
Threat intelligence is a priority but organizations lack network visibility
New research from asset visibility and security company Armis shows threat intelligence has become a top priority, yet organizations don't have a clear view of their networks.
The study of 400 IT professionals across the UK shows the top challenges they faced in the last six months as: keeping up with threat intelligence, compliance with cybersecurity regulations and frameworks, staffing and recruitment, an ever expanding attack surface, and visibility into all assets connected to the network.

How to install the macOS Sonoma beta right now
Apple may have just announced macOS Sonoma and a full release may still be some months off, but there are going to be plenty of beta builds to play with in the meantime.
Starting right now, there is a developer build of this latest version of macOS. If you are particularly keen to try out all of the new features and enhancements that Apple has introduced, here's how to download that beta right now.
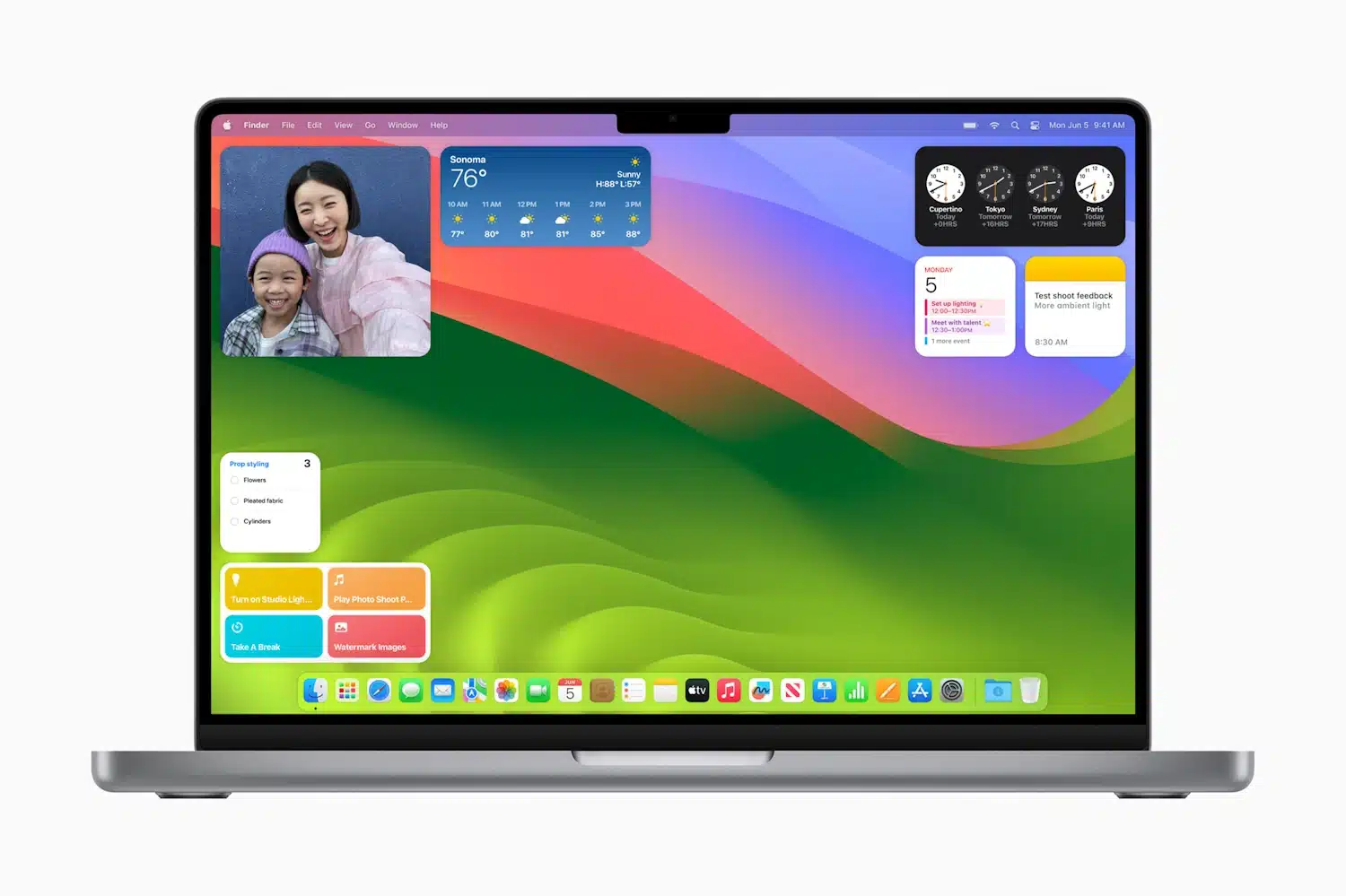
Apple announces macOS Sonoma with widget updates, gaming enhancements and much more
At its World Wide Developer Conference (WWDC) Apple made various hardware announcements, but the event wasn't just about the likes of Apple Vision Pro VR headset. Also revealed was the latest version of Apple's desktop operating system -- macOS Sonoma, or macOS 14.
Like Microsoft with Windows 11, macOS Sonoma sees Apple adding new widget capabilities and boosting the experience for gamers. Other updates include Presenter Overlay in video conferencing, new screensavers, and significant privacy updates to Safari.

Apple launches new 15-inch MacBook Air
The big hardware news from today's WWDC conference was Apple's exciting "Vision Pro" VR/AR headset. However, those expensive goggles were not the only new device. Actually, Apple launched a new 15-inch MacBook Air too.
This new laptop features a 15.3-inch Liquid Retina display. With a high resolution, 500 nits of brightness, and support for a billion colors, this display offers an impressive visual experience. Text is razor sharp, and the colors are vibrant and rich, making content come alive.

Apple's Vision Pro isn't the VR headset you were expecting, but it is the future -- for rich people
Last week, Meta officially took the wraps off Quest 3, its next gen VR product. Today at its World Wide Developer Conference (WWDC), Apple showed us the long rumored headset it's been working on for years. If you were expecting a VR device designed to take on Meta, you're going to be disappointed. What Apple has come up with is something incredible, but whether you'll want to buy it is another matter.
Apple's Vision Pro is a mixed reality headset that overlays apps on the real world, but there's more to it than just that. There's a reason that Apple has filed over 5000 patents to protect the technology inside it.

Silicon Power announces Cinema Pro PNV350 USB-C SSD
Today, Silicon Power announces its latest portable solid state drive. Called "Cinema Pro PNV350," the external USB-C SSD offers very fast performance thanks to its USB 3.2 Gen2x2 interface. Silicon Power says the design is inspired by "architectural concrete," but truth be told, it looks like a standard rectangle to me.
The entire body of the Cinema Pro PNV350 SSD is made of CNC-machined aluminum, not only giving it a sleek and modern look but also allowing heat to be conducted quickly and efficiently. The result is enhanced heat dissipation and maximum utilization of the heat-dissipating surface area, ensuring optimal performance even during demanding tasks.

Ransomware targets specific industries as attack success rate soars
Last month broke ransomware records -- and not in a good way. The latest report from Blackfog shows 66 publicly disclosed ransomware attacks, the highest recorded since the company began reporting in January 2020.
More concerning still is a significant uptick in the attack success rate, with a 154 percent increase over 2022.

How an IT asset checklist can set up CISOs for success [Q&A]
The Great Resignation and tech layoffs have pushed staff turnover to an all-time high. And with every personnel change, years of institutional knowledge are lost in the transition. That information can be critically important for security executives, like CISOs, who must be the ultimate stewards of organizational security across an ever-changing attack surface.
Organizational environments today are increasingly complex and constantly evolving, making it challenging to understand exactly what is at risk at any given moment. For CISOs joining an organization, it is vital to understand exactly what is on their environment to effectively secure it.

Microsoft is quietly rolling out Bing Chat support to web browsers that rival Edge
Thus far, Microsoft's artificial intelligence-powered Bing Chat has been exclusively available to users of the company's own Bing browser -- but this is starting to change.
Although there has been no official announcement, there have been numerous reports from users that they have been able to get Bing Chat to work without having to switch to Edge. Responding to queries about these reports on Twitter, Microsoft has now confirmed that it is gradually rolling out the AI-driven chat tool to different web browsers.
How data and analytics build a stable future for manufacturers
The CHIPS and Science Act promises a bright future for the U.S. semiconductor industry. The legislation aims to increase domestic production capacity, build a stronger workforce and encourage American innovation. But high-tech manufacturers can't sit around waiting to reap the benefits -- they must focus on revenue optimization now to set themselves up for success.
Experts forecast semiconductor demand to surge 6-8 percent per year, requiring manufacturers to double current production. Despite the CHIPS Act inspiring $200 billion in new commitments to U.S. manufacturing, the industry is unlikely to experience significant production capacity growth for several years. What should companies do in the interim? Improve data and analytics processes to build better business practices.

Walmart's cybersecurity: Don't try this at home
It seems that every week we hear of another cybersecurity breach. This year, organizations of all shapes and sizes have fallen victim to malicious crimes -- from Apple, T-Mobile and Uber, among many others -- and data breaches are costing U.S. businesses millions of dollars.
The emerging digital ecosystem has made every company a target, and as a result, organizations are investing in a range of cybersecurity measures to mitigate threats and enhance resiliency and recovery. As cybercriminals continue to evolve their tactics, it’s becoming increasingly challenging for organizations to keep up with the latest security measures. This highlights the need for ongoing cybersecurity investment and a proactive approach to threat detection and response. The question is, what are these measures, and is there a one-size-fits-all approach? Let’s explore.
Microsoft is killing off Cortana in Windows 10 and Windows 11 later this year
Given that it never really generated a huge degree of excitement, you would be forgiven for having forgotten about Microsoft's digital assistant Cortana. Now the company has announced that support for the Cortana app for Windows 10 and Windows 11 is coming to an end.
Microsoft has not made a huge fuss about killing off the app, slipping out the news in a support document rather than a blog post. But the end of support for the app does not mean that Cortana is disappearing altogether.

How do chemical manufacturers avoid the nightmare cyberattack scenario?
If you were to draw up a list of places you don’t want to experience a sudden and catastrophic shutdown as the result of a cyberattack, chemical manufacturing plants would be pretty high up there. In addition to halting business operations and production, the nightmare scenario of hazardous materials being released into the human population and the surrounding environment is ever-present.
But such attacks are becoming increasingly common and sophisticated. A 2021 UK government study, for instance, found that attacks on the chemical industry cost £1.3 billion. Over the years, such attacks have targeted an increasingly varied number of players in the industry too. In 2017, for example, attackers were able to gain control of vital safety systems at a petrochemical plant in Saudi Arabia. Drug manufacturers, chemical distributors, and even hazardous waste sites are among the other players in the sector to have been impacted by attacks. In January, meanwhile, hackers launched multiple attacks on Israeli chemical factories.
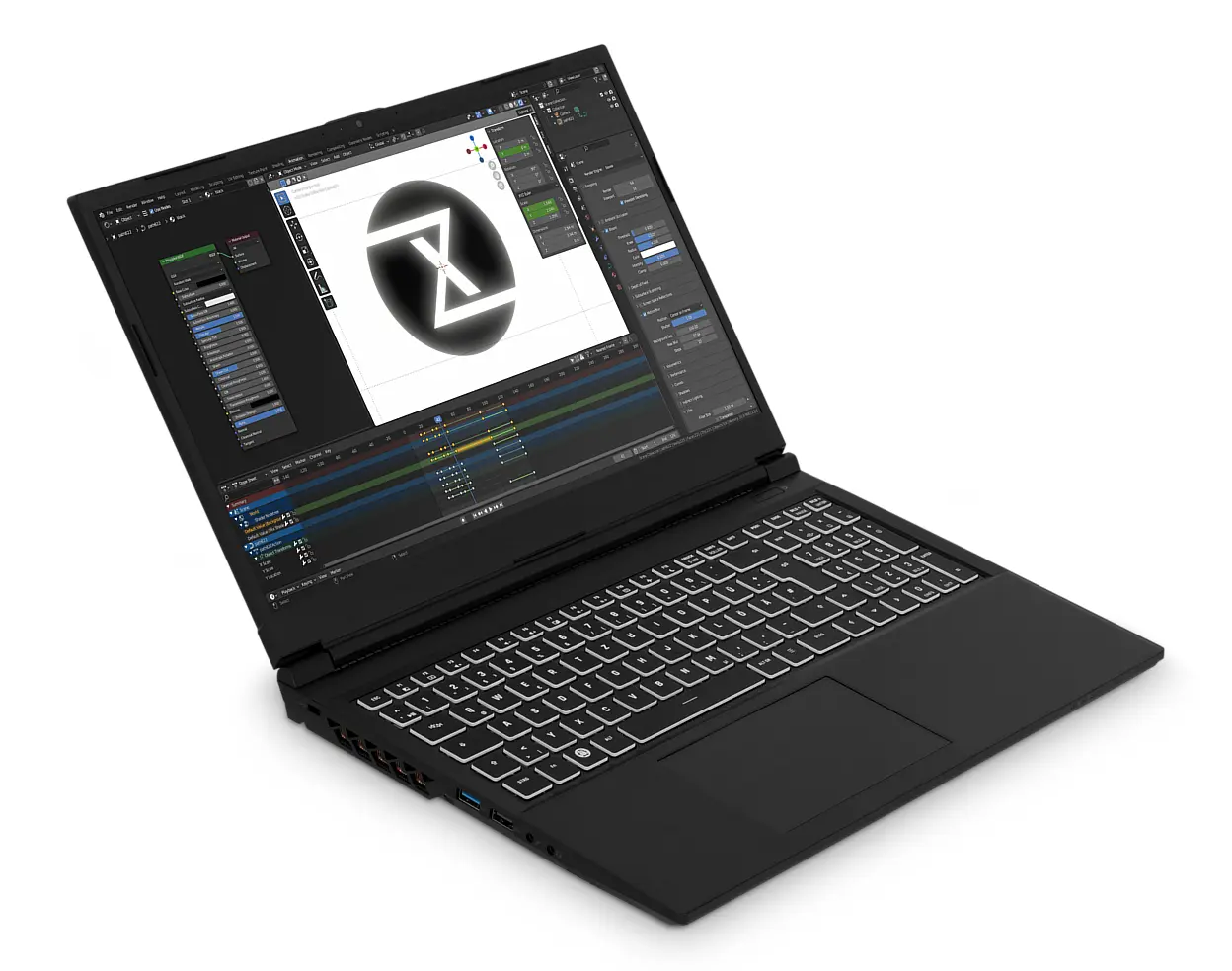
TUXEDO's new Gemini gaming laptops come with Linux or Windows 11
Today, TUXEDO, manufacturer of Linux-based computers, releases the second generation of its Gemini gaming workstation laptops. These high-end notebooks embrace the power of open-source software, delivering exceptional performance, unrivaled customization, and a liberating computing experience. Don't want Linux? That's OK. These laptops can instead be equipped with Windows 11 if you prefer.
At the heart of the Gemini series is the powerful Intel Core i9-13900HX processor. With 24 cores (8 performance cores and 16 efficiency cores) and an impressive 40 threads, this high-end processor is suitable for demanding tasks such as video rendering, 3D animation, and top-level gaming. Users can equip them with up to 8TB of SSD storage and up to 64GB of DDR5 RAM, ensuring ample space and high-speed performance for intensive tasks.

IoT and digital replicas: Powering up innovation with digital twins
The concept of digital twinning isn’t a new one. More than 40 years ago, NASA used an early form of digital twin technology to bring the Apollo 13 astronauts safely back to Earth. By replicating the real-life conditions of the crippled spacecraft in its simulators, NASA was able to identify the right strategies and procedures for achieving a successful return in the damaged craft and deliver this critical information to Apollo’s flight crew.
Fast forward to today, and digital twin applications are now being deployed by organizations eager to harness the power of virtual prototyping to reinvent their operations. All made possible by the growing prevalence of IoT devices that pull real-time data collected from physical objects, which is used to create digital twins that deliver unprecedented visibility into assets and production processes.



