
Cloudflare's Impact Report for 2025 reveals how elections, journalism, and nonprofits faced rising online threats
Cloudflare has published its fifth annual Impact Report, outlining how its network and security services have been used to support elections, independent media, and nonprofit organizations while also addressing environmental commitments. The report explains why these efforts matter as cyberattacks, automation, and AI-driven traffic continue to reshape how public interest services operate online.
The Impact Report follows Cloudflare’s recent 2025 Radar Year in Review, the sixth annual report examining broad trends in internet traffic, security, and technology adoption across its global network. That earlier analysis used aggregated data from web requests, bots, and connectivity signals to show how automation, encryption changes, and attacks shaped online services worldwide. The new report narrows the focus to how those trends affected democratic institutions, journalism, and other vulnerable groups.

Adapting to AI agents, growing risks and perimeter focus -- identity predictions for 2026
Identity remains key to cybersecurity with stolen IDs opening the door to many attacks. And with the rise of AI agents and machine identities it isn’t just just humans that we have to worry about. Here’s what some leading industry figures think we can expect from the identity landscape in 2026.
Itamar Apelblat, CEO and co-founder of Token Security, thinks compliance frameworks will need to be rebuilt to account for AI agents. “Traditional compliance models were designed for human-centric workflows, and they are already breaking. Over the next year, frameworks will evolve to recognize AI agents as workforce identities with their own permissions, accountability requirements, and control expectations. Organizations that fail to adapt will fall out of step with regulators and customers.”

Adobe partners with Runway to bring AI video generation into Firefly
Adobe has announced a multi-year partnership with Runway that pulls generative video directly into Adobe Firefly and, over time, deeper into Creative Cloud. The idea is to make AI-generated video part of the same tools people already use to edit, finish, and deliver professional projects.
Runway offers AI video generation tools that let users create clips from text prompts, control motion and pacing, and experiment with different visual ideas without shooting footage. It sits in the same general space as tools like OpenAI’s Sora, but is often used as a practical production tool.

DisplayFusion 12 arrives with fixes and improvements for managing multi-monitor setups
DisplayFusion 12 is now available, offering a number of improvements to the tool which helps manage multi-monitor setups on Windows. The updated version focuses on fixing long-standing issues, improving how Windows handles multiple displays, and adds some small small but useful changes that should make managing several screens less fiddly.
Multi-monitor support in Windows is decent, but it stops short of giving users real control. Although adding one or more displays is easy enough, the OS largely treats them as one extended desktop. DisplayFusion takes things further, tightening how windows, wallpapers, taskbars, and profiles behave across multiple screens.

AI data transparency shapes shopping behavior
A new survey of over 1,000 US consumers looks at how holiday shopping behavior is impacted by brand management of personal data in AI systems.
The study from Relyance AI suggests Americans are entering the gifting season emotionally depleted and digitally exposed, with most planning to shop online. But feeding more personal data into systems during periods of high stress and emotional depletion sets the stage for a fragile purchasing environment.

Chuwi announces two new lightweight Ryzen laptops under $600
Chuwi has announced two new lightweight Windows 11 laptops called the CoreBook Air and CoreBook Air Plus. Both systems are powered by AMD’s Ryzen 5 6600H processor.
The CoreBook Air weighs 1kg and has a 14 inch 16:10 WUXGA IPS display. The CoreBook Air Plus steps up to a 16 inch screen of the same resolution and weighs slightly more at 1.35kg. The two laptops use aluminum alloy chassis and slim bezels, and are available in an indigo color.

MiniTool adds a duplicate cleaner and refreshed interface to Partition Wizard 13.5
MiniTool has released version 13.5 of its Windows partition manager, adding a new Duplicate Cleaner and updating the interface. The update focuses on making storage tasks quicker to complete and easier to understand.
The new Duplicate Cleaner clears out repeated files across local drives and external devices. It scans selected locations, identifies matches, and lets users remove unneeded copies while keeping control over how those files are handled.

Why SaaS apps are a prime target for attackers [Q&A]
Attackers will always use tactics that are proven to work and with more business turning to SaaS for their systems obviously these apps are on the cybercriminal’s radar.
We spoke to Martin Vigo, lead offensive security researcher at SaaS security company AppOmni, to explore the reasons why SaaS apps are such fertile ground for attackers.
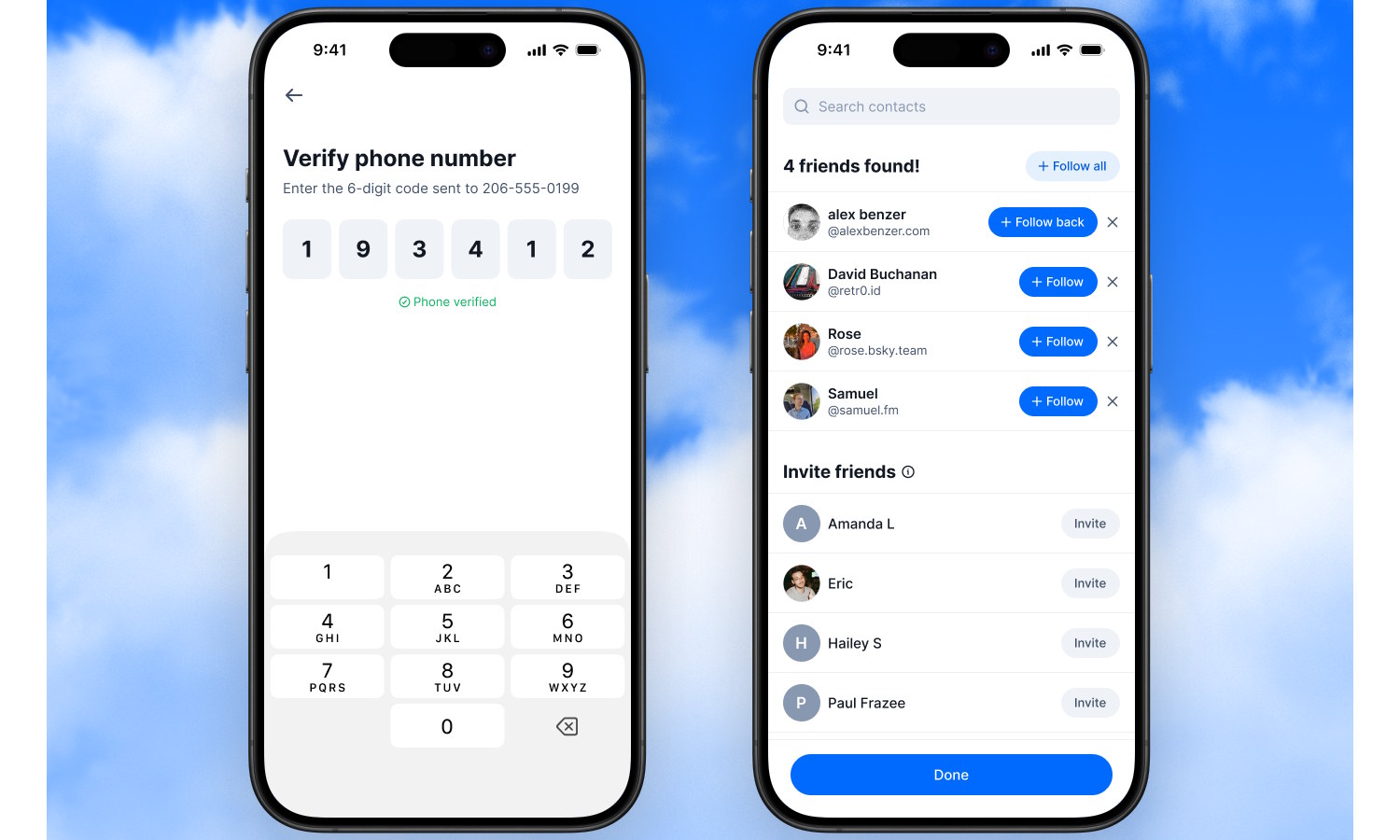
Bluesky launches Find Friends feature to find people you know on the platform
All social media platforms are about connections, and Bluesky is no different. The problem that a social platform with a focus on privacy and security has is that it can be hard to track down people you know that you would like to connect to.
It is with this in mind that Bluesky is launching a new contact import feature called – somewhat uninspiringly – Find Friends. One of the aims, apart from connecting people, is to help cut down on spammy methods of tracking people down.

Investor deal is a ‘new TikTok US joint venture’
The seemingly never-ending story of TikTok and its place in the US could be coming to an end. A new deal between TikTok’s parent company ByteDance and US investors allows the social platform to continue operating in the country.
Reports from CNBC say that TikTok has signed an agreement to create a new US joint venture. The arrangement involves a number of big investors, and the resulting entity is known as TikTok USDS Joint Venture LLC.

Instagram puts a limit on hashtag usage
In a bid to help clamp down on spam on the platform, Instagram has announced new limitations on the use of hashtags. While there is certainly some value in hashtags for the tracking and categorization possibilities they offer, they are also open to abuse.
If you have been confused, frustrated, angered or otherwise responded negatively to an Instagram post which has dozens and dozens of hashtags, the new policy will come as good news. Details were shared about the changes not in a news release or even an Instagram post, but in a post to Threads.

Microsoft releases emergency patch for Windows 10 to fix Message Queuing problems
The situation for updates for Windows 10 remains quite confusing for many people. Now mainstream support has ended, those who are sticking with the older operating system need are reliant on the Extended Security Updates program to keep their computers safe.
But, breaking with the way things were meant to work out, Microsoft has now released an out-of-band update for Windows 10 to address an issue introduced by an earlier security patch. The KB5074976 update is a little unusual in that it needs to be manually installed. Here is what you need to know.
Visa says AI agents will complete shopping purchases for you in 2026
Visa says it has completed hundreds of real-world transactions initiated by AI agents, marking an early test of a (near) future where software can move from shopping recommendations to payment without a human needing to click through the checkout process.
The transactions were carried out with partners across Visa’s payments ecosystem and took place on live systems, rather than in demonstrations or simulations. According to the company, they show that AI-driven purchases can be completed securely using existing payment infrastructure, so long, that is, as the agent operates within predefined controls.

Fineshare's new Vora AI can clean up Sora videos and upscale them to 4K
Fineshare has announced the launch of Vora AI, a video generation and enhancement tool designed to improve videos created with OpenAI’s Sora, including content produced using Disney characters as part of the new deal Sam Altman's firm struck with the House of Mouse.
Fineshare says the tool focuses on improving visual quality, speeding up production, and helping creators keep pace with fast-moving platform trends.

Hospitals struggle with visibility of connected medical devices
A new survey of CISOs at North American hospitals finds that 43 percent identified complete device visibility as the challenge they would most want to solve immediately, followed by ransomware threat detection (24 percent) and compliance automation (22 percent).
The study from Asimily also uncovered fragmentation in how hospital security teams approach vulnerability remediation. Only 22 percent of hospital CISOs base their prioritization on device usage and criticality, which is the most effective method for focusing resources on the highest-risk assets. Meanwhile, 18 percent rely on manual review and 15 percent report having no clear process at all for addressing IoMT (Internet of Medical Things) vulnerabilities.
