Twitter is going to make you pay for some elements of 2FA -- act now to secure your account for free!

Two-factor authentication (2FA) is an important means of securing accounts, making it significantly harder for hackers to gain unauthorized access. So it is perhaps a little surprising that Twitter has announced that it is locking one of the most popular 2FA methods behind a paywall.
The company has announced that SMS-based two-factor authentication will only be available to paying Twitter Blue subscribers. The change will take effect on March 20, and after this date non-paying Twitter users will be limited to securing their account with either an authentication app or a physical security key.
See also:
- Twitter reveals scant details of its controversial changes to API access, including 'a new form of free access'
- Microsoft is adding a useful End Task option to the Windows 11 taskbar; here's how to enable it now!
- Twitter delays the rollout of paid API access yet again, and confirms researchers will lose free access
The company says that bad actors are frequently found abusing 2FA that is based on phone numbers, and it believes that charging for access to this very common security method is the solution. Questions will be asked, however, about how limiting SMS-based 2FA to Twitter Blue subscribers will help the situation. Identity verification for Twitter Blue is limited at best, so excluding non-subscribers from using this particular method of 2FA merely means that those who are willing and able to pay for it will be able to use it -- and this will almost certainly include the "bad actors" Twitter is using to justify the move.
Open up the Twitter app on your phone, and you're likely to see a message like this:
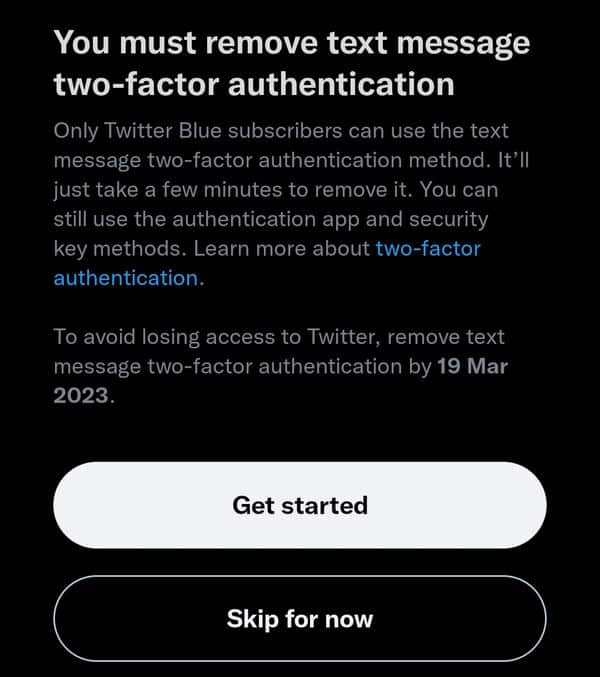
As the message says there is just a month for you to disable text message two-factor authentication, or you risk "losing access to Twitter". Clicking through reveals the following screen:
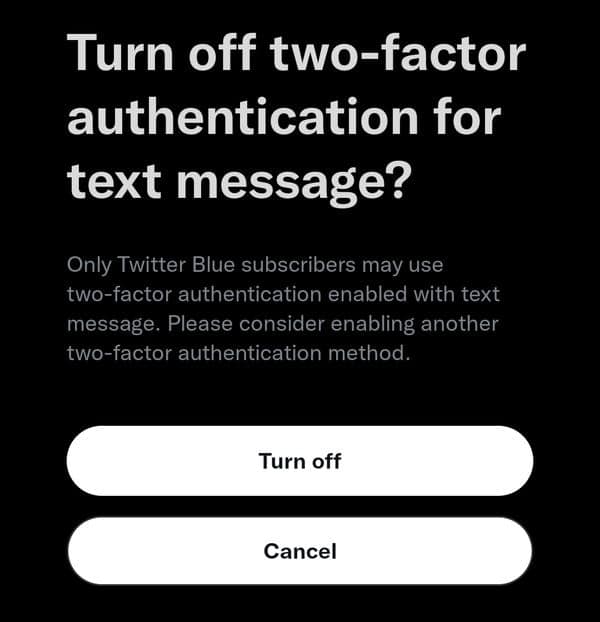
After disabling SMS 2FA, you can then opt to enable one of two other methods -- using an authentication app, or using a security key. What is likely, however, is that many people will simply disable 2FA entirely, resulting in poorer security.
Twitter made the announcement in a blog post that reads:
We continue to be committed to keeping people safe and secure on Twitter, and a primary security tool we offer to keep your account secure is two-factor authentication (2FA). Instead of only entering a password to log in, 2FA requires you to also enter a code or use a security key. This additional step helps make sure that you, and only you, can access your account. To date, we have offered three methods of 2FA: text message, authentication app, and security key.
While historically a popular form of 2FA, unfortunately we have seen phone-number based 2FA be used - and abused - by bad actors. So starting today, we will no longer allow accounts to enroll in the text message/SMS method of 2FA unless they are Twitter Blue subscribers. The availability of text message 2FA for Twitter Blue may vary by country and carrier.
Non-Twitter Blue subscribers that are already enrolled will have 30 days to disable this method and enroll in another. After 20 March 2023, we will no longer permit non-Twitter Blue subscribers to use text messages as a 2FA method. At that time, accounts with text message 2FA still enabled will have it disabled. Disabling text message 2FA does not automatically disassociate your phone number from your Twitter account. If you would like to do so, instructions to update your account phone number are available on our Help Center.
We encourage non-Twitter Blue subscribers to consider using an authentication app or security key method instead. These methods require you to have physical possession of the authentication method and are a great way to ensure your account is secure.
It is worth remembering that, as the blog post mentions, Twitter Blue is not available globally. This means that some people will be forced to use a different method of 2FA that they may not be comfortable with.
Image credit: Mehaniq / depositphotos
