
The top five capabilities SIEMs should have for accurate threat detection [Q&A]
Security Information and Event Management (SIEM) platforms are the centerpiece of many organization's security controls, but if these products aren't configured correctly they will produce too many false positives to be useful, and can even make overall threat detection worse.
Security analysts need to trust that their SIEM is detecting threats accurately. We spoke to Sanjay Raja from security analytics company Gurucul to discuss how SIEMs can be configured to offer accurate detection.
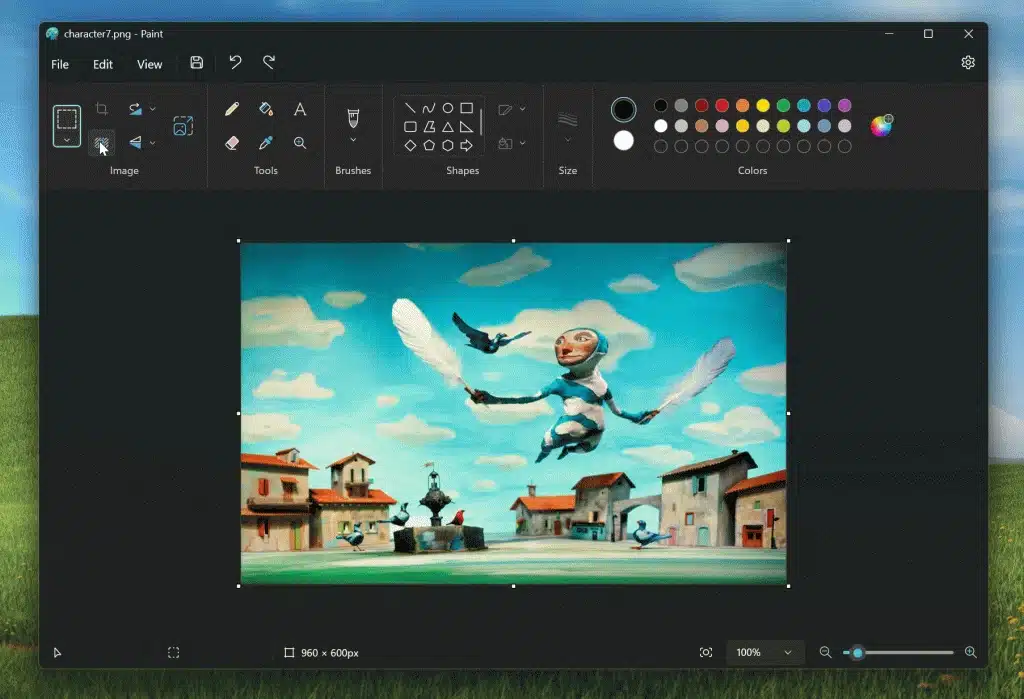
Microsoft is bringing one of the best features of Photoshop to Paint in Windows 11
Microsoft Paint has been the subject of ridicule for as long as it has existed, but much of the mockery is ill-placed these days. While it may not be the most advanced image editor in the world, there is a lot more to the app than it is generally given credit for.
Microsoft is not done with development of the app, updates rolled out to the latest Insider builds of Windows 11 show that the company is on the verge of bringing a Photoshop-level tool to Paint: background removal.

CISOs see budgets increase despite economic slowdown
A new report from Team8 shows that 56 percent of CISOs have had budget increases since 2022 despite the economic slowdown, while 25 percent saw no change and 19 percent cuts.
However, larger security departments have been most affected by budget cuts with 67 percent of those with 51-100 people seeing budget reductions.

Get 'Learning Spring Boot 3.0 -- Third Edition' (worth $35.99) for FREE
Spring Boot 3 brings more than just the powerful ability to build secure web apps on top of a rock-solid database.
It delivers new options for testing, deployment, Docker support, and native images for GraalVM, along with ways to squeeze out more efficient usage of existing resources. This third edition of the bestseller starts off by helping you build a simple app, and then shows you how to secure, test, bundle, and deploy it to production.

AI-driven search helps uncover cloud risks
It's crucial for organizations to have a complete and comprehensive view of all their cloud assets, but the process of discovery can be a difficult one, especially if multiple platforms are involved.
Cloud security platform Orca Security is launching a new AI-powered cloud asset search that is aimed at making the process more intuitive and available not only to security practitioners, but also developers, DevOps, cloud architects, and risk governance and compliance teams.

Guardians of privacy: The promise of fully homomorphic encryption in the AI and blockchain era
The rise of AI has been nothing short of meteoric, especially with the advent of extensive language models like ChatGPT. We're witnessing a technological tide that might not only match, but even eclipse the transformative power of the internet. Every corner of our world, from the intricate complexities of finance to the foundational elements of education, is currently in the throes of a radical transformation catalyzed by artificial intelligence.
Yet, as we march forward in this brave new world of machine learning and digital cognition, there's an ever-looming shadow: the challenge of data privacy. Every digital query, every command we voice, and every interaction we have with these advanced systems invariably deposits bits of our personal information into vast databases. These repositories, managed by the service providers, become de facto vaults of our digital identities. The gravity of this concern hasn't been lost on the world's decision-makers. Countries not yet willing to take the blind leap have started sounding the alarm, and corporate behemoths have begun implementing restrictions on the use of such AI-driven tools.

Hiding undetected: Why security teams can no longer overlook HTTPS decryption
Decrypting HTTPS (TLS/SSL) traffic at the network perimeter is a vital step in protecting against malware and other online threats. Most of today’s web traffic is encrypted and presents an obvious hiding place for threat actors to deliver cyberattacks, since many network security controls aren’t set to inspect encrypted traffic. Consider recent findings from WatchGuard’s Threat Lab in its Q4 2022 Internet Security Report (ISR). While the report showed an apparent decline in overall malware volume, the Threat Lab analysts found a much higher prevalence of malware being delivered over encrypted connections when they looked closer at decrypted HTTPS traffic. These results came from a mere 20 percent of devices decrypting TLS and indicate the other 80 percent would also show malware volume is up, but hidden -- which mirrors findings from previous quarters.
Despite this trend, it’s common for teams not to enable decryption at the firewall due to the complications it can present. The process requires resources to decrypt and then re-encrypt traffic passing through a gateway device, as well as next-gen firewalls (NGFW) or unified threat management (UTM) appliances that use significant computing horsepower, all which impact network performance. Then, introducing decryption while managing the performance of other security tools and their varying uses could be difficult. Today, however, tabletop UTM/NGFW solutions can perform this process at the speed of the incoming WAN connection. So now, users’ main objection is the initial configuration of TLS/SSL decryption, and the need for exceptions for certain applications.

How to speed up File Explorer in Windows 11
The vast majority of software bugs are, almost by definition, a problem. A bug can cause unexpected behavior, reduce performance, and cause endless other issues. But there is a bug in Windows 11's File Explorer that actually makes it better.
If you've ever thought that File Explorer would benefit from a speed boost, there's some good news. A strange bug can be exploited to noticeably improve performance in a split second.
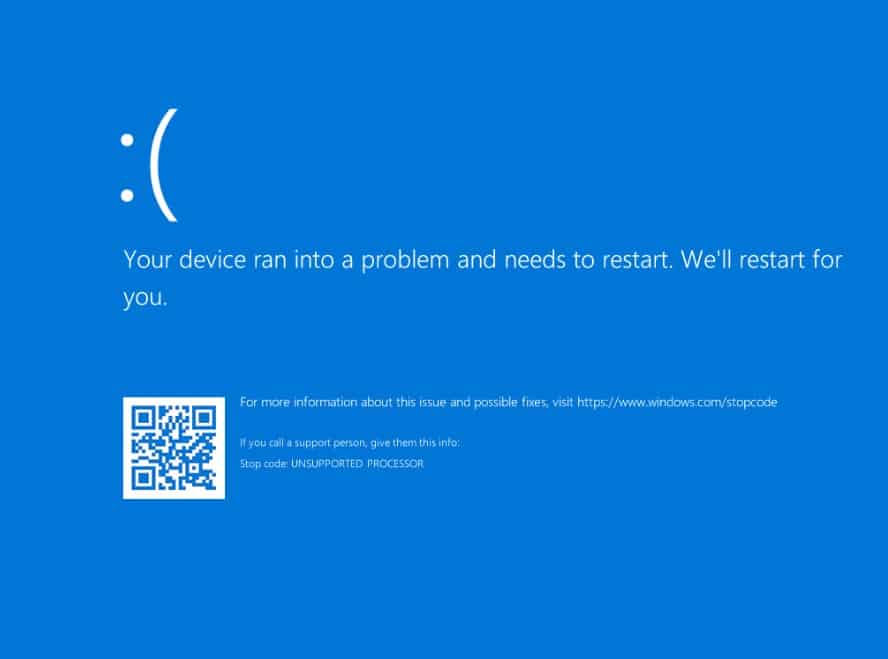
Fix the UNSUPPORTED_PROCESSOR error in Windows with a BIOS update from MSI
It is now a couple of weeks since a Windows 11 update resulted in a large number of people suddenly seeing UNSUPPORTED_PROCESSOR error messages.
At the time, the finger of blame was pointed at Microsoft, although the company was quick to suggest that the fault may be elsewhere. With the issue affecting MSI motherboards, the hardware manufacturer offered up a workaround. Now MSI has released a BIOS update that properly fixes the problem for Intel 700 and 600 series boards.

Samsung announces 4TB variant of its popular 990 PRO SSD
Let's face it, when it comes to solid state drives, Samsung’s offerings are some of the most reliable. That is why many people trust that company’s SSDs to store their important data. Today, Samsung unveils a new 4TB version of its wildly popular PCIe 4.0 990 PRO SSD.
The heart of this new 4TB offering is the eighth-generation Samsung V-NAND (V8) technology. Paired with an enhanced proprietary controller, this SSD is designed to handle almost anything you throw at it, from 3D/4K graphics work to data analytics.

AI chatbot simplifies Kubernetes management
Kubernetes management platform company D2iQ is launching new updates to its D2iQ Kubernetes Platform (DKP) that include DKP AI Navigator, an AI assistant that enables enterprise organizations to overcome the skills gap they face in adopting cloud-native technology.
DKP AI Navigator enables organizations to harness more than a decade of the D2iQ team’s experience. It's been trained on D2iQ's internal knowledge base, enabling customers to ask questions and receive real-time responses in a natural, intuitive way. This can reduce the duration and cost of system misconfigurations and downtime while helping organizations overcome the Kubernetes skills gap.

Lack of cybersecurity staff affects over 70 percent of organizations
The cybersecurity skills crisis has impacted 71 percent of organizations and left two-thirds of cybersecurity professionals saying that the job itself has become more difficult over the past two years.
New research carried out by Enterprise Strategy Group (ESG) and the Information Systems Security Association (ISSA) finds 66 percent of respondents believe that working as a cybersecurity professional has become more difficult over the past two years, with close to a third (27 percent) stating that it is much more difficult.

Get 'Excel All-in-One For Dummies' (worth $27) for FREE
Excel-erate your productivity with the only guide you'll need to the latest versions of Microsoft Excel.
Microsoft Excel offers unsurpassed functionality and accessibility for data exploration and analysis to millions of users around the world. And learning to unlock its full potential is easier than you can imagine with help from Excel All-in-One For Dummies.

As the cookie crumbles, ID resolution reignites customer experience
In today's digital world, one customer can have multiple identifiers. These identifiers track customer information, transactions, and interactions as they engage with a business through its web browser, mobile app, and in-store. Each of these touchpoints might capture different data about the customer, creating different identifiers. This can lead to customer data ending up in disconnected silos throughout the organization, impacting the company’s ability to target marketing and advertising efforts.
Without a comprehensive view of a customer's journey, brands struggle to understand consumers’ needs, creating a bad customer experience (CX). In fact, CX quality fell for 19 percent of brands last year, with 49 percent of customers stating they left a brand they had originally been loyal to in the last 12 months due to poor CX. With customer loyalty at stake, it’s more important than ever that brands use identity resolution (ID) resolution to improve CX, increase retention, and drive revenue.

Boards show confidence in their cybersecurity but still think they're at risk of attack
A new survey reveals that board members tend to feel good about their company's cybersecurity policy, but that many are still unprepared to face a cyberattack.
The study from Proofpoint surveyed over 650 board members across 12 countries and finds that 73 percent believe cybersecurity is a high priority for their board, 72 percent feel their boards understand the threats they face, and 70 percent agree they have adequately invested in resources.



