
How to backup your computer to the cloud with OneDrive folder protection
Previously only available to OneDrive for Business users, Microsoft is now rolling out OneDrive folder protection to everyone.
Also referred to as "known folder move" -- and rather copying the Backup and sync app from Google -- OneDrive folder protection makes it possible to back up your important files and folders to the cloud. Here's how to get started.

Money, power and ego, the factors that drive people to cybercrime
We reported last week on a report highlighting how many security professionals are turning to a life of cybercrime.
In a follow up research piece, Wendy Zamora at Malwarebytes, has been looking at the psychology, motivations and other underlying factors that drive people to take part in cybercrime.

If you want to record calls in Android 9 Pie, you'll need to root your phone
Recording phone calls is dodgy territory legally speaking, but whether you choose to do it depends on where you are in the world, and whether you're concerned about complying with the law. Since Marshmallow, Google has made it difficult to record calls on Android phones by killing the recording API, but this has not stopped third party developers finding ways around it.
But with Android 9 Pie, Google has made it impossible for apps such as Call Recorder - ACR and BoldBeast Android Call Recorder to be used to record calls. Unless, that is, you're willing -- or able -- to root your handset.

Quickly remove unwanted bundleware using the latest IObit Uninstaller 8
We handle support for people who purchase software and the number one issue we consistently experience is the inability to install updated versions of their favorite software.
There are very basic reasons, too. When you first install your software, you’re often asked to reboot. After this procedure, it’s in use. The application may start when you boot your PC, run in the background, checking your system and much more. When you decide to upgrade, people expect to simply install the latest version on top, forgetting the application is being used and that Windows cannot remove active files.

Trojans increase as cryptomining declines
The second quarter of 2018 has seen a significant increase in Trojan activity, seeing them become the leading type of malware, according to the latest report from Comodo Cybersecurity.
At the same time there has been a slight decrease in cryptomining software. However, this has gone hand-in-hand with a sharp increase in their harmful capabilities, including better concealment and stronger persistence.
Organizations still struggle with basic firewall management
Firewalls remain an important element of security architecture, but many organizations are still struggling with the basics, according to a new study.
Security policy management company FireMon has released its 2018 State of the Firewall report which reveals that 94 percent of respondents believe firewalls are as or more critical than ever.

SnapLogic integrates with GitHub to speed up DevOps capabilities
Self-service application specialist SnapLogic is announcing new integration with GitHub to automate critical elements of continuous integration and continuous delivery (CI/CD).
The integration enables system administrators to host different versions of their work, including tasks, pipelines, and projects from SnapLogic, with visibility into changes with each update.
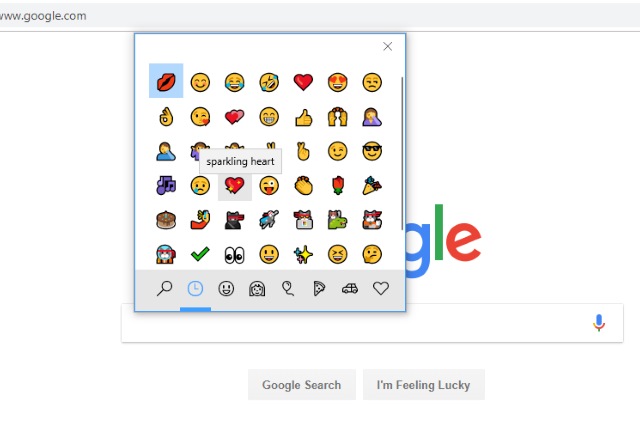
How to enable Chrome's secret Emoji Context Menu to make it easier to type emoji
The likes of Duolingo have made it easier than ever to learn French, Spanish, Polish, Hebrew or whatever other tongue tickles your fancy, but the language of the internet is -- arguably -- emoji. On your mobile phone, these handy little characters are easy to type, but less so on your computer.
To make things a little easier, Google Chrome now has a hidden Emoji Context Menu that you can enable. Once activated, this menu can be used to access an emoji picker to add emoji to text fields. Here's how to enable it.

Twitter is killing push notifications for third party apps -- here's what you need to do
Starting tomorrow -- Thursday, August 16 -- Twitter is disabling push notifications for third party clients. If you use the likes of Twitterific, Fenix or Plume, this could mean you miss out on important messages as Twitter clamps down on what third party tools are able to do.
Twitter has long had a tempestuous relationship with app developers, including its frankly bizarre token limit which effectively restricts the number of users any app can ever attract. This latest move is billed as a part of a security drive, but it's one that will impact a large number of people. There is something you can do to ensure you get Twitter notifications on your iPhone or Android handset, but it's not ideal.
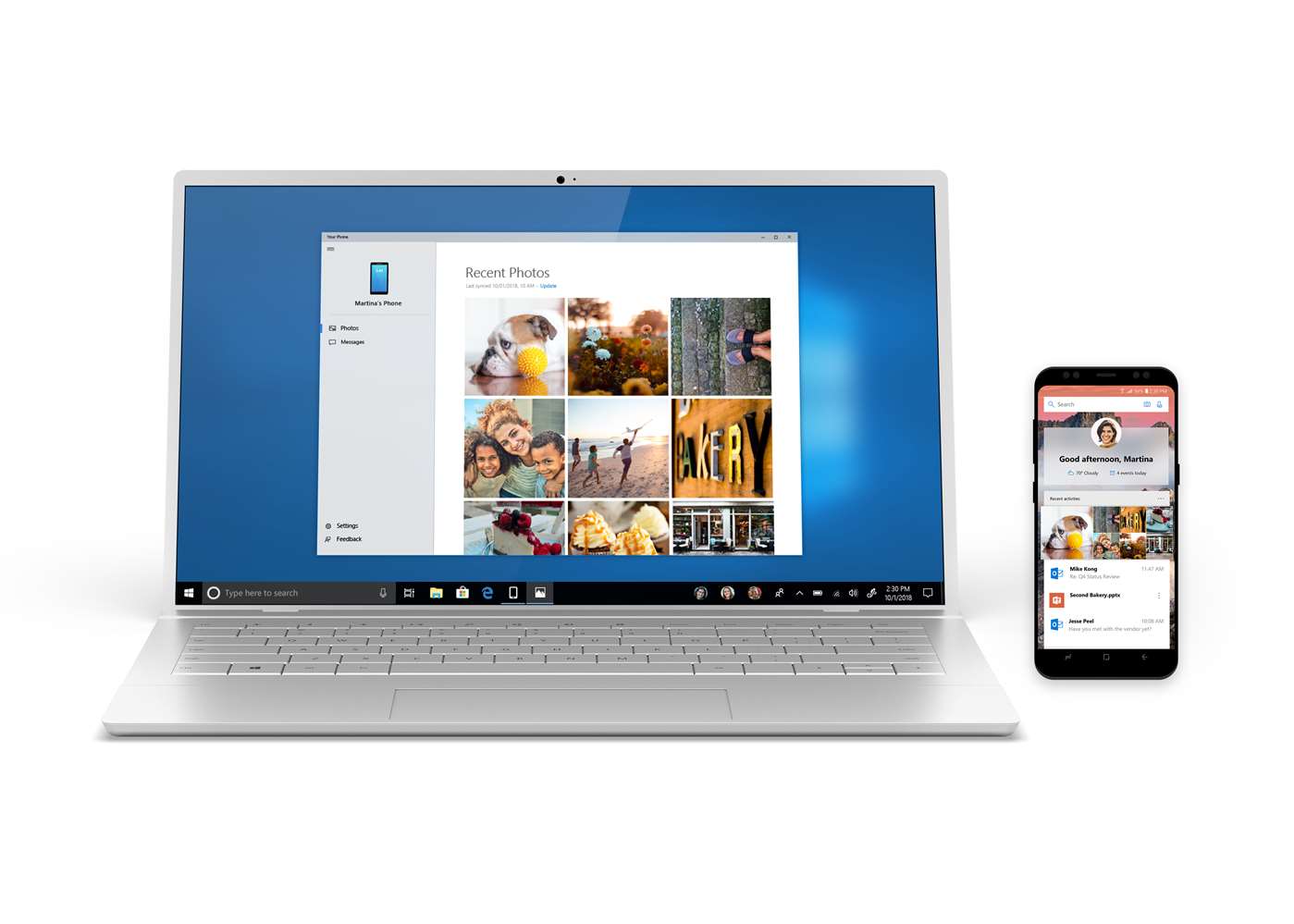
Android users can now view their phone content on Windows 10 [Update]
Two weeks ago, Windows Insiders got the chance to test out a new app called Your Phone. This app, for iOS and Android, lets users sync content directly from their phones to a Windows 10 PC.
If you’ve wanted to try out the app, but you’re not an Insider, we’ve some great news for you. Starting today, Your Phone is available to all, although it currently only works with Android devices.

Microsoft releases Windows 10 Redstone 5 Build 17738 to Insiders on the Fast ring
Microsoft is hard at work polishing the next big feature update for Windows 10, out in the fall. It released two new Redstone 5 builds last week -- Build 17733 (with Dark Theme for File Explorer) and Build 17735.
Today, the software giant pushes out Build 17738 to Windows Insiders on the Fast ring.

Need a rugged Oreo smartphone without (too many) compromises? Try the Poptel P10
As Samsung, Apple and even the likes of OnePlus push out flagship smartphones with ever-larger price tags, it's little wonder that people are increasingly seeking out cheaper alternatives. Where there's demand, supply follows, so there's no end of choice when it comes to handsets that pack a punch without breaking the bank.
It's possible -- probable, even -- that you've not heard of Poptel, but the Poptel P10 is a phone that's worthy of a second look. No, it's not a flagship-killer. No, it's not anything even approaching a competitor for the iPhone X or Samsung Galaxy Note9. But it is a highly capable dual-SIM phone which is waterproof, dustproof and shockproof, that boasts good looks, a slim design, and a pair of decent cameras.
Zorin OS 12.4 Linux distribution is here -- switch from Microsoft Windows 10 now!
I'm not a Microsoft "hater" at all. With that said, I am not a fan of the state of Windows 10. The privacy issues alone are a reason to avoid the operating system, but that is hardly the only concern. For instance, Microsoft has been pre-loading tiles for games like Candy Crush and other apps -- a move that shows major disrespect towards its customers. Not to mention, the "Insiders" program is just a way for the company to get free beta testing -- Microsoft is all too happy to treat Windows 10 users as guinea pigs. It is all very shameful.
These days, if someone asks my advice on buying a computer, I recommend purchasing a Mac, Chromebook, or PC with a traditional desktop Linux distribution, such as Ubuntu. If you are happy with your current computer, but hate Windows 10, installing a Linux distro is very easy nowadays. I often suggest that Windows switchers try Zorin OS as it has a familiar interface. Today, that excellent operating system reaches version 12.4.

Finance remains top target for phishing attacks as scammers exploit GDPR
New figures from Kaspersky Lab show that more than a third (35.7 percent) of phishing attempts in the second quarter of 2018 attempts were related to financial services via fraudulent banking or payment pages.
The IT sector was second hardest hit, with 13.83 percent of attacks targeting technology companies, a 12.28 percent increase compared to Q1.

Turkey to boycott US electronics as Trump implements ZTE and Huawei ban
Donald Trump has signed the Defense Authorization Act into law which imposes a watered-down ban on ZTE and Huawei products by the US government and IT contractors. The ban also covers a number of other Chinese telecoms manufacturers.
There has been much to-ing and fro-ing about whether these sanctions would actually be introduced, but now and for the next two years they will be in place -- something Huawei denounces as "ineffective, misguided, and unconstitutional". But while this latest bill signing sees Trump wielding his power, the president will be unimpressed by Recep Tayyip Erdoğan -- the president of Turkey -- saying his country will boycott US electronics.