
Google is making YouTube and other services delightfully free of political ads... in Europe
The nature of modern-day politics means that parties of all colors, all leanings, spend millions on advertising -- it is something that was painfully apparent during the run-up to the US presidential election. Technology firms and social media platforms are under a lot of pressure to take steps to prevent election interference, and to increase transparency.
This is something that has been playing out in Europe with regulation on Transparency and Targeting of Political Advertising (TTPA) due to come into force in the EU. With concerns about the, “operational challenges and legal uncertainties” this could lead to, Google has announced that it will not only will stop serving political advertising in the European Union, but will do so before the TTPA comes into force.

Transcend unveils CFX735 CFast card for secure and high-performance storage
Transcend has introduced its new CFX735 CFast card aimed at professionals who need reliable data storage. This card comes equipped with built-in write protection technology, catering to applications that demand secure and stable data handling.
The CFast card is built using 112-layer 3D NAND flash technology and connects via a SATA III 6Gb/s interface. This ensures impressive read/write speeds and large storage capacities, making it suitable for data-heavy operations. The CFX735 model can handle temperatures ranging from -5°C to 70°C, making it versatile for various working environments.

Gemini app launches for iPhone bringing Google AI assistant to Apple users
Google has released its Gemini app for iPhone, giving Apple users the chance to experience the company’s personal AI assistant through a dedicated app. Available for download in the App Store here, the Gemini app expands the ways iPhone owners can access Google’s AI, previously limited to the Google app or web browser.
This new app offers iPhone users a focused experience designed to enhance learning, productivity, and creativity. A highlight of the app is Gemini Live, a conversational feature that allows for fluid, back-and-forth interactions. Users can interrupt, change topics, or ask follow-up questions naturally, adding a more human touch to AI interactions. With 10 different voice options and support for over 10 languages, it offers a customizable user experience that wasn’t previously available through other versions of Gemini.

Satechi unveils portable NVMe SSD enclosure and XR hubs for high-speed storage and power needs
Satechi is stepping up its lineup with the launch of the Mini NVMe SSD Enclosure and two new Mobile XR Hubs, aiming to meet the demands of users needing fast storage and power on the go. These products are designed for mobile gamers, photographers, videographers, and XR enthusiasts looking for portable, versatile solutions.
The Mini NVMe SSD Enclosure offers speeds up to 10Gbps, making it an attractive option for those who need efficient, high-speed file management. Supporting 2230mm NVMe drives, this enclosure leverages Gen 2 USB-C for quick transfers, ideal for anyone looking to streamline their workflow. It features a tool-free, swappable SSD design, so users can easily switch out drives up to 2TB without any hassle.

New platform protects organizations by assuming they've been breached
Most organizations now recognize that some form of cybersecurity breach is a matter of when rather than if. So why not just assume that the site has been breached in the first place?
That’s exactly what Tide Foundation has done with its new platform. TideCloak is an identity, immunity, and access management system that starts with a 'breach assumed' approach.

Get 'The AI Value Playbook' for FREE and save $35.99!
The AI Value Playbook is a crucial resource for those who want to understand how to leverage AI to drive business value, drawn from the firsthand experience of those who have been implementing this technology successfully.
The book focuses on questions frequently posed by leaders and boards. How can businesses adapt to these emerging technologies? How can they start building and deploying AI as a strategic asset to drive efficiency? What risks or threats need to be considered? How quickly can value be created? This book is a response to those demands.
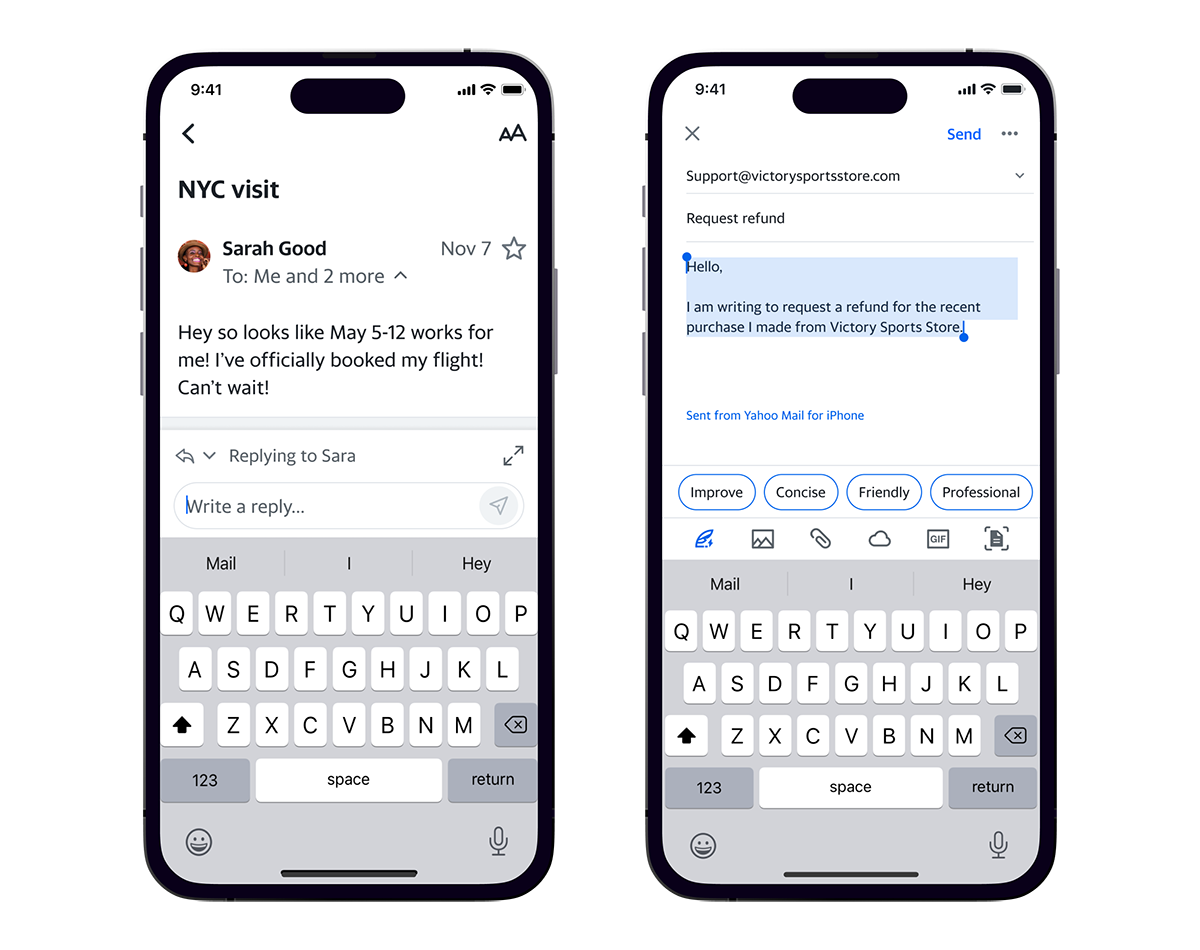
Yahoo Mail launches app update with AI features
Yahoo Mail has released an updated mobile app featuring AI-driven tools, a messaging-inspired design, and new gamification elements aimed at enhancing inbox management. The app introduces features that help users organize their emails, compose responses more efficiently, and perform actions directly from the inbox view.
“We know people struggle to keep up with their inbox volume and with organizing the messages that matter most,” said Rob Gelick, General Manager of Yahoo Mail. “We want to make email more manageable, useful, and feel less like ‘work’ by powering the experience with AI features that make reviewing emails fast and efficient.”
AI and hiring
The advent of artificial intelligence inspired a great deal of fear in the workplace, especially regarding job displacement. As AI's potential became more apparent, workers in virtually every industry feared they would be replaced by an AI-driven alternative that could work faster and for less pay.
To date, those fears have been mostly unfounded. In fact, a recent study of nearly 3,000 different workplace skills determined none of them were “very likely” to be replaced by generative AI.

BIOSTAR MT-N97 industrial computer targets system integrators and AIOT development
BIOSTAR has introduced the MT-N97 industrial computer, a fanless and compact system designed for modern industrial needs. This PC is aimed at supporting applications in automation, edge computing, and AIOT (Artificial Intelligence of Things) development, promising quiet and stable operation for demanding environments.
At the core of the MT-N97 is an Intel Alder Lake N SOC Processor, specifically the Intel N97. This quad-core chip runs up to 3.6GHz while maintaining a 12W TDP (Thermal Design Power), balancing power efficiency with capable performance for continuous use without excessive heat output.

AI redefines priorities for IT leaders
A new survey from Flexera shows that 42 percent of IT leaders say they believe if they could integrate AI, it would make the most difference to their organizations.
The study surveyed 800 IT leaders from the US, UK, Germany and Australia to determine how IT decision makers' priorities have evolved over the past 12 months and outline their focus for next year.

The winds of change: Why 2025 could prove transformative for ethereum
Sometimes the tides gather at the edges of what is, churning with quiet violence and dare something new to rise up. 2025 looks like one of those moments when you look at Ethereum. Under all the talk of cryptocurrencies, decentralized economies and digital revolutions is something far more basic: the slow, relentless toppling of systems that no longer serve the people.
A quiet question is starting to whisper: is Ethereum just a new piece on the board or the whole game?

This free app finally fixes one of Microsoft Windows' most annoying features
If you've ever tried to save a file in Windows and ended up playing a game of "hide and seek" with your own folders, you're not alone. It seems Microsoft has a grand vision for where our files should live, even if it has little to do with what we actually need.
Open the "Save As" dialog, and you'll find that Windows is practically begging you to save in its favorite spots -- like OneDrive, the Documents folder, or any other “default” that Microsoft has deemed worthy of your files.

Skills gap leads enterprises to outsource cybersecurity
A new survey of over 1,700 senior decision makers and influencers in leadership, technology and security roles across Europe finds that 48 percent manage their security operations in house compared to 52 percent who use a third party.
The study from Logpoint finds more than a quarter (28 percent) of UK businesses intend to outsource security over the course of the next two years.

Bluesky thinking -- why left-wingers are leaving X and why X will get over it
Are you still on Twitter (sorry, X)? You can tell us, we won't judge. If you are you may have noticed something interesting since the recent US election.
Celebrities along with people and organizations of a left-wing persuasion have been announcing -- in a markedly flouncy manner it must be said -- that they're leaving the platform. This peaked yesterday with the UK's standard bearer of the liberal left the Guardian broadcasting its intention to depart X -- on X, ironically.
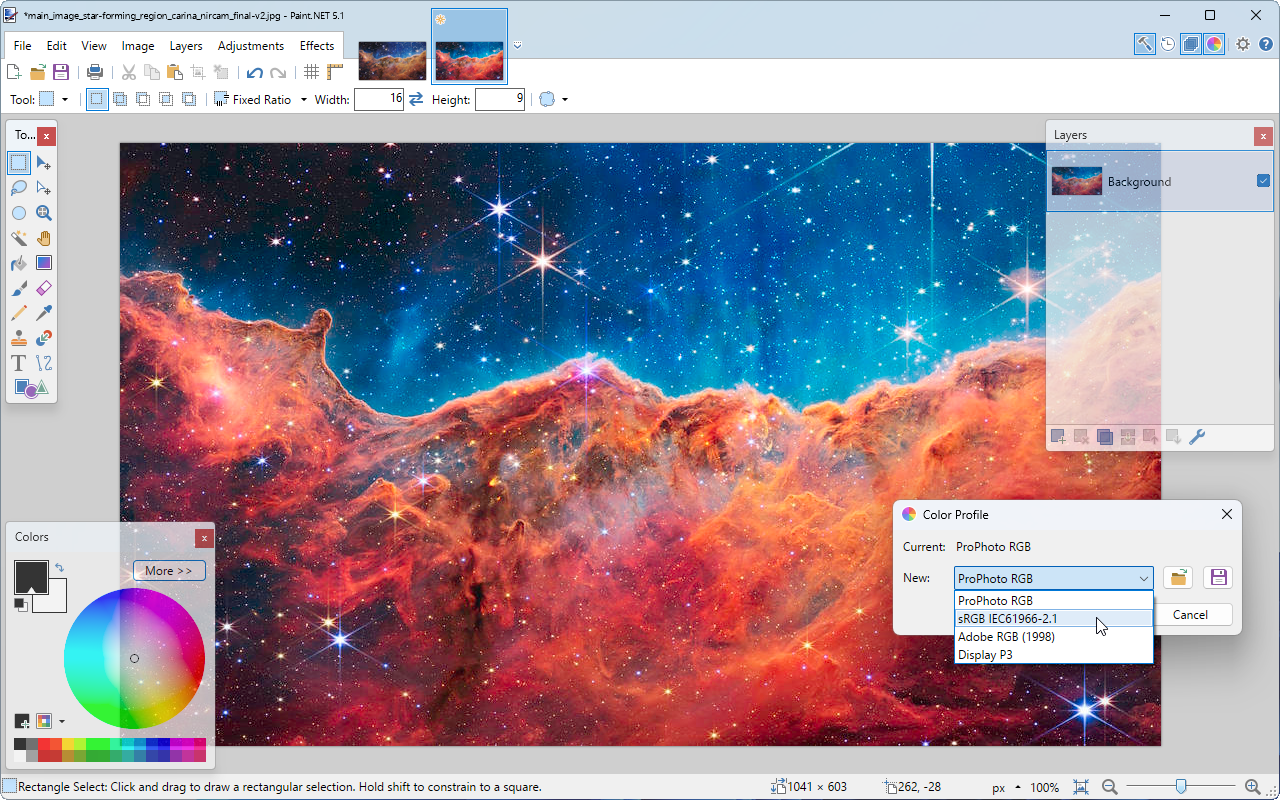
Paint.NET 5.1 unveils color management support, new and improved effects
Rick Brewster and dotPDN LLC has released Paint.NET 5.1, the first major point release in the Paint.NET 5.x series. It comes just under two years after Paint.NET 5.0 first saw the light of day.
The major highlight is support for color management -- ensuring images with embedded color profiles can now be displayed correctly in Paint.NET. The feature is effectively automatic -- when an image containing an embedded color profile is loaded into Paint.NET 5.1, it’ll display according to the embedded profile. Users can then switch to different ICC color profiles via the new Image > Color Profile… dialog.



