
91 percent of organizations experience software supply chain incidents
The overwhelming majority of organizations (91 percent) have experienced a software supply chain incident in the past 12 months, according to a new report.
The study from Data Theorem and the Enterprise Strategy Group surveyed over 350 respondents from private- and public-sector organizations in the US and Canada across cybersecurity professionals, application developers and IT professionals.

From complexity to clarity: Managing IT landscapes in a hybrid cloud world
IT plays a key role in achieving sustained business success against a backdrop of constantly changing industry and economic challenges. Today’s IT systems not only underpin business operations but enable the projects and initiatives that deliver on every aspect of a company’s business strategy.
Over the last five years, there has been a significant transformation in the business systems and IT landscapes that IT teams are required to manage. The COVID 19 pandemic played a large role in this shift, with businesses having to rapidly incorporate new capabilities to facilitate remote work and maintain daily operations. Over time, these ‘temporary solutions’, plus others that have been implemented since, have become embedded in many organizations.

CIOs: Don't let the cost of cloud migration hold you back
In 2024, one fact is clear: The cloud aids business success. Cloud migration isn't just an operational upgrade but a highly strategic financial strategy capable of unlocking up to $1 trillion in business value. Cloud benefits extend from reduced operating costs -- including infrastructure, labor and energy expenses -- to enhanced scalability and operational efficiency.
Most organizations have caught on to these benefits. Today, more than half of all corporate data exists in the cloud, up from 30 percent in 2015. This dramatic shift illustrates the cloud's crucial role in modern data management and sets the stage for a long-overdue discussion of the cloud's financial implications.

Cisco adds new AI and security innovations
Security and networking specialist Cisco is announcing changes to its Cisco Security Cloud as part of its mission to simplify security.
Cisco Identity Intelligence -- available from July this year -- will run on top of customers' existing identity stores and provides unified visibility, as well as AI-driven analytics.

Enterprises hang onto mainframes as migration strategies shift
A new report suggests that faced with mounting competition and economic uncertainty, 92 percent of global enterprises are changing course to retain mainframes as part of pragmatic hybrid strategies, rather than pursuing wholesale cloud shifts.
The latest Mainframe Modernization Business Barometer Report from Advanced, based on a survey of 400 IT leaders worldwide, reveals hybrid infrastructure strategies taking hold to balance workloads across cloud and mainframe. In fact, only six percent expect outright mainframe replacement anytime soon.

Top 4 cloud trends that will affect your business in 2024
Over recent years, Cloud computing has boomed in popularity, receiving a global spend of $55.9 billion within the first quarter of 2022, and then by Q3 2023, it had reached $73.5 billion, a 16 percent rise year on year according to research by Canalys. As well as that, Statista had also conducted a survey that investigated the increase use of cloud services and discovered that storing and creating files and office documents was the main reason for implementing cloud technology to their business.
Businesses that utilise cloud services to their full potential can gain a helpful push towards a more digital direction. But like all technology, it will continue to evolve and provide new ways of making your processes more efficient.

Companies put convenience and speed above security in app deployments
A new report from cloud security company Sysdig reveals that many businesses are indulging in the dangerous practice of putting convenience before preventive security in pursuit of faster application development.
"Attackers are leveraging automation to exploit every point of weakness they can uncover," says Crystal Morin, cybersecurity strategist at Sysdig. "This year's report shows that many companies are chasing faster innovation at the cost of more comprehensive security -- a gamble that poses real business risks."
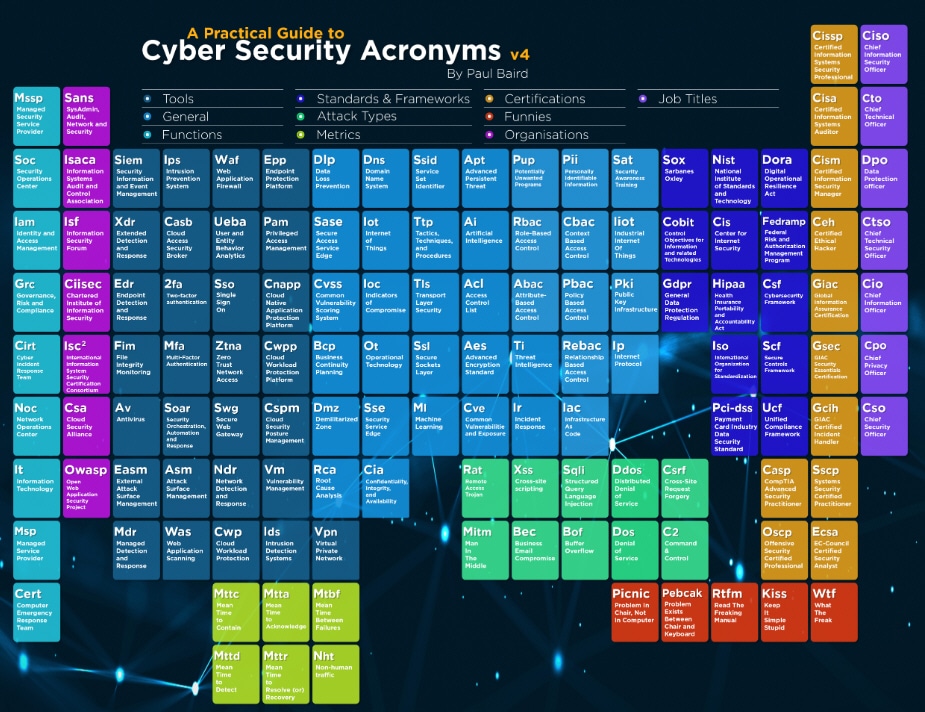
Making cybersecurity elementary [Q&A]
There are so many terms and acronyms used in the cybersecurity sector that it can be a little overwhelming at times, even for people who work in the industry.
Paul Baird, director of cyber security operations and engineering at Advanced Software and fellow at the Chartered Institute of Information Security (CIISec) has produced a round up of all the terms that you might ever need to know in the security space in a format based on the periodic table of elements.

Securing the cloud: Lessons learned from 2023 and what it means for 2024
The global cloud computing market is expanding rapidly and reaching new milestones every year. According to recent data, the market is projected to grow from USD 626.4 billion in 2023 to USD 1,266.4 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 15.1 percent during the forecasted period.
The industry's rapid financial growth is also driving new technological advancements. With this, the dynamic and innovative nature of cloud technology brings new security vulnerabilities and risks, thereby every year increasing the number of malicious incidents. According to the 2023 Thales Cloud Security Study, more than a third (39 percent) of businesses experienced a data breach in their cloud environment last year, an increase from the 35 percent reported in 2022. The leading targets for hackers were Software as a Service (SaaS) applications (38 percent) and cloud-based storage (36 percent).

SecurityScorecard launches industry-specific ratings for the telecoms sector
Some industries make more attractive targets for cybercriminals than others, thanks to the type of data they hold and the services they provide. The telecoms sector is one such. 85 percent of the top telecom companies in the US, UK, France, Italy, Denmark, and Germany experienced a third-party data breach in the past 12 months alone.
Which is why SecurityScorecard is introducing a new set of security ratings developed especially for telecommunications companies, internet service providers, and cloud providers.

Don't risk falling behind when it comes to cloud security
Cloud investment is central to staying competitive in modern business. Gartner estimated that global end-user cloud investment reached nearly $600 billion this year and forecasts a 20 percent increase in spending in 2024. But as investment in and reliance on the cloud increases, so must investment in cloud security.
Expanding cloud usage means an expanding attack surface for threat actors to target. Research from Vanson Bourne, commissioned by Illumio, found that nearly half (47 percent) of all security breaches now start in the cloud.

Selecting the right storage for SQL Server high availability in the cloud
When it comes to the type of storage you might use for a cloud-based SQL Server deployment, all the major cloud providers provide a bewildering array of options. Azure offers Standard HDD as well as Standard SSD, Premium SSD as well as Premium SSD v2. Oh, and then there’s Ultra Disk. And AWS? The options are no less eye-glazing: ST1 and Standard, GP2 and GP3, IO1 and IO2.
Even if you could easily differentiate the offerings, what would be your best choice if you plan to configure your infrastructure for high availability (HA) -- by which we mean an infrastructure designed to ensure that your SQL Server database will be available and operating no less than 99.99 percent of the time?

Get 'Cloud Native Software Security Handbook' (worth $35.99) for FREE
For cloud security engineers, it’s crucial to look beyond the limited managed services provided by cloud vendors and make use of the wide array of cloud native tools available to developers and security professionals, which enable the implementation of security solutions at scale.
Cloud Native Software Security Handbook covers technologies that secure infrastructure, containers, and runtime environments using vendor-agnostic cloud native tools under the Cloud Native Computing Foundation (CNCF).

Consolidation of products, closer attention to security and cost increases -- cloud predictions for 2024
The cloud has become a familiar feature of most computing environments over the last decade, but that doesn't mean that the technology is standing still.
Here are some industry expert views on what we can expect from the cloud scene in 2024.

Use of distributed cloud expected to rise over the next year
Both developers and decision makers are seeing a shift in the market towards a more decentralized cloud, according to new research.
The study from Akamai, in partnership with ClearPath Strategies and SlashData shows 55 percent of developers already actively work on distributed cloud architectures, 87 percent of ITDMs expect their use of the distributed cloud to increase over the next 12 months.
