
Bluelight Filter Android app helps you reduce eye strain and sleep better
Bluelight Filter is a free Android app which aims to reduce the harmful effects of the blue light emitted by smartphones and tablets.
This could reduce eye strain, help you sleep better, and generally make the screen easier to read.

Recover lost files with NirSoft’s ShadowCopyView and PreviousFilesRecovery
NirSoft has released ShadowCopyView and PreviousFilesRecovery, free tools designed to help you browse Windows’ volume shadow copies and restore whatever files you need.
ShadowCopyView lists all volume shadow copies on your PC, the hard drive snapshots created by Windows Vista and later.

How to automatically mount a network drive on Mac OS X
To quickly and easily access a network drive from your Mac you can configure OS X to automatically mount the volume after booting up. That way, after you turn on or restart your Mac, you will be able to get to your files in no time. But, how can you do that?
While it is very easy to access the network drive, figuring out how to set up OS X to automatically mount it is not. That is because there is no magic button to click on in the volume's settings or an obvious option to enable in System Preferences. So, where does that leave you?

How to remove location data from your photos
Saving the location in photos you take with your smartphone, tablet or camera is a good idea if you want to keep track of where you've captured those moments. Some services, like Google Photos, will do that for you automatically, showing a history of places you've been based on their coordinates. However, when it comes time to share your photos online, you may want to remove the location data.
The location data, alongside other types of identifiable information, will also be shared alongside them, potentially exposing you and your loved ones to all sorts of complications as a result. Fortunately, you can remove the location data from your photos. Here is how you can do that.

How to control when Windows 10 can automatically install updates
Windows 10 updates may add new features, beef up security, and refine the user experience, but they can also be a source of frustration if the operating system decides to automatically install them at the wrong moment. There are times when you really want to keep using your PC, and not let Windows 10 restart it to finish the job. Just ask this pro gamer who had a Twitch stream ruined right in the middle of a gaming session watched by 130,000 followers.
So what can you do? You may be tempted to disable automatic updates or Windows Update altogether, but that is obviously not ideal. However, you can control when Windows 10 can automatically install updates. Here is how you can configure it.

Three steps to BYOD bliss
BYOD has now become so prevalent that 29 percent of UK secondary schools are now operating some sort of BYOD policy including asking students to bring their own devices. While the enterprise world has been talking about BYOD for years, it’s this kind of mainstream use that confirms BYOD as a way of life, and of business.
While there are clear benefits in terms of productivity for example, unfortunately, security still remains a key concern. In order to take advantage of the potential benefits and avoid the security risks, organizations need to do three core things: develop a robust BYOD policy, choose the right security technology, and support the people using it.

How IT admins can support cloud adoption
Iron Man. Captain America. IT administrator. Yes, you read that correctly. As organizations make their shift to cloud computing technologies, including Microsoft Azure and Office 365, IT admins can be crucial -- but often overlooked -- assets.
These superheroes of the technology world can save their organization from technological chaos, stop compliance issues in their tracks, and spread their technical knowledge for the good of the organization. So how can admins prove their worth in the rise of the cloud?
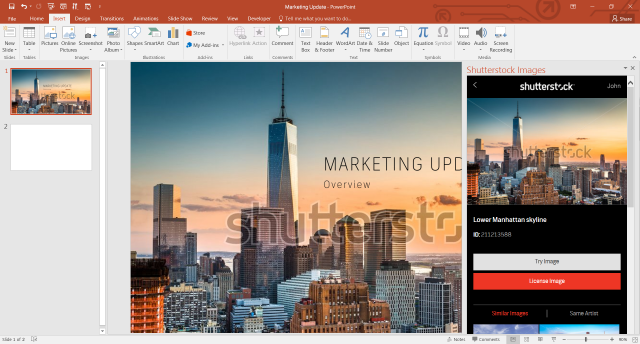
How to add Shutterstock photos to your Microsoft PowerPoint presentations
Shutterstock is now making it easy to find and add quality photos to your Microsoft PowerPoint presentations, as it just launched a new add-in for the popular software that lets you explore and buy images from its vast collection.
"We know our customers are frequently using images to enhance their PowerPoint presentations", says Microsoft corporate vice president of Developer Experiences Steven Guggenheimer. "With this Microsoft Office 365 PowerPoint add-in, Shutterstock is broadening our ability to enhance productivity through its collection of high-quality imagery to professional users".

9 tips to improve your smartphone's battery life
You’re really concerned about your battery life, aren’t you? That’s right, when it’s time to travel or go out, you always remember two things -- your toothbrush and your charger! The toothbrush to make your morning fresh and the charger to save you from the irritation of the diminishing smartphone battery during your working day.
Battery life has been one of the most important concerns for users, app developers, and manufacturers. On average, most smartphone batteries last 1-2 days before being completely depleted. In smartphone reviews we see how battery life can outrank other features -- after all, if the battery’s dead we can’t use them for those important calls or emails! While we wait for any latest technology to come to market, let’s look at some easy ways to conserve battery life. These tips will definitely help to make you feel relaxed and anxiety-free till you return safely to your charger.

Five ways to take your passwords to the next level
World Password Day is apparently a day for “taking our passwords to the next level”, so here are five traditions the crooks and password crackers really, really don’t want us to start.
In 2007, Dinei Florencio and Cormac Herley at Microsoft Research looked into the password habits of half a million users in their large-scale study of website password habits. They found that the average user needed about 25 distinct passwords but only had about six.

Malware takes advantage of Windows' God Mode hack to slip past security
The so-called God Mode hack for Windows is rather less grand than it might first sound. Rather than granting users deity-like abilities, it simply provides one-folder access to an absolute butt-load of Control Panel options and settings. But security researchers have discovered that the technique used to create this special folder can also be exploited by malware.
McAfee says that while the Easter Egg is great for power users, it is also being used by attackers for "evil ends". By placing files within the God Mode shortcut folder, malware such as Dynamer is able to run undetected on a victim's computer.

How to boost your free Microsoft OneDrive storage back up to 15GB
Last year, Microsoft announced plans to drop the free OneDrive storage amount from 15GB down to 5GB, and also discontinue the 15GB camera roll bonus.
Earlier this week we learned that the software giant will be putting this plan into action from July, which means if you’re currently using more than 5GB of storage you will either have to remove some files to get under the new limit, or upgrade to a paid plan. But hold on a minute. Before you do either, there is a third option which you can use to keep your free storage at 15GB.

How to stay safe using public Wi-Fi hotspots
One of the most convenient things about connecting to the Internet through your computer, tablet, or smartphone is being able to tap into public Wi-Fi from pretty much anywhere. These days, there are hotspots available all across the country, so you’re practically never without Internet access. However, it’s a smart move to be cautious when it comes to connecting to public Wi-Fi.
When you’re tapping in to an unfamiliar hotspot, you could potentially be putting your personal data -- and the security of things like your bank accounts, your passwords, and your identity -- at risk. Even if a public WiFi hotspot looks secure, you might still miss the small red flags that signal trouble. Let’s take a look at how public WiFi works to connect you to the Internet, some risks that come with it, and how to ensure you’re keeping your data safe while you’re on a hotspot.

The 3-2-1 rule and other backup tips
It may not have escaped your notice that today is World Backup Day, which aims to raise awareness of the importance of looking after your data.
To mark the event Dark Bear Web Solutions has produced an infographic offering facts and tips about backups.

Best practices for securing your website
The web seems like a dangerous place lately, doesn’t it? We’re constantly hearing about some new piece of malware, or a website that was hacked and defaced, or a new vulnerability in what was once thought to be a secure protocol. I wouldn’t blame you for being paranoid -- after all, to hear the media tell it, your site’s under attack by criminals and ne’erdowells from all sides.
Here’s the thing -- if you’ve taken all the necessary steps to keep your site safe, you actually don’t have a whole lot to worry about. And that’s where we come in. Today, we’re going to talk about some best practices for securing your site, and protecting it against everything from infected clients to ignorant users. Let’s get started.
