
Organizations can only stop 57 percent of cyberattacks
Over the last two years, the average organization's cybersecurity program was prepared to preventively defend against, or block, just 57 percent of the cyberattacks it encountered. This means 43 percent of attacks launched are successful and need to be remediated after the fact.
This is among the findings of a new report from Tenable, based on a survey of over 800 IT and cybersecurity leaders carried out by Forrester Consulting.

Over half of enterprises struggle to get insights from their data
Research released this week from Hitachi Vantara shows 55 percent of enterprises are struggling to derive meaningful insights from their data.
The survey of over 200 IT leaders across North America and Europe, carried out by Forrester Consulting, reveals ongoing challenges related to security, inflexible systems, isolated data, a skilled labor shortage, and the need for infrastructure agility.

New service aims to make cloud more accessible
With so many different platforms and technologies available, navigating the world of cloud computing can be tricky.
In a bid to make things simpler Acorn Labs is announcing public beta availability of its cloud developer platform Acorn, a service that makes it simple for anyone to run software in their own cloud sandbox and easily share their creations.

Cloud management skills gap holds back growth
A new study of over 800 IT professionals across the US, UK and Germany finds that 72 percent of mid-size companies report a lack of cloud management skills as being a barrier to their growth.
The study from Parallels finds 64 percent of respondents have already implemented a hybrid approach, and 38 percent of all respondents plan to further embrace a hybrid cloud approach in the next year.
GPU revolution: Harnessing the power of advanced technology through cloud delivery
Recent advancements in GPU (Graphics Processing Unit) technology, accompanied by new innovative use cases and increased user expectations have produced a profound impact on the industry. Together, they have driven the proliferation of new application architectures, fueling growth in artificial intelligence (AI), machine learning, and visual computing.
In this era of relentless innovation, the key to staying competitive lies in quickly meeting user expectations through cloud delivery. Its multiple advantages -- on-demand consumption, scalability, global availability, a safeguard against supply chain disruptions, and financial perks -- shape a compelling strategy for deploying GPU technology via the cloud.

Mastering cloud cost optimization: Strategies for efficiency and resiliency
In an era driven by digital transformation, cloud computing has emerged as a game-changer for businesses of all sizes. However, as cloud adoption continues to soar, so does the need to manage cloud costs effectively. Balancing cost reduction with maintaining and increasing resiliency has become a top priority for businesses seeking to maximize the benefits of the cloud.
The need to optimize is evident, but achieving this goal can be complicated. Without appropriate cost containment and governance strategies, organizations risk falling into a continuous climb spend pattern. Often, businesses address cost optimization as a sporadic, reactive exercise -- like making annual bulk purchases of reserved instances. To break free from this cycle and achieve sustained cost efficiency, a shift towards a collaborative, ongoing and iterative approach to cost optimization and management is a key priority.

Cloud vs. on-premises: Unraveling the mystery of the dwell time disparity
In the ever-evolving realm of the cloud, dwell times are now measured in moments, not days. Whereas Mandiant’s 2023 M-Trends report highlighted a global median dwell time of 16 days for on-premises environments, the Sysdig Threat Research Team (TRT) recently reported in their 2023 Global Cloud Threat Report that cloud dwell time is five minutes.
To better understand the stark difference between defenders' abilities to find attackers in the cloud and on-premises, I sat down with the Sysdig TRT to discuss their findings. They circled around four distinct, but closely related reasons.

Seven steps to successfully migrate your enterprise data to the cloud
Amidst a challenging economic climate many businesses are unsurprisingly reviewing their spending, with research from the Institute of Directors finding most businesses are unlikely to increase investment over the next 12 months.
One area currently bucking this trend is the cloud. Research shows almost half of tech and business leaders are increasing investment in cloud-based products and services, and a third of them plan to migrate their legacy enterprise software and on-premises workloads to the cloud.

How careful cloud migration can help your business tighten its belt
Today’s enterprises are grappling with a very modern IT dilemma: how to carry out cloud migration as cost-effectively as possible.
According to recent research on the views of IT leaders, more than half of enterprises worldwide (55 percent) believe a move to the cloud is "inevitable." The benefits of migrating to the cloud are now widely-acknowledged -- from replacing unreliable legacy infrastructure that hinders business agility, to providing support for modern, collaborative workloads. Many enterprises’ eagerness to adopt AI technologies is also driving cloud migration. This is because the cloud offers the computing power required to deploy AI models at scale.

UK regulator to investigate hyperscalers' dominance of the cloud market
The UK's Competition and Markets Authority (CMA) is launching a market investigation into the supply of public cloud infrastructure services in the UK. Between them, Amazon and Microsoft enjoy a combined market share of 60-70 percent of Britain's cloud computing industry.
This follows a referral by telecoms regulator Ofcom which has expressed concerns around egress fees, discounts -- which may incentivize customers to use only one cloud provider, and technical barriers to switching.
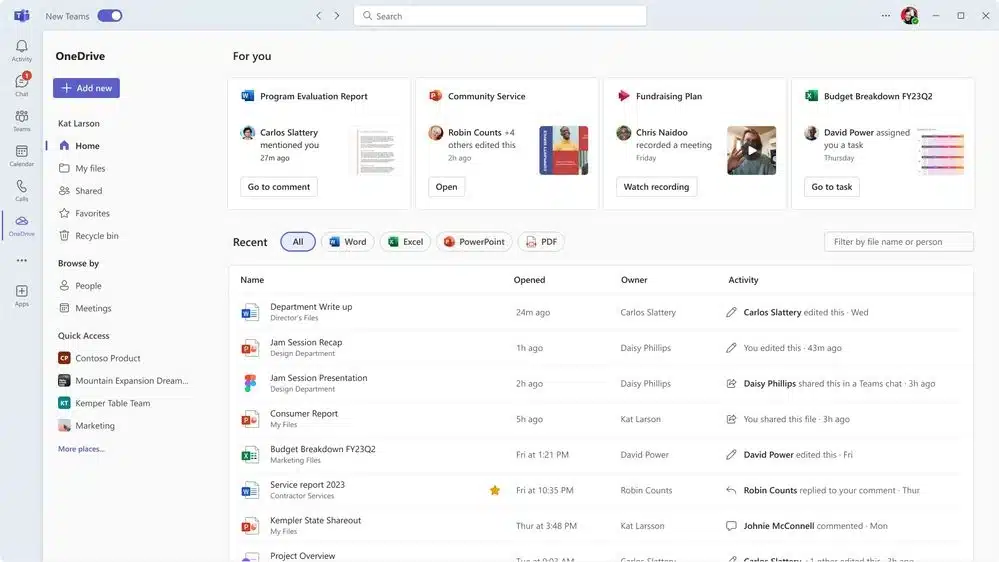
Microsoft unveils the next generation of OneDrive with a massive update of its cloud storage service
Microsoft is updating OneDrive as part of a major revamp of the cloud storage service. With the third generation of OneDrive, there are not only visual changes, but also new tools and features to use along with, almost inevitably, a dash of AI courtesy of Copilot.
Described as heralding the "future of file management”, Microsoft's OneDrive update includes a redesign home experience to help speed up finding what you need. File sharing has been simplified, there is better offline support, and there are numerous performance enhancements. What is currently rolling out is only the beginning; Microsoft promises even more tools and features soon.

The battle for control of cloud environments [Q&A]
Lack of control has long been a pain point for developers in cloud computing, especially with the market dominated -- and controlled -- by a few large providers.
What's likely to happen as developers' desire for control meets the hyperscalers' desire to keep companies locked into their platforms? We spoke to Billy Thompson, solutions engineering manager at Akamai, to find out.

IT and finance battle for control of cloud spending
A tug-of-war between finance and cloud leaders is preventing enterprises from controlling their cloud spending, according to new research.
The study from Vertice, of 600 senior finance and tech leaders in the US and UK, shows cutting cloud spending is revealed as the number one cost-saving priority for over a third of finance leaders, but only nine percent of technical leaders say that managing cloud costs is a top concern.

CSPs align with enterprise cloud strategies
Cloud transition plans have dominated the CISO agenda for the past decade, accelerated by the rapid shift to working remotely. Now, cloud infrastructure and strategies have moved far beyond the initial reactive approach of the last few years and into a revenue-generating, proactive investment for all modern businesses. Communications service providers (CSPs) are aligning their services and networks to support this trend and most are reporting a positive outcome related to the cloud transition of their enterprise customers.
As technology evolves and digital transformation plans continue to accelerate, enterprises that want to stay competitive are transitioning a portion of their infrastructure to the cloud, focusing on finding the right mix of cloud services to support their mix of applications as well as their current and future plans. These enterprises are looking to communications service providers to help them manage a complex multi-cloud environment as well as including CSP cloud services in that mix.

CISOs see budgets increase despite economic slowdown
A new report from Team8 shows that 56 percent of CISOs have had budget increases since 2022 despite the economic slowdown, while 25 percent saw no change and 19 percent cuts.
However, larger security departments have been most affected by budget cuts with 67 percent of those with 51-100 people seeing budget reductions.
