
Cloaking-as-a-service set to reshape the phishing landscape
Imagine if hackers could give their scam websites a cloak of invisibility, showing one web page to regular people and a harmless page to security scans. Sneaky, huh?
According to new research from SlashNext that’s essentially what’s happening as cybercriminals start to leverage AI-powered cloaking services to shield phishing pages, fake stores, and malware sites from prying eyes.

CrapFixer update fixes Windows 11 and turns it into the operating system you deserve -- download it now!
There are a number of great tools that you can use to improve Windows 10 and 11, but our new favorite is CrapFixer. The free program can remove bloat, ads, AI, unwelcome data collection, and more from the operating system.
Although it was originally created seven years ago it has been completely rewritten for Windows 11 and a new update makes it even better, with its own small, modern Policy Editor.

The future of encryption in a post-quantum world
As quantum computing speeds edge closer to practical use, the ‘harvest now, decrypt later’ approach is already in motion with adversaries collecting encrypted data today, anticipating they'll be able to crack it tomorrow. But is enough being done to prevent it?
New research from Forescout highlights the urgent need for organizations to prepare for a future where quantum-capable adversaries can break widely used cryptographic protocols.

Application layer comes under threat
A new report from Contrast Security exposes a growing crisis at the application layer as adversaries use AI to easily launch previously sophisticated attacks at scale.
Recent reports from Verizon (DBIR 2025) and Google Mandiant (M-Trends 2025) confirm what many security leaders already suspect: components of the application layer are among the most targeted and least protected part of the modern enterprise.

Outdated printer firmware can leave organizations open to attack
In the past the printer has tended to be a pretty dumb device, but as they’ve gained more features and extra connectivity printers have become a target for attacks and potentially a way of gaining access to networks.
A new report from HP Wolf Security, based on global study of 800+ IT and security decision-makers (ITSDMs), highlighs the challenges of securing printer hardware and firmware.

Financial firms keen to use AI but their data isn't ready
A new study into AI readiness shows that while financial services firms are ready to adopt AI, they still have work to do in terms of improving data quality and modernizing systems.
The study from Indicum finds many financial services firms are hindered by legacy data systems and outdated IT infrastructure, which often lack the real-time processing and data quality capabilities required for effective AI deployment.

Matanbuchus 3.0 is a serious malware threat spread via Microsoft Teams
The Matanbuchus malware loader is not new – it has been around for at least 4 years – but it has evolved into something incredibly dangerous.
Matanbuchus 3.0 has been found targeting victims as part of a ransomware attack. Described as being “highly targeted”, the cyberattack campaign uses Microsoft Teams as a delivery method for the latest version of the malware loader. The highly sophisticated attack employs a Microsoft Teams call impersonating an IT helpdesk.
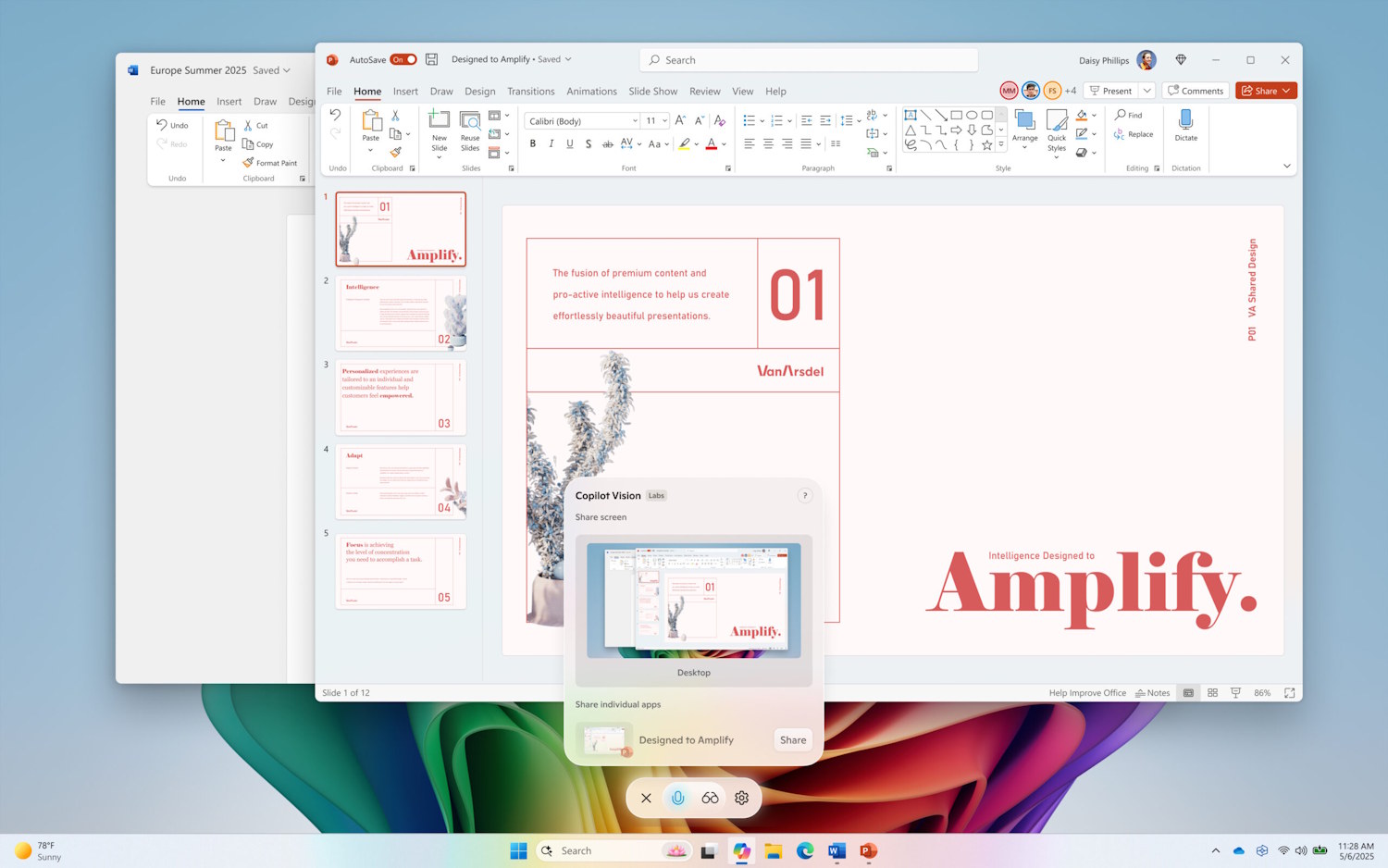
Microsoft rolls out whole desktop sharing to Copilot on Windows 11
Microsoft’s development of Copilot continues apace, and the latest update is one that could prove to be divisive. Windows 11 users signed up to the Windows Insider program are being given a new option in Copilot Vision for Windows – namely the ability to share the entire desktop with the AI tool.
Sharing your desktop in this way means that Copilot Vision for Windows will be able to see everything that is on your screen asnduse it in your interactions. While there are many potential uses for this, the controversy caused by screenshotting desktops with the Recall feature of Windows that was so controversial that Microsoft had to withdraw and rebuild it.
WhatsApp is developing a way to use status updates to run surveys
WhatsApp is not only one of the most popular communication apps out there, but also one of the most dynamic and frequently updated. The beta releases for WhatsApp are exciting places to hang out and a great way to try, or at least glimpse, new features.
The latest update does not buck the trend. In the most recent beta release for Android, we see developers working a new way to make use of status updates. These are already highly versatile but soon will provide a way to pose questions.

IObit Software Updater 8 makes app updates faster and safer -- download it now
IObit has launched Software Updater 8 to manage software updates and installations in a single place. The latest version of the popular tool aims to reduce security risks and save time by offering faster updates, a larger database of programs, and -- because it’s 2025 -- access to a wide range of AI-powered tools.
Keeping software updated can be a hassle, and skipping updates can leave systems exposed to security threats. IObit Software Updater 8 addresses this by scanning for outdated applications and applying the latest official versions with just one click.

Ditch Windows 11: SparkyLinux 7.8 is the lightweight alternative to Microsoft's OS you've been looking for
SparkyLinux 7.8 is now available to download, bringing a welcome selection of updates to the “Orion Belt” stable release series. Based on Debian 12 “Bookworm,” this latest point release offers a modern Linux experience that’s a strong alternative for users looking to move away from Windows 11.
With Microsoft's OS continuing to introduce clunky AI features, bloat, slow performance and limited user control, SparkyLinux serves as a lighter, faster, and fully customizable alternative. Version 7.8 delivers updated software, improved desktop environments, and superior system performance.

Ransomware surges 63 percent in Q2
The second quarter of this year has seen a 63 percent increase in publicly disclosed ransomware attack volumes, with a total of 276 incidents compared to Q2 2024, according to the latest report from BlackFog.
This represents the highest number of attacks for this timeframe since the company began tracking ransomware volumes in 2020. All three months in the quarter set a new high compared with the same time period in previous years. June saw 113 percent increase with a total of 96 attacks. There was a 51 percent increase in April with a total of 89 attacks, and a 40 percent increase in May with 91 attacks.

Differing levels of access to AI create new inequalities
A new survey of 4,000 knowledge workers across the UK, US, Germany, and Canada reveals that higher earners have disproportionate access to the latest AI tools and training, allowing them to reap AI's promised rewards.
In contrast, the study from The Adaptavist Group reveals that lower earners and women are being shut out from AI opportunities, which impacts their skill development, job satisfaction, and time savings, both personally and professionally.

OnePlus releases innovative 2-in-1 charger cable for watches and phones
Owning a smartphone is just about a given these days, and it is also becoming true for a smartwatch. If you have bought into the OnePlus ecosystem for your phone and watch, the company has just released an incredible 2-in-1 charger cable.
While not an entirely unique idea – there are various chargers out there that can charge two devices at the same time – the solution from OnePlus has at least a couple of features that make it stand out from the crowd.
What has AI done for us? Celebrating AI Appreciation Day
In the last few years artificial intelligence has found its way into more and more areas of our world and its progress shows no signs of slowing down.
Of course most things these days need a day to mark their achievements and today is AI Appreciation Day. So, what has AI done for us and what can we expect from it in future? Some industry experts gave us their views.
