
Cybercriminals can penetrate 93 percent of company networks
In 93 percent of cases, an external attacker can breach an organization's network perimeter and gain access to local network resources.
This is among the findings of a new study of pentesting projects from Positive Technologies, conducted among financial organizations, fuel and energy organizations, government bodies, industrial businesses, IT companies and other sectors.

Nearly a quarter of employees are likely to fall for phishing attacks
Almost a quarter (22 percent) of employees globally are likely to expose their organization to the risk of cyber-attack via a successful phishing attempt according to a new study.
The study, from AI-driven cybersecurity training software company Phished, shows that of employees who open a phishing message 53 percent are likely to click a malicious link contained within it.

Organizations lack confidence in managed security solutions
A new report produced by MITRE Engenuity and Cybersecurity Insiders seeks to understand the current state of managed services security.
It finds that while 68 percent of respondents use MSSP/MDR solutions to fill security gaps, a worrying 47 percent are not confident in the technology or the people. Also 44 percent are not confident in the managed services security processes.

Three-quarters of enterprises don't have full observability of log data
Log data is important for tasks such as tracking performance of applications and capacity resources, informing product improvements, and identifying threats and anomalous activity.
But a new report from LogDNA, based on a Harris poll of more than 200 professionals responsible for observability and log data management across the US, shows 74 percent of companies are still struggling to achieve true observability despite substantial investments in tools.

Ransomware doesn't take weekends off
Ransomware is being targeted at organizations seven days a week, leaving no time for enterprises to shore up their security operations, according to a new report.
Analysis of publicly reported ransomware events by RiskRecon looks at the dates on which ransomware activated to encrypt systems, a metric that which was disclosed in 473 of the 654 events examined.
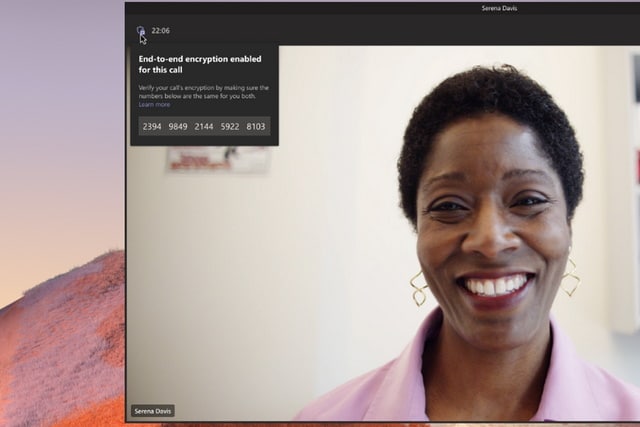
One-to-one Microsoft Teams calls finally have the security of end-to-end encryption
Microsoft is improving the security of one-on-one Teams chats by adding end-to-end encryption. After a couple of months of testing the feature as part of a public preview the company says that the optional security boost is now generally available.
In order for calls to be protected, both parties need to have end-to-end encryption enabled. And if you're wondering why you might want to have E2EE disabled in Microsoft Teams, it's because having the security feature enabled means that some other call features do not work.

What are Log4Shell and log4j and should you be worried about them?
At the end of November a vulnerability targeting Minecraft servers was uncovered. If you don't play Minecraft you probably didn't pay it much attention.
Since then, however, 'Log4Shell' has surged across the web sending tremors through the security community and prompting the US government to describe it as a 'severe risk'. So, what's going on and is it time to panic?

Lack of segmentation exposes enterprise networks to risk
Segmentation is an approach that separates critical areas of the network to control traffic, prevent lateral movement, and ultimately reduce the attack surface.
But according to a new study from Guardicore -- based on a survey of over 1,000 IT decision makers by Vanson Bourne -- while 96 percent of organizations claim to be implementing segmentation in their networks, only two percent are segmenting all six mission-critical asset classes, including critical applications, public-facing applications, domain controllers, endpoints, servers, and business critical assets/data.

Cybereason and Google Cloud launch AI-powered protection
Anything that's connected to the internet can be a possible attack route for hackers, but organizations are often forced to use multiple solutions for protection, adding complexity and risk.
Cybereason and Google Cloud are launching an AI-powered XDR (Extended Detection and Response) solution to enhance and simplify the ability to predict, detect, and respond to cyberattacks.

Security firm releases a free fix for serious Log4Shell vulnerability in Apache Log4j
If you are running a version of Apache Log4j between 2.0-beta9 to 2.14.1 (inclusive) the Log4Shell vulnerability is something you need to be aware off. Tracked as CVE-2021-44228, this is a serious and easily exploited RCE flaw in the open-source Java-based logging utility.
An attacker can exploit the security flaw to execute a remote attack by simply using a particular string as the browser user agent. Although the Apache Software Foundation has released a patched version of Log4j 2.15.0, not everyone is able to update straight away, and this is something that attackers are taking advantage of. Thankfully, security firm Cybereason has released a "vaccine" called Logout4Shell that protects against Log4Shell.

What cybersecurity can learn from health and wellness
The current cyberthreat landscape can feel like a dark cloud hanging over the head of every organization, the same way Covid loomed over us for so long. But just as advances in health have offered light at the end of the tunnel for the pandemic, new approaches to cyber wellness can help us stay healthy and secure in the digital realm.
By taking proactive measures to ward off digital diseases like ransomware, and fighting off any infections that do occur through individually tailored therapies and treatments, we can go about our business with confidence, feeling and performing our best.

New solution aims to streamline enterprise identity management
Over time enterprises amass lots of applications, each of which has its own means of authentication and authorization for users. This inevitably leads to 'identity sprawl' with information being held in multiple different silos.
In order to unify identity data from all sources within an organization and turn it into a flexible resource that can deliver verification on demand, Radiant Logic is launching its RadiantOne Intelligent Identity Data Platform.

The internet is getting safer but legacy encryption techniques still linger
A new report from Venafi, based on in-depth security analysis of the world's top million websites over the last 18 months, shows the internet is becoming more secure.
Use of encryption is increasing and the adoption of newer TLS protocols is rising. However, many companies continue to use legacy RSA encryption algorithms to generate keys, despite stronger protocols being available.

Linux Foundation to host Cloud Hypervisor project
The Linux Foundation has announced that it will host the Cloud Hypervisor project, aiming to deliver a Virtual Machine Monitor for modern cloud workloads.
Written in Rust, the project has a strong focus on security, features include CPU, memory and device hot plugging; support for running Windows and Linux guests; device offload with vhost-user; and a minimal and compact footprint.

Bots-as-a-service and why they might interest shoppers [Q&A]
Bots tend to have a poor reputation, launching cyber attacks, beating you to the best bargains on eCommerce sites and generally being a bit of a pain in the Net.
Nowadays bots are frequently available 'as-a-service' so it's possible to rent one for a period of time to execute an attack. But, according to research for Cequence Security, 32 percent of respondents say they've used a shopping bot before and 38 percent say they might in the future. So that's 70 percent of people who are thinking, 'If you can't beat them, join them.'
