
Chaos engineering platform improves Kubernetes container reliability
Kubernetes is one of the leading choices for container users, but its benefits of scalability and abstraction also lead to increased complexity, which can make companies reluctant to deploy the technology.
Chaos engineering platform Gremlin is launching support for Kubernetes -- Docker support was launched last year -- so engineers can now use Gremlin to automate the process of identifying and targeting Kubernetes primitives such as nodes and pods, to find issues that can prove difficult to pinpoint at a given moment.

Consumers worry about fraud risk from support desk calls
Almost a third of US consumers (31 percent) think they are at risk of fraud when contacting a brand's customer service department, with 47 percent saying it's because they have to share personal information with a customer service agent.
In another report released for International Fraud Awareness Week, the Sitel Group and CallMiner have looked at consumers' experience and concerns around customer service fraud, voice assistants and information security.

Poor security habits leave Americans vulnerable to fraud
Despite high profile data breaches in 2019 and 33 percent of respondents having been a victim of fraud or identity theft, when asked if they update or change passwords following a data breach at a firm they deal with, 28 percent say only sometimes and nine percent say they don't update their passwords at all.
This is one of the findings of a Shred-it report for International Fraud Awareness Week which highlights the need for improvements in both digital and physical security.

Database containing details of nearly half a million gamers exposed in security lapse
Wizards of the Coast -- publisher of, among other titles, Magic: The Gathering -- has confirmed a security incident that exposed information relating to 452,634 players.
The company left a backup database containing gamer information in a public Amazon Web Services storage bucket where it was accessible from early September. Specifically, the database was used to house data relating to the game's online portal, Magic: The Gathering Arena.

Almost three quarters of retailers have been victims of cyberattack
Some 72 percent of retailers globally have experienced a cyberattack, with 61 percent experiencing one in the last year, yet 50 percent don't have a response plan in place to deal with data breaches.
This is among the findings of a new study carried out by the Ponemon Institute for Keeper Security, which also shows the average cyberattack on a retailer involving the loss of customer/employee data results in 7,772 individual records lost or stolen, with an average price tag of $1.9M from the disruption of normal operations.

Consumers put banks in the frame for holiday shopping fraud
As we head into the peak holiday shopping season, 66 percent of Americans believe they could easily become a victim of fraud, while another 65 percent think they are at a higher risk of having their financial information exposed as a result of their holiday shopping.
A new report from digital risk protection company Terbium Labs also shows that 68 percent would hold their bank at least partly responsible for fraudulent activity, no matter how the compromise occurred.
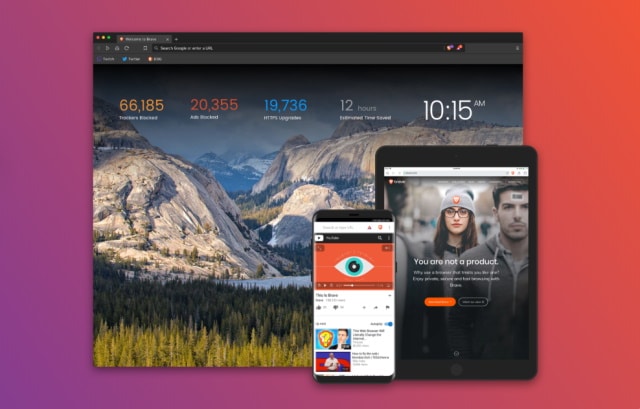
Privacy-focused web browser Brave exits beta for mobile and desktop
Brave, the open-source web browser which focuses on speed, security and privacy, has officially hit version 1.0 and exited beta.
Available for Windows, macOS, Linux, Android and iOS, Brave boasts that it "blocks ads and trackers that slow you down and invade your privacy". The official launch comes three years after Brave first entered beta testing, and the browser has managed to amass millions of users.

Windows 10 will soon refuse to connect to WEP networks
There are various ways of protecting wireless networks, and as technology develops old methods become outdated. One wireless security technique that has fallen by the wayside is WEP (Wired Equivalent Privacy) because it is very easily defeated.
Having been superseded by WPA2 and WPA3 (Wi-Fi Protected Access generations 2 and 3), Microsoft is completely dropping support for WEP from Windows 10. Soon, it will not be possible to connect to a wireless network with WEP in place.

Cyber incident ripple effects lead to increased losses
Cybersecurity incidents that involve more than one party incur financial losses 13 times greater than those contained within a single organization according to a new report.
The study carried out by the Cyentia Institute for RiskRecon analyzed over 800 cyber incidents and their 'ripple effect' on multiple downstream organizations.

Cybercriminals step up attacks on the healthcare sector
Comparing all of 2018 against just the first three quarters of 2019 has seen a 60 percent increase in threat detections at healthcare organizations, according to a new report from Malwarebytes.
The industry has been overwhelmingly targeted by Trojan malware during the last year, with attacks increased by 82 percent in Q3 2019 over the previous quarter. The two most dangerous Trojans of 2018–2019 for all industries, Emotet and TrickBot, were the two main culprits.

The Facebook app could be secretly using your iPhone camera behind your back
Facebook is hardy a name that synonymous with privacy, and a newly discovered issue with the iOS version of the Facebook app does nothing to improve the situation.
Web designer Joshua Maddux was alarmed to find that the app was secretly using the camera on his iPhone as he scrolled through his Facebook feed. The problem has been confirmed by others, but it appears to only affects certain iPhones and certain versions of iOS.

ESET launches Full Disk Encryption for businesses
Although businesses go to great lengths to protect their networks, physical loss of devices and the consequent risk to corporate data remains a major concern.
Cyber security company ESET is addressing this with the launch of Full Disk Encryption, allowing IT administrators to remotely deploy, activate, and encrypt connected devices using a one-click action, thus preventing attackers from profiting from lost or stolen computers.

Senior professionals not confident in their security solutions
More than a third of senior security professionals aren't confident in their choice of security solution and as a result could be put in compromising positions as the organization uses its security posture as a selling point.
This is among the findings of the latest Cyber Confidence Report from Nominet. When asked how confident they were in an organisation’s final choice of security solutions, only 34 percent of CISOs say that they are only somewhat or slightly confident.

Reluctance to automate leads to problems for enterprise network firewalls
Enterprises are slow to abandon manual processes, despite being short of staff, and a lack of automation, increasing network complexity and limited visibility are contributing to costly misconfigurations and increased risk.
This is among the findings of the 2019 State of the Firewall Report released today by security automation specialist FireMon, the report is based on responsed from almost 600 people.

Apple is fixing a macOS flaw that exposes snippets of 'encrypted' emails
Apple is working to fix an issue that makes it possible to read portions of encrypted email in macOS after an IT specialist discovered a flaw in the way Mail's messages are handled by Siri. The problem affects macOS versions from Sierra to Catalina.
It is important to note that there are a number of criteria that have to be met for the issue to rear its head, but the fact that it is possible at all is still a concern. For a company that has just been shouting about its privacy policies, the timing is less than ideal -- particularly as Apple has been aware of the problem since July.
