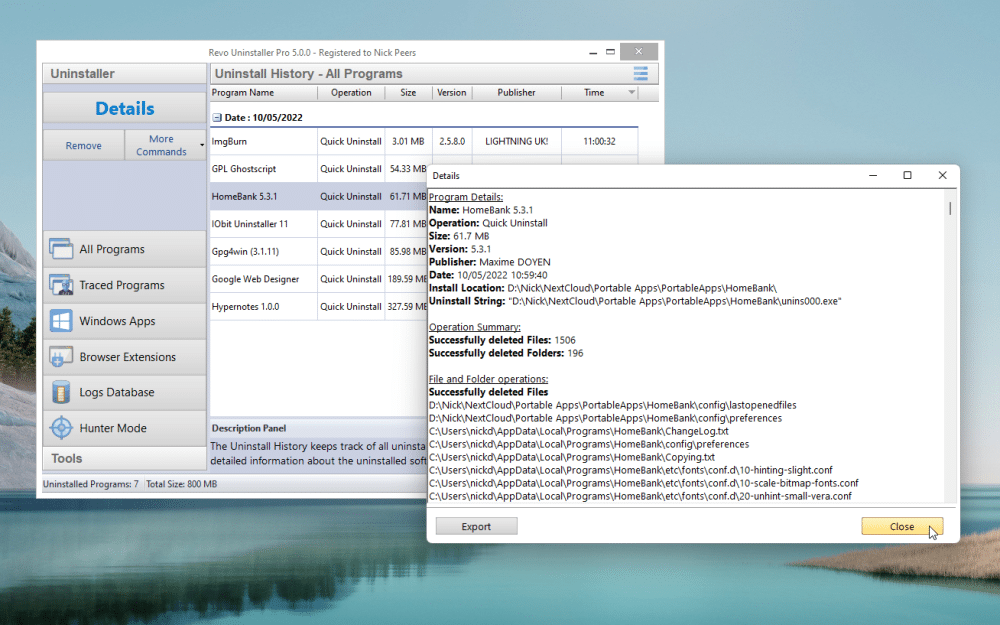
Revo Uninstaller Pro 5 adds uninstall history and dark mode
The VS Revo Group has unveiled Revo Uninstaller Pro 5.0 and Revo Uninstaller Pro Portable 5.0 for Windows PCs. This powerful tool allows users to more thoroughly remove unwanted programs, Microsoft Store apps and other elements (including browser extensions) from their PCs.
Version 5.0 adds new features to allow users to track all previous uninstall operations, more thoroughly clean programs installed across all user accounts and adds support for removing multiple Windows Store apps and browser extensions in a single action.

Enterprises continue to back digital transformation
A new global study reveals that 79 percent of enterprises have made significant, transformative or even revolutionary improvements to the end user experience through digital transformation over the past year.
The research by Couchbase shows a positive outlook too, with enterprises planning to increase their investment in digital transformation by 46 percent over the next 12 months.

Staff at Fortune 1000 enterprises put their employers at risk
A new report has identified over 687 million exposed credentials and PII tied to Fortune 1000 employees, a 26 percent increase over last year's analysis.
The study from SpyCloud, based on its database of over 200 billion recaptured assets, also shows a 64 percent password reuse rate, widespread use of easy-to-guess passwords, and a spike in malware-infected devices.

Microsoft warns against using leaked beta of unreleased One Outlook app for Windows 11
In recent days the yet-to-be-released successor to Windows 11's Outlook app leaked online. Called One Outlook, this unreleased beta version is known as Project Monarch.
This is not the first we have heard of One Outlook; it was originally scheduled for release last year, but the launch was delayed. But the leak was the first time anyone has been able to try out the app, but Microsoft has issued a warning saying that this is an "unsupported early test version" which is missing features.

Majority of Americans fear some form of cyberwarfare
The war in Ukraine has highlighted the role that the cyber world has to play in modern conflict and a new survey from NordVPN finds that 93 percent of Americans believe that another country could launch cyberwarfare against the US.
What's more, of over 1,000 consumers surveyed only 19 percent feel 100 percent confident in the government's ability to protect them, despite the fact that 70 percent rank the US as the most secure country for cyber war attacks.

Microsoft to release fix for 'code defect' in KB5012599 update for Windows 10
Last month, we wrote about problems experienced by some Windows 10 users who installed the KB5012599 update -- specifically 0x8024200B and 0x800F0831 errors.
While the problems are yet to be publicly acknowledged by Microsoft or added to the list of known issues with the update, the word is that a fix is on the way very soon. Sysadmins that have contacted Microsoft have been advised that a patch is "on track" for delivery this week, with the company blaming a "code defect" for the problems.

The CSO's new seat at the executive table and how to use it [Q&A]
With the changes to working patterns brought about by the pandemic and increasing levels of cyberattacks, the role of the Chief Security Officer (CSO) in businesses has become more challenging.
These things have also led to a boost in the status of CSOs within their organizations. We spoke to Chaim Mazal, CISO and SVP of engineering for Apple device management platform Kandji to find out more about how things have changed and how CSOs can make the most of their new influence to drive security strategy.

The great balancing act: How to manage your workloads amidst ongoing change
Amidst the ongoing skills gap and permanent move to hybrid working, workloads are continuing to grow. Two and a half quintillion bytes of data are generated every day, often scattered between the cloud, data silos, and on-premises storage as employees work from a range of locations. Although this flexible approach to working has many benefits -- increased productivity, improved employee wellbeing, and a better work-life balance -- it also can create a sprawl of data.
Left unattended and unmonitored, workloads stack up and enterprises are left with a balancing act to manage data stored in multiple places. Whilst this can be maintained in the short term, it is not sustainable in the long term and will eventually spill over. Many will remember offices before the widespread use of computers and technology, when stacks of paper were piled up on desks and filing cabinets were full to the brim with important documents. Trying to find the single piece of paper with the information you needed was a difficult task that wasted valuable time. Having a disparate IT environment has a similar impact on today’s business operations.
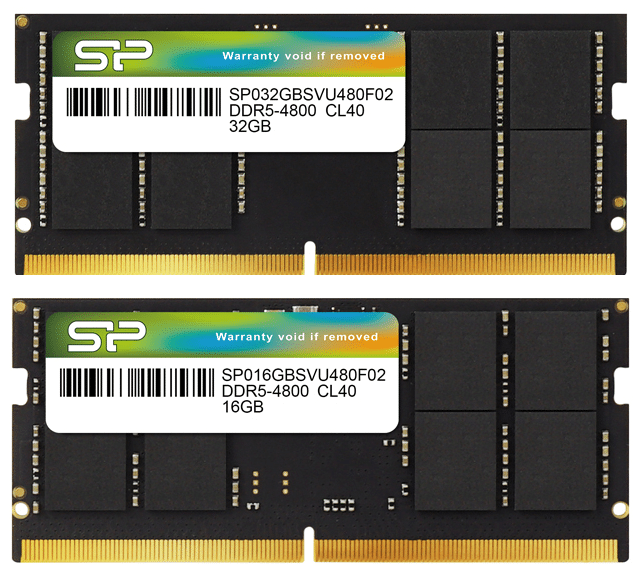
Silicon Power launches SO-DIMM DDR5 laptop RAM with 4,800MHz clock speed
When you are a computer enthusiast or PC builder, there are peaks and valleys when it comes to excitement about internal components. Sometimes you are using desktops and/or laptops with bleeding-edge parts as an early adopter, while other times you are using ho-hum components that have been around a while. For instance, we have been using DDR4 memory for approximately seven years now.
Thankfully, the age of DDR5 is finally here, y'all! After dealing with DDR4 for so many years now, we are finally seeing PCs with DDR5 memory inside -- including laptops and mini desktop PCs that use SO-DIMM sticks. Today, Silicon Power unveils some really cool DDR5 notebook memory. This laptop/mini desktop RAM runs at an impressive 4,800MHz and comes in capacities ranging from 8GB (single stick) to 64GB (2x32GB).

Countering the risk of ransomware with operational continuity
In recent years, organizations all over the world have been hit by increasingly sophisticated ransomware attacks. For some, the impact is so severe that normal business operations experience major disruption with a knock-on effect on customers and revenue. For others, the impact can last weeks or even months as they seek to restore IT services and access to vital data.
Since the start of last year, for example, organizations across a huge range of sectors -- from oil and gas to food -- have seen their services impacted by ransomware. KP Snacks suffered an incident that brought its supply chain to a halt, with the company unable to process orders and dispatch products. And most recently of all, The Works, a retailer with over 500 stores across the UK, was forced to close some outlets after an employee reportedly fell victim to a phishing email that introduced ransomware to their infrastructure.

How to continue the growth of open source in the UK
Open source adoption rates are growing globally, with non-propriety code proving to be both efficient and cost-effective for a variety of organizations. Approximately 82 percent of IT decision-makers are more likely to choose a vendor that actively gives back to the open source community, according to a recent report from Red Hat. In the UK in particular, much of the reason for this open source drive is down to increased public cloud usage, the growing demand for rapid digital transformation and a greater understanding of open source’s cybersecurity resilience.
To help continue this open source upsurge in a sustainable manner, organizations utilizing the technology need to be contributing back to the community, to best enable the development of the technology.



