
Walmart's cybersecurity: Don't try this at home
It seems that every week we hear of another cybersecurity breach. This year, organizations of all shapes and sizes have fallen victim to malicious crimes -- from Apple, T-Mobile and Uber, among many others -- and data breaches are costing U.S. businesses millions of dollars.
The emerging digital ecosystem has made every company a target, and as a result, organizations are investing in a range of cybersecurity measures to mitigate threats and enhance resiliency and recovery. As cybercriminals continue to evolve their tactics, it’s becoming increasingly challenging for organizations to keep up with the latest security measures. This highlights the need for ongoing cybersecurity investment and a proactive approach to threat detection and response. The question is, what are these measures, and is there a one-size-fits-all approach? Let’s explore.

The challenge of protecting data in the cloud [Q&A]
Modern enterprises hold huge volumes of data and increasingly it's stored in the cloud. This means that protecting the information is a significant challenge and it can even be easy to lose track of where data is.
We spoke to Dan Benjamin, co-founder and CEO of Dig Security, to discuss the risks around cloud data storage and how to address them.

Google Drive security flaw allows data to be stolen without trace
Cloud incident response company Mitiga has released research on a significant forensic security deficiency in Google Workspace that enables threat actors to exfiltrate data in Google Drive without any trace.
Data theft is one of the most common motives for attack, and with more than six million businesses using Google Workspace -- including Google Drive -- the cloud-based repository has been a prime target for data exfiltration.

77 percent of UK citizens are concerned about online privacy
A new survey shows that 77 percent of people in the UK are concerned about the privacy of their data online, but 15 percent don't do anything at all to protect themselves online.
The study, carried out for Proton by YouGov, reveals concern is even greater among those who have been a victim of a hack, or know someone who has.

Think you can spot a deepfake? Think again
A new study from Jumio reveals that 52 percent of global respondents believe they could successfully detect a deepfake video.
However, the report's authors believe this reflects over-confidence on the part of consumers, given the reality that deepfakes have reached a level of sophistication that prevents detection by the naked eye.

90 percent of organizations have had identity-related incidents in the past year
In the last 12 months, 90 percent of organizations have suffered an identity-related incident, an increase of six percent over the previous year.
A new report, based on an online survey of over 500 identity and security professionals, from The Identity Defined Security Alliance, shows that only 49 percent of respondents say that their leadership teams understand identity and security risks and proactively invest in protection before suffering an incident, while 29 percent only engage and support after an incident.

The key to an effective generative AI strategy: Human oversight
Generative artificial intelligence (AI) systems have witnessed significant advancements in recent years, offering remarkable capabilities in a variety of domains.
Generative AI is a powerful tool that can be used for both good and bad. Threat actors have been employing the latest technology to harm businesses in various ways for decades, but organizations have and must continue to find ways to use this same technology to their advantage, and ultimately outsmart these digital thieves as AI is becoming more accessible and accepted.
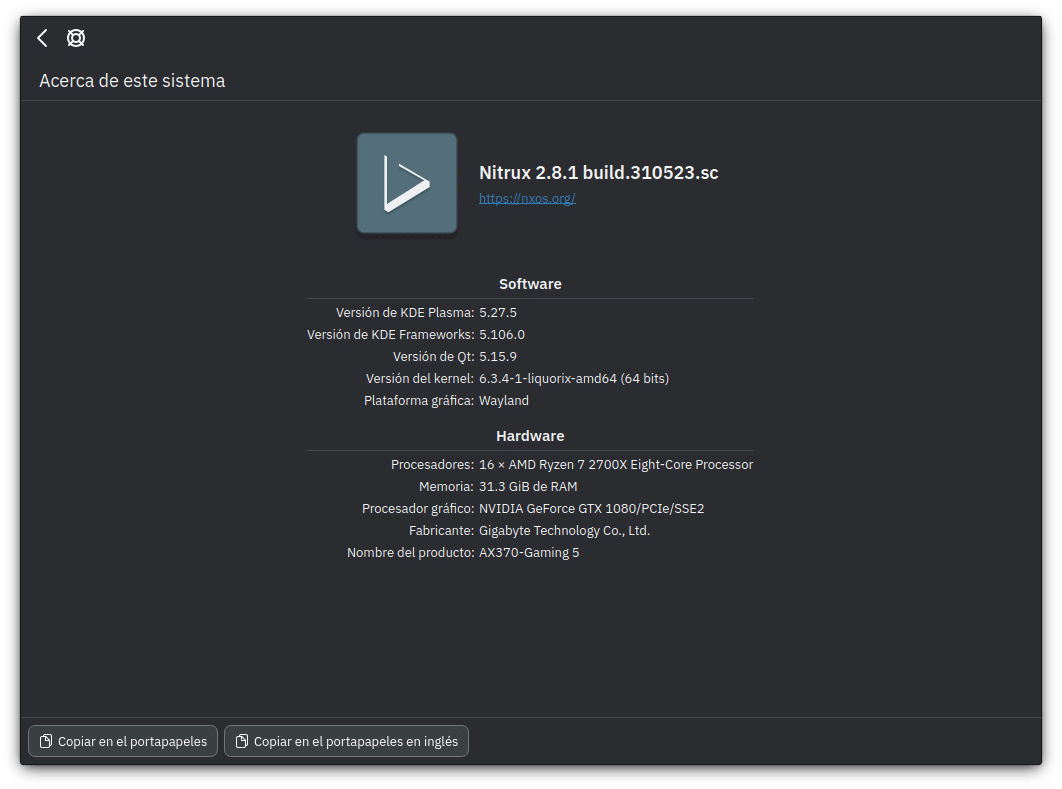
Nitrux 2.8.1 Linux distribution unleashes supercharged security and privacy powers
Nitrux 2.8.1, codenamed "sc" for "safer computing," has been released, offering enhanced privacy and security features. While the distribution does not claim to be impenetrable or unhackable, it aims to protect users' privacy and provide tools for online anonymization. The release is made possible through collaboration with packagecloud, which provides the necessary infrastructure for building the distribution.
New users are advised to perform a fresh installation using the latest media. For existing users of version 2.8.0, it is recommended to review the release notes for specific instructions. Notably, Nitrux 2.8.1 employs Linux 6.3.4-1 (Liquorix) as its kernel.

Cybercriminals increasingly using legitimate websites to hide malicious payloads
A new report shows a 121 percent increase in cybercriminals using legitimate websites to obfuscate malicious payloads.
The report from Egress, based on data from its Egress Defend cloud email security solution, shows YouTube, Amazon AWS, Google Docs, Firebase Storage, and DocuSign to be the top 10 most frequently used sites.

Advanced phishing attacks grow 365 percent
A new report has identified a 356 percent growth in the number of advanced phishing attacks attempted by threat actors in 2022.
The study from threat detection specialist Perception Point also shows that the overall number of attacks increased by 87 percent.

Cyber insurance gets more expensive as ransomware attacks target backup storage
A new report reveals that 93 percent of ransomware attacks are now targeting backup storage as a way of ensuring payment.
The report from Veeam also shows that the success of attacks is having an impact on enterprises' ability to get insurance cover. 21 percent of organizations say that ransomware is now specifically excluded from their policies.

Half of organizations fell victim to spear phishing in 2022
The latest spear phishing trends report from Barracuda Networks shows that 50 percent of organizations studied were victims of spear-phishing in 2022, with 24 percent having at least one email account compromised through account takeover.
The report draws on a data set that comprises 50 billion emails across 3.5 million mailboxes, including nearly 30 million spear-phishing emails, as well as a survey by Vanson Bourne of IT professionals from frontline to the most senior roles at 1,350 companies.

Cybersecurity in the utility space isn't just about keeping the lights on, it's about saving lives.
Russia’s invasion of Ukraine in February 2022 signaled many things to the Western world, but perhaps one of the biggest warnings was how precarious energy security really was as oil and gas prices skyrocketed following the start of the war.
As Europe entered winter and the demand for energy increased, it highlighted just how vicious the cycle can be as cyber attacks on critical infrastructure and operation technology increased.

Email is seen as the enterprise channel most vulnerable to attacks
The majority of organizations use six or more communication tools, across channels, with email being the single channel seen as the most vulnerable to attacks.
Of those responding to a new survey by Enterprise Strategy Group (ESG) and Armorblox of almost 500 IT and security professionals, 38 percent see email as the most vulnerable channel.

How DevSecOps can mitigate the cyber risks of emerging technologies [Q&A]
The technology world never stands still for very long and as new technologies emerge so too do new threats. With things like quantum computing on the verge of becoming mainstream it's important to understand their security implications.
We spoke to Archie Agarwal, founder and CEO of ThreatModeler to discuss how DevSecOps can help to identify and mitigate these new threats to cloud services.
