How the data talent gap risks our AI future
Data workers are at the center of our ambitious targets for universal artificial intelligence adoption as they are the ones responsible for building the technology on a strong and stable foundation. However, there is one significant hurdle that stands between data workers and designing the perfect AI solution; the talent gap. Recent research has revealed that 44 percent of data workers are wasting time every week because they are unsuccessful in their activities, as they face challenges such as lengthy data preparation processes and a lack of collaboration. If organizations can't attack the data and analytical talent gap head-on, they will increasingly be buried under rising data volumes, complexity and an incomplete understanding as to whether their workflows are doing the job they want.
Without a productive workforce, organizations simply cannot proceed to tackle the technical challenges existing in a data-driven industry, such as reversing the inconsistencies and set-backs with data-led AI projects. With the right analytics platform, data capabilities can be put in the hands of the business experts who not only have the context of the problems to solve but the data sources needed to deliver insights quickly and efficiently. By alleviating data workers of some of the mundane, day-to-day tasks that are consistently clogging up their to-do lists, more time can be allocated to pushing through large-scale AI projects.

A primer on migrating SQL Server 2008/2008 R2 databases to the Azure cloud
System and database administrators are now being forced to do something about legacy SQL Server 2008 and 2008 R2 database applications. The reason is the end of Extended Support in July 2019. Extended Support will also end for its common companion Windows Server 2008 and 2008 R2 in January 2020. Upgrading to the latest versions is always an option, of course, but Microsoft is providing an attractive alternative when upgrades are not viable or cannot be cost-justified: Migrate the database to the Azure cloud and get three more years of Extended Security Update support at no additional charge over the standard virtual machine pricing.
This article highlights important considerations for migrating mission-critical legacy SQL Server 2008/R2 databases to the Azure cloud to help administrators make more informed decisions. Among the key considerations is knowing which options are and are not available.

Get 'Hands-On Network Forensics' ($20 value) FREE for a limited time
Network forensics is a subset of digital forensics that deals with network attacks and their investigation. In this era of network attacks and malware threats, it’s now more important than ever to have skills to investigate network attacks and vulnerabilities.
Hands-On Network Forensics is not only your ticket to gaining basic skills in network forensics, but also learning how to apply them effectively.

Integration with MITRE ATT&CK framework delivers improved security skills training
Traditional cyber security training is often based on out-of-date attack methodologies which means the skills learned quickly becoming outdated. While cybercriminals are continuously innovating, training for security professionals is lagging behind.
Skills development platform Immersive Labs has announced an integration that allows organizations to base cyber skills training on MITRE ATT&CK, meaning organizations can map and manage specific people’s skills, to actual risks.

Logitech launches wireless MX Master 3 mouse and MX Keys keyboard
Logitech makes great hardware, but understandably, its products aren't "one size fits all." For instance, a gamer might have different needs than a business person. Its MX Master wireless mice are really popular with some, but I personally don't really like them. Why? Well, my hands are fairly small, and I prefer a more simplistic approach -- I want the mouse to essentially disappear and become an extension of my arm. Sadly, the MX Master mice are too large and busy to do that -- for me, at least.
For the many consumers that love the MX Master mice, however, I have great news -- the third generation launches today. MX Master 3 features USB-C charging and improved scrolling. It can be had in either a graphite or grey color. What I am more excited about, however, is a new wireless keyboard that the company releases today. Called "MX Keys," it is very similar to the existing Logitech Craft keyboard, but without the input dial. That's fine with me. Look, that dial is cool, but it never really caught on with consumers.

Companies struggle to deliver digital transformation projects
Despite the popularity of digital transformation projects, the vast majority of organizations are still suffering failure, delays or scaled back expectations from their projects according to new research from enterprise database company Couchbase.
The study of 450 heads of digital transformation in the US, UK, France and Germany finds 86 percent say factors including reliance on a legacy technology, complexity of implementing technologies, and lack of resources and skills had prevented them from pursuing a new digital service or other project.
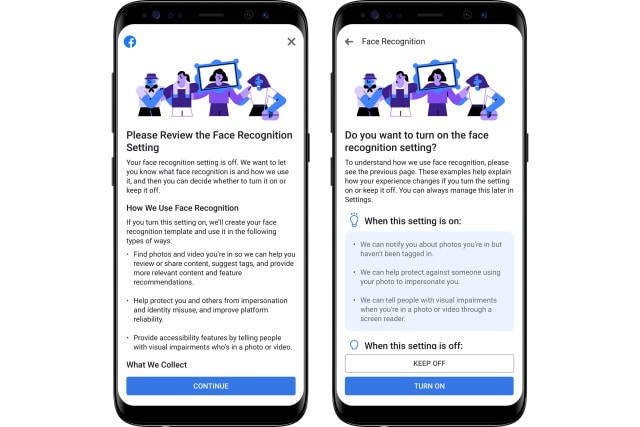
Facebook now lets you opt out of automatic facial recognition
Facebook has announced changes to its facial recognition feature as it rolls out globally. The feature is used to automatically identify and tag people in photographs uploaded to the social network.
Acknowledging concerns about privacy, the company is making it easier to opt out of the "Tag Suggestions" feature which was introduced to a subset of users back in 2017. Now known as Face Recognition, new users will be given the chance to opt out from the word go, while anyone who has (or had) Tag Suggestions enabled will be informed of the change and asked whether it should be on or off.

SteelSeries launches Arctis 1 wireless gaming headset for Nintendo Switch, PC, PlayStation 4, Xbox One, and Android
There is this idea that people have to choose between PC and console gaming. While I'm sure there are some folks that are adamant about only using one or the other, the reality is, gamers just want to play games -- the platform doesn't really matter. Hell, some consumers own all of the current consoles, such as PlayStation 4 and Switch, while also playing PC games.
If you are the type of gamer that uses several platforms, SteelSeries has a new wireless gaming headset for you. Called "Arctis 1 ," it will work with Nintendo Switch, PC, PS4, Xbox One, and Android. It comes with a USB Type-C wireless transmitter that plugs into the PC or console. If your device doesn't have USB-C, do not worry -- it also comes with a Type-A cable and 3.5mm audio cord.

The hidden costs of third-party data breaches -- and how to avoid them
Recent studies show that third-party data breaches are the most expensive cyber incidents for businesses today. The rise in associated costs has prompted not only security leadership but also executives and boards to pay close attention to the cyber risk that comes with doing business with their biggest vendors and partners. But what many business leaders don’t realize is that the biggest third-party cyber risks can come from the smallest, most seemingly innocuous places.
Take, for example, the Docker Hub cyberattack that took place this past May. While in the grand scheme a given business ecosystem, Docker Hub’s role -- a container used by developers to store image files -- is small, the extent of the damage to its customers was not.

Security professionals now think cloud is safer than on-premise
New research from internet infrastructure company Nominet finds that 61 percent of security professionals believe the risk of a security breach is the same or lower in cloud environments compared to on-premise.
The study of nearly 300 UK and US C-level security professionals, marks a major shift in the perception of security of the cloud. However, it doesn't mean the cloud is viewed as entirely safe.

Phishing attacks target UK SMBs
According to a new study 43 percent of UK SMBs have suffered phishing attacks involving attempts to impersonate staff in the last year.
More concerning is that of those attacks 66 percent were successful in compromising data. The study from security and data anlaytics company CybSafe also finds only 47 percent of those surveyed say they have already got a cyber security training and awareness program in place.

Geekbench 5 arrives, offers new CPU and GPU benchmarks
Primate Labs has announced the release of Geekbench 5.0 for desktop, Android (later this week) and iOS. Geekbench 5 makes huge changes to the way it benchmarks your CPU and GPU, as well as going 64-bit and Windows 10 only.
Other changes include a brand new Dark Mode (confusingly, currently macOS only with iOS 13 to follow, but not for Windows 10) and a 50 percent launch sale if you were considering upgrading.

Firefox Quantum 69 strengthens default anti-tracking protection, can block all autoplay content
Mozilla has released Firefox Quantum 69.0 for desktop, along with Firefox for Android 68.1 and Firefox ESR 68.1.0.
The new release switches on Enhanced Tracking Protection features by default, extends block autoplay to cover all videos (not just those with sound) and improves performance on Windows 10 machines. The Android release marks the browser’s move to the ESR channel.

Take two: Samsung Galaxy Fold pre-registrations go live in the US and UK
After poor reviews, a postponed launch, and something of a redesign, Samsung is readying itself to launch the Galaxy Fold.
If you haven't lost interest -- or faith -- as a result of the problems and delays, Samsung has opened up "pre-registration" once again in the US and UK. While it is not possible to pre-order yet, the move suggests that a launch is imminent, and Samsung promises you can "be the first to see the future".

Firefox will improve battery life for MacBook users
macOS users who have been disappointed with the power consumption of Firefox have something to look forward to. Developers say that power usage has been dramatically reduced in the latest nightly build, meaning that when the release goes public, MacBook owners can expect to see a jump in battery life.
There have long been complaints about Firefox Quantum sapping batteries, and now it finally seems as though the problem has been addressed.
