
96 percent of organizations worry about the impact of shorter certificate life
The radical shortening of SSL/TLS certificate lifespans from 398 days to 47 days by 2029 is shaking up the cybersecurity world. New research shows 96 percent of organizations are concerned about the impact of shorter SSL/TLS certificate lifespans on their business.
The study from Sectigo, developed in collaboration with global research firm Omdia, surveyed over 270 IT decision makers and finds fewer than one in five organizations feel very prepared to support the coming shift to 47-day certificate renewal cycles.
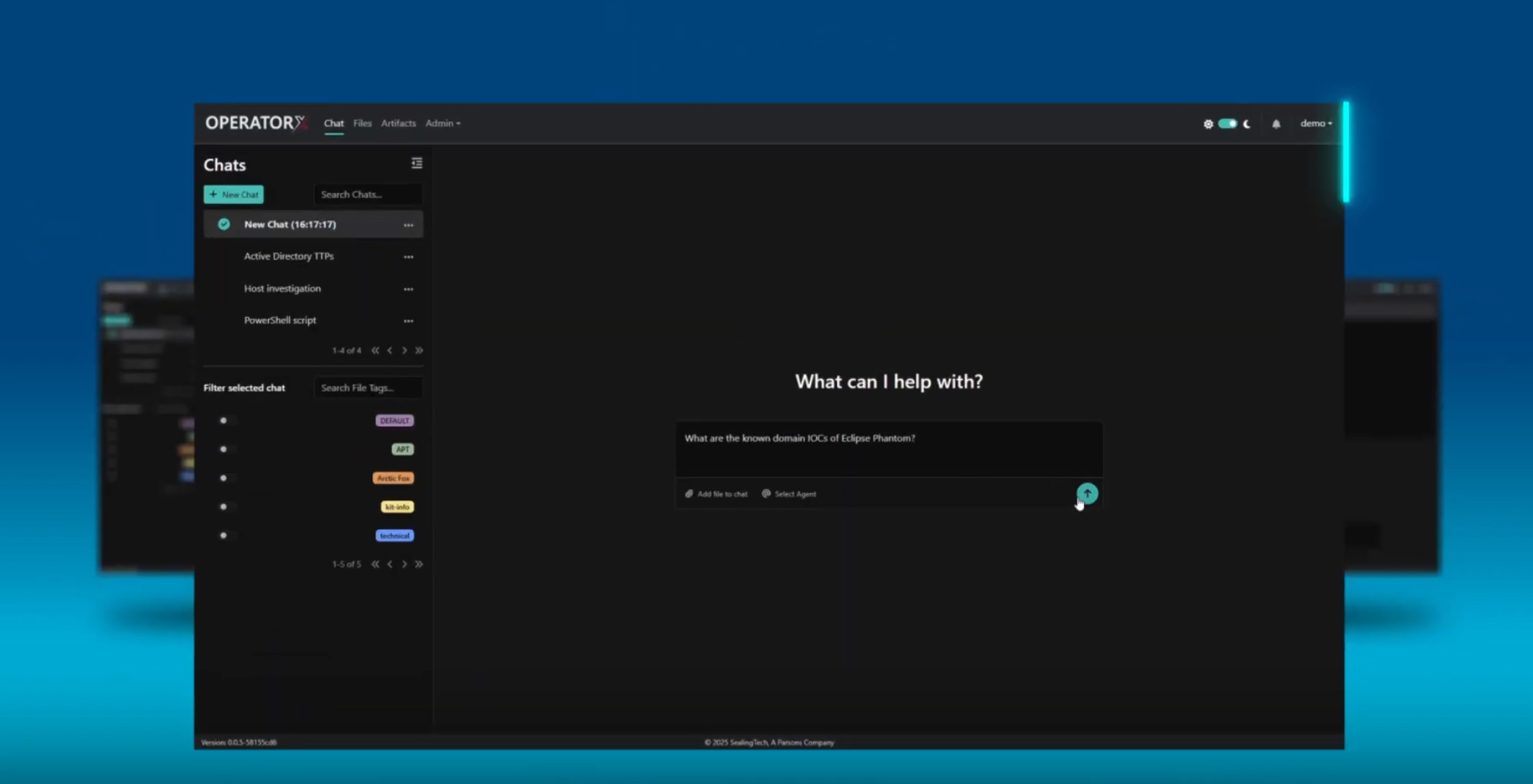
New AI-powered Operator X streamlines offline defensive cyber missions
Sealing Technologies has launched Operator X, an AI Hunt Kit Assistant built for defensive cyber operations at the edge.
Operator X is designed for situations where you can’t rely on the internet or external cloud services. Many cyber defense teams work in places where security rules are very strict, so sending sensitive data to a cloud provider is not allowed. In those cases, everything has to run locally, inside the secure environment.

Insecure code is behind a wave of data breaches
New research reveals that insecure code is behind a shocking number of cyber breaches in the UK, with two-thirds of tech leaders admitting their organization suffered an incident in the past year.
The study from SecureFlag, of 100 UK C-suite and tech leaders, shows that despite the risks, many companies are still failing to train developers properly, leaving a gap that attackers are exploiting.

How the SOC is evolving to meet new threats [Q&A]
As cybersecurity threats grow more sophisticated and relentless, the role of the Security Operations Center (SOC) has never been more critical.
In response organizations are re-imagining their SOCs to address the dual challenges of an evolving threat landscape and a shifting workforce dynamic. We spoke to Scott Scheppers, chief experience officer at LevelBlue to find out more about this shift and how SOC teams are pivotal in safeguarding operations, fostering innovation, and mentoring the next generation of cybersecurity talent.

Malicious URLs overtake attachments as top email threat
Cybercriminals increasingly favor malicious URLs over attachments, as they are easier to disguise and more likely to evade detection, according to the latest report from Proofpoint.
These links are embedded in messages, buttons, and even inside attachments like PDFs or Word documents to entice clicks that initiate credential phishing or malware downloads.

Dealing with the challenge of securing machine identities [Q&A]
Machine identities have proliferated in recent years, but while they offer convenience they also introduce new vulnerabilities.
We spoke to Ev Kontsevoy, Teleport CEO, to learm more about the problem of securing machine IDs and what enterprises can do to address it.

Enterprises struggle with too many identity tools
With identity security growing more complex a new report shows that of 70 percent of enterprises recognize the need to consolidate their identity security tool stack.
The study by Enterprise Strategy Group for Silverfort finds that while 70 percent of teams plan to expand their use of an existing tool to cover a new use case in the next 12-18 months, 62 percent of organizations plan to implement a new tool to satisfy a use case, hinting that current solutions may not be adequate to satisfy evolving priorities.

Over 80 percent of organizations knowingly ship vulnerable code
New research shows 81 percent of organizations knowingly ship vulnerable code, and 98 percent experienced a breach stemming from vulnerable code in the past year, that’s a sharp rise from 91 percent in 2024.
The survey from Checkmarx, of more than 1,500 CISOs, AppSec managers and developers around the world, also shows that AI‑generated code is becoming mainstream, but governance is lagging.

Shifts in federal cyber priorities put stress on security teams
Recent shifts in US federal cybersecurity efforts, most notably cuts to key CISA programs and the disbanding of the Cyber Safety Review Board, are having an impact beyond Washington according to a new report.
Security automation company Swimlane surveyed 500 IT and security decision-makers across the US and UK The findings show how private-sector leaders are now shouldering greater responsibility for resilience, investment and public‑private coordination.

Why browser security is increasingly essential for the enterprise [Q&A]
As enterprises embrace hybrid work, SaaS applications, and AI tools at unprecedented scale, one critical access point is being increasingly targeted by attackers: the browser.
To better understand the risks and what can be done to secure the browser, we spoke with Alon Levin, vice president of product management at Seraphic Security, and an expert in enterprise browser security.

How access to company networks is sold on the dark web for under $1,000
New analysis of illicit dark web marketplaces where cybercriminals buy and sell access to corporate networks uncovers new insights into how initial access to compromised businesses is being sold -- often for less than $1,000 -- and the steps defenders can take to disrupt the process in its earliest stages.
Rapid7’s threat intelligence researchers analyzed hundreds of posts by Initial Access Brokers (IABs) offering access to compromised networks across a range of industries and regions. Their findings show that ‘initial’ access doesn’t necessarily equate to minimal; in many cases, this access represents a deep compromise.

Spread of AI agents sparks fears of a cybersecurity crisis
A new report reveals an increasing trust gap between businesses deploying agentic AI for external communications and consumers wary of sharing personal information due to security concerns.
The research, carried out by Censuswide for Salt Security, also warns that without proper API discovery, governance and security, the very technology meant to drive smarter customer engagement could open the door to cybersecurity issues including attacks or data leakage.
Ransomware attacks up by 41 percent globally
New data from Check Point Research reveals a sharp rise in cyberattacks globally, with business services, healthcare, and manufacturing among the hardest hit sectors.
Ransomware incidents in particular have surged, with 487 attacks reported in July, a 41 percent increase year-on-year. North America accounted for 56 percent of all reported ransomware cases, followed by Europe at 24 percent.

Threat actors move to smaller more persistent attacks
Threat actors are favoring smaller, persistent attacks under 100,000 requests per second according to a new report. This shift signals a growing dependence on automated, generative AI-enhanced attack tools, reflecting the democratization of DDoS capabilities among loosely coordinated threat actors and new actors entering the scene.
The report from Radware also shows web DDoS attacks rose 39 percent over the second half of 2024. The second quarter set a record with a 54 percent quarter-on-quarter spike.

Why effective exposure management is key to cybersecurity [Q&A]
Thanks to the rise of hybrid working and SaaS the traditional concept of ‘attack surface’ -- limited to hardware, software, and network infrastructure -- is dangerously outdated and no longer sufficient to ensure cybersecurity.
We spoke to Mike Riemer, senior vice president Network Security Group and field CISO at Ivanti, to find out how organizations need to adapt to keep their systems secure.
