
Bag yourself $15,000 as an Azure or Project Spartan bounty hunter
It's not unknown for technology companies to run bounty programs that reward bug hunters for unearthing problems with software. Discover a security vulnerability and you could be in line for a nice cash bonus. Microsoft is one firm that runs such a program, and today the Microsoft Bounty Program is being expanded -- with a particular focus on Azure and Project Spartan.
Microsoft has already been asking for feedback about Windows 10 Technical Preview, but this is the first time a financial reward has been offered for pointing out security issues with any of its components. The maximum pay-out has been increased to $15,000 USD, so there's more incentive than ever to seek out problems and report them to Microsoft.
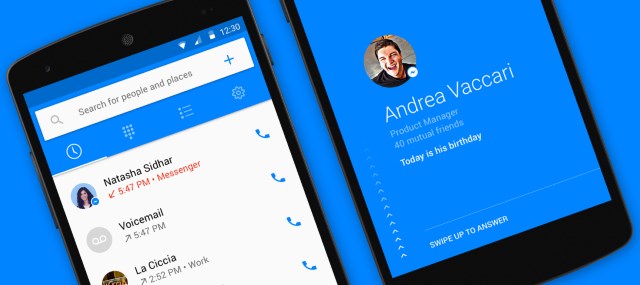
Facebook Hello tells you who's calling before you pick up
It's easily forgotten with the number of apps available, but mobile phones are primarily designed for making calls on the move -- whodda thunk it? When you receive a call you'll usually see the number of the caller, but this may not be helpful in identifying them before you decide whether to pick up. Facebook's answer to this problem is Hello.
This new app comes from the Facebook Messenger team and aims to tell you more about the person getting in touch with you even if you don’t have their number saved in your address book. Currently available for Android, the dialer app also allows for the blocking of calls from individuals.

Ubuntu Linux 15.04 Vivid Vervet is here
Today is Wednesday, aka "Hump Day". The middle of the work week can be quite the miserable day. If you are stuck in a soul-sucking corporate job, it means you still have a long way to go before the weekend brings sweet release.
Don't worry, people, I have good news; this is a very special Wednesday. Why? One of the world's best Linux-based operating systems, Ubuntu, sees a stable and final release of 15.04, codenamed Vivid Vervet (it's a type of monkey). At the end of today's work day, you can hopefully go home and try out the latest version of the popular Linux distribution -- once the download links go live, that is.

Anonymous, LulzSec, Guardians of Peace... A guide to the most notorious hacking groups
In 2015, the number of cyber-attacks and data breaches being reported by companies and governments across the world does not appear to be decreasing. Many high profile attacks have taken place in the past year alone. As a result of government investigations into cyber-attacks, it was discovered that many of these attacks are not the work of a single criminal acting alone.
In fact, organized hacking groups are increasingly responsible for these incidents. As time goes on, the data breaches and attacks are becoming more devastating and authorities are looking to see who is behind these events in order to stop these groups from organizing further. As the world becomes more technologically integrated, cyber-attacks pose issues of national security that need to be addressed.

Corporate privacy policies are out of step with protecting sensitive data
Technology makes it easier than ever for businesses to collect data but that also means they have greater responsibility for looking after it.
Data protection specialist Druva has released the results of a new study conducted by Dimensional Research which examines companies' efforts to protect sensitive data, the challenges they face ensuring data privacy and gathers respondent views on protecting data privacy in the cloud.

You're more likely to be struck by lightning than hit by mobile malware
We constantly see stories about the latest threat from malware, particularly relating to mobile devices. But is it really as bad as it's made out to be?
No, says threat detection and containment specialist Damballa which is unveiling new research based on its big data analysis of almost half of US mobile traffic.

Safari is king of the mobile browsers -- which could be bad news for Google
Google’s dominance of the web is best illustrated by Mobilegeddon. The search giant has made changes to its algorithm, prioritizing sites that are "mobile friendly" and demoting those that aren’t. Google says that mobile-friendliness is just one of 200 signals that it uses to determine the ranking of results and that sites which don’t have mobile versions won’t disappear as a result of this change. That said, the truth is if Google says you need a mobile site -- that it approves of -- then you need a mobile site.
But while Google is forcing sites to offer mobile friendly versions or suffer the consequences, it’s Apple’s browser that the majority of people are using to access the web while on the go.

New tools help speed up the unlocking of business intelligence
Where business intelligence is concerned it's often the case that companies don't lack data. However, they struggle to use the information they have in a way that offers meaningful insights.
San Francisco-based cloud analytics provider GoodData is releasing some new additions to its platform to break down the barriers of traditional business intelligence and improve self-service options without compromising the IT department's need for data governance and integrity.

Microsoft confirms Windows 10 universal apps will work on HoloLens
Microsoft has launched a question and answer section for Windows Holographic and the HoloLens headset, sent in an email to Windows 10 'Insiders' currently testing the new updates to the operating system.
The FAQ answers ten of the most popular questions on HoloLens, before Microsoft’s annual BUILD conference on April 29th to May 1st. Amongst the answers, Microsoft details that HoloLens will be able to run Windows 10 universal apps.

Office 365 Video begins its worldwide rollout
Back in November we told you about Office 365 Video, although at the time it was only available for First Release customers. The service, if you recall, brings video sharing to the enterprise, allowing customers to manage and post, as well as making it available across all devices -- PC, tablet and phone. Microsoft also claims that it will be automatically optimized for each device.
Now the service is rolling out worldwide, so everyone can begin putting it to use for training videos, company messages and the like. Microsoft's Claire Tutill states that "Video is fast becoming one of the most powerful forms of communication, so this is a very exciting development for Office 365 users".

Cybercrime gets smarter and more complex
There are 85,000 new malicious IPs launched every day and the top phishing targets are technology companies and financial institutions.
These are among the findings of a new report from threat intelligence and security company Webroot. The Webroot 2015 Threat Brief provides the latest cyber threat trends collected from tens of millions of users and over 30 security technology partners.

iOS 8 vulnerability can send iPhones, iPads into reboot loop
At the 2015 RSA Conference, security researchers from Skycure showcased a new iOS 8 vulnerability which, if properly exploited, can send iPhones and iPads connected to a malicious hotspot into a reboot loop. The vulnerability affects both the operating system as well as apps which use SSL to communicate.
All that an attacker has to do to exploit the vulnerability is to set up a router in a "specific configuration", and allow anyone to connect (basically make it an open hotspot). The iOS 8 devices that connect will be affected, without the attacker having to have access to them.

Facebook revamps your newsfeed yet again
Facebook is, once again, making changes to the algorithm that controls what appears in newsfeeds. If you had ever been under the impression that you were going to see a chronological list of status updates from your friends in your newsfeed, numerous changes over the years will have put paid to that notion.
It has been a source of many a social networking grumble, and now Facebook is taking steps to address the issue. Depending on how you use Facebook, you may be connected to not only real-world friends, but also companies, celebrities and even TV shows. Your newsfeed has likely turned into less of a collection of bon mots from your mates and more of a stream of updates from entities you're only vaguely interested in. Now your friends will be given greater priority.

Mem Reduct: a memory cleaner which isn't rubbish
Let’s be frank: most memory cleaners are garbage. They’ll lure you in with bogus claims about fixing memory leaks, dazzle you with flashy interfaces and colorful graphs, yet usually make no difference at all to system performance (or even slow you down) because they’re doing something Windows does as required, all on its own.
If you still think they might help you anyway, there are a few more honest and capable tools you can try, and Mem Reduct is a great example.

Funding for SaaS businesses grows by 70 percent
Software as a Service (SaaS) is one of the biggest technology growth areas at the moment. That's reflected in the amounts of capital being pumped into the sector by investors.
A new SaaS Trends Report by Tibco Analytics and venture capital tracker CB Insights shows that funding for SaaS companies was $11.7 billion in 2014, up 70 percent over the past year. SaaS funding has tripled since 2011.



