
Cherry XTRFY MX 10.1 wireless keyboard offers triple connectivity and extended battery life
Cherry has introduced the Cherry XTRFY MX 10.1 Wireless, a full-size, low-profile mechanical keyboard that combines a slim design with high-end specs. Available to buy now and priced at $249 on Amazon, the keyboard supports triple connection modes, and can last up to 900 hours on Bluetooth.
The keyboard operates at 4000Hz when connected wirelessly and up to 8000Hz through USB-C, which means it reports keystrokes at a much higher frequency than other keyboards.

Tech investment is needed to fight geopolitical risk to supply chains
A new report finds that nearly three quarters (73 percent) of UK businesses expect geopolitical risk to intensify over the next 12 months, with 62 percent saying their supply chains can’t deal with the shifting geopolitical sands.
The study from Ivalua, based on a survey of 300 supply chain and procurement decision-makers in the UK, shows the war in Ukraine has negatively impacted confidence in their organization’s supply chain the most (77 percent). This is followed by US tariffs (75 percent), military exercises and testing disrupting major shipping straits (73 percent), tensions between China and Taiwan (62 percent), and the war in Gaza (58 percent).

The social media apps harvesting your data for AI
We all know that data is a valuable commodity, whether it’s to build marketing profiles or target advertising. Increasingly it’s also being used to train AI models, but do you know what the sites you use are doing with your information?
Data privacy and removal company Incogni has released its Social Media Privacy Ranking 2025 report, which ranks major social media platforms on user privacy, compliance, and overall data protection practices.

Raspberry Pi 500+ all-in-one PC debuts for $200 with mechanical keyboard
The Raspberry Pi Foundation has expanded its line of all-in-one desktop computers with the launch of the Raspberry Pi 5-powered Raspberry Pi 500+.
Priced at $200, the new keyboard PC blends nostalgic design cues from the home computers of the 1980s with modern performance.

Proton Mail launches new mobile apps for Android and iOS
Popular encrypted email service Proton Mail is rolling out brand new iOS and Android apps, offering users a faster, more modern and smoother experience.
Email started on desktop computers and was designed accordingly. As a result early mail apps could feel awkward with slow speeds, clumsy tabs unintuitive layouts. But today, phones are users' primary access to the internet. With this in mind, over the past year, Proton has embarked on an ambitious project to rebuild Proton Mail's iOS and Android apps from the ground up.

Corsair launches FRAME 4500X, a feature-rich PC chassis for high-end gaming and workstation builds
Corsair has added the FRAME 4500X to its range of PC cases, a mid-tower designed for high-end builds. The case combines a large glass front and side panel with a curved design that gives a clear view of internal components. It also provides a spacious interior and multiple airflow options aimed at keeping the internals cool.
The chassis supports up to 10x 120mm fans or 5x 140mm fans, with mounts on the top, rear, bottom, and power supply shroud. The included fans come in two versions: the RS120-R PWM ARGB or the iCUE LINK LX120-R RGB reverse-rotor fans. Both are designed to draw air into the case while keeping RGB lighting unobstructed. The iCUE LINK version connects through a single cable for fan speed and lighting control.
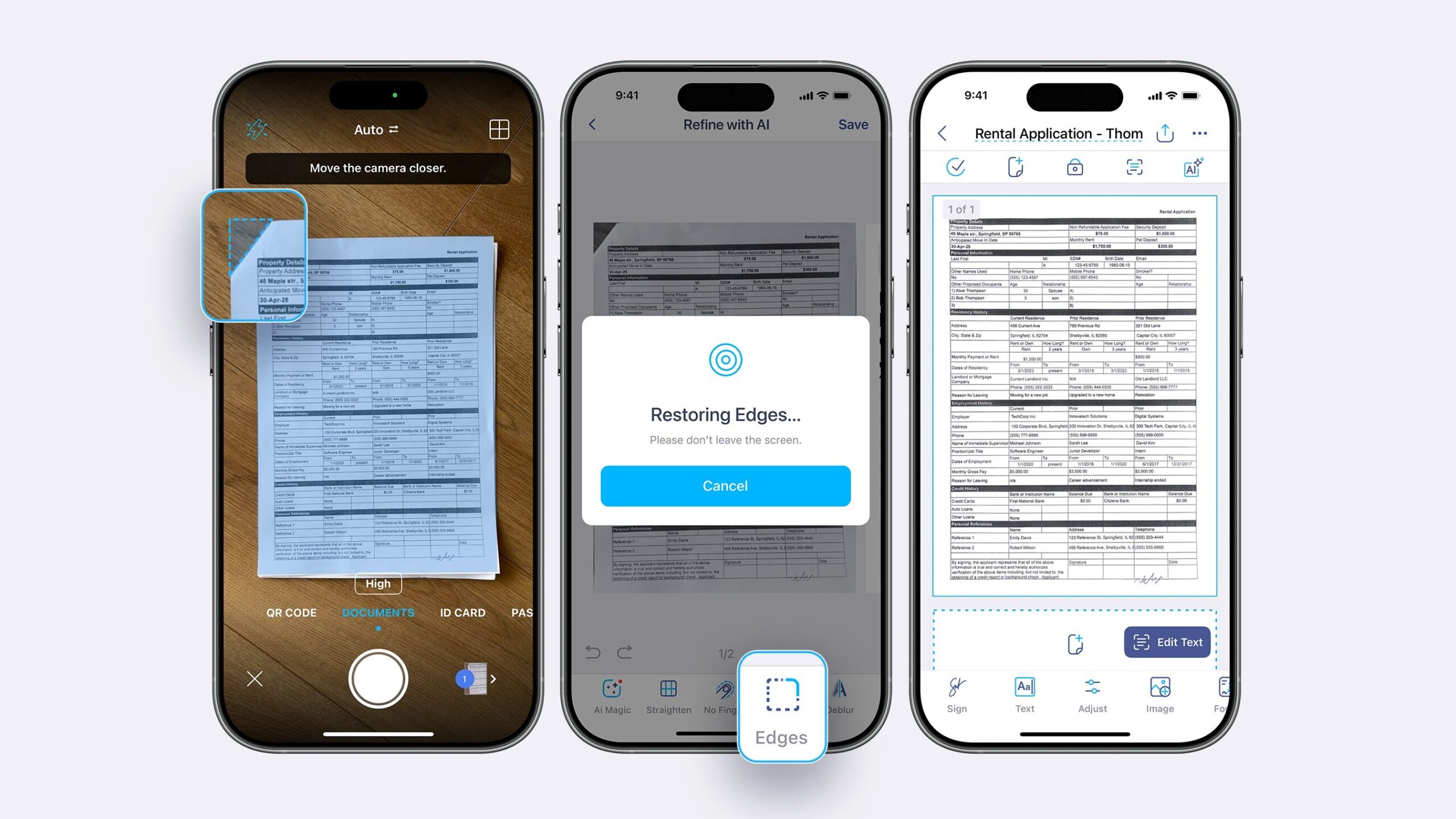
iScanner introduces AI edge repair to fix stapled and damaged document scans
Scanning documents with staples, bent corners, or clipped edges has long been a hassle for people who rely on mobile apps for paperwork. A new feature in iScanner, called Edge Repair, is designed to take care of that issue. By applying AI directly on the device, the app can smooth out rough edges and rebuild missing parts of a page so the final scan looks as it should.
Instead of forcing users to trim staples or re-scan pages to avoid cut-off corners, Edge Repair works behind the scenes to identify what is missing and restore it pixel by pixel. The creators say it can handle folds, obstructions, or tilted pages, producing a clean version without requiring any manual fixes.

ESPN Fantasy Football adds AI-powered weekly insights from IBM watsonx
IBM and ESPN are working together once more for the 2025 fantasy football season, introducing Fantasy Insights Built With IBM watsonx on the ESPN Fantasy Football app.
The new tool provides personalized, AI-powered recommendations based on over 36 billion insights generated throughout the season, helping fantasy managers make weekly roster choices with greater context and data-driven guidance.

Skeptic or realist? The contradictions in AI technology adoption
Research released today by The Adaptavist Group reveals deep-rooted contradictions in how companies are approaching and implementing AI technology.
The survey of 900 professionals responsible for introducing and onboarding AI across the UK, US, Canada, and Germany uncovers a major fault line between the 42 percent who believe their company’s AI claims are over-inflated -- the AI ‘skeptics’ -- and the 36 percent of AI ‘realists’ who do not.

Two-thirds of people working with AI are not in tech roles
We tend to think of artificial intelligence as being at the cutting edge of technical development, but new analysis from Multiverse shows that over two-thirds of people using AI at work in the UK are in roles not traditionally associated with tech.
The analysis of over 2,500 people on Multiverse’s AI apprenticeship programs reveals that over two-thirds (67 percent) are in non-tech roles -- that is, roles whose job titles don’t include keywords related to tech, data and AI. Instead, among the 50 most common ‘invisible’ roles are frontline public service, education, healthcare and construction roles, including nurses, doctors, librarians, pharmacists, therapists, lecturers and surveyors.

Logitech’s new Signature Slim Solar+ K980 Keyboard is powered by light
Logitech has announced an interesting new addition to its range of peripherals – a wireless keyboard that is powered by light. Despite the name, the Logitech Signature Slim Solar+ K980 Keyboard does not require sunlight, with the company’s proprietary Logi LightCharge technology allowing it to charge up using any source of light.
With the launch of the Signature Slim Solar+ K980 (and the Logitech Signature Slim Solar+ K980 for Business), Logitech is helping to address one of the issues that arises when using a wireless keyboard – battery life. There is no need to manually charge this keyboard, and the changes of running of juice are incredibly small.

AI is an even playing field -- how secure by design can tip the scale [Q&A]
Vibe coding is currently all the rage, with more than 97 percent of respondents to a survey earlier this year reporting having used AI coding tools at work.
The adoption of these tools only continues to grow but it comes with a catch, attackers are also employing the same techniques. We spoke to Pieter Danhieux, co-founder and CEO of Secure Code Warrior, to discuss how vibe coding is redefining the software development landscape, how malicious actors are also leveraging this technology and the need for organizations to implement secure by design strategies from the outset.

Disney+ is raising its prices yet again
Subscribers to Disney+ are being asked to dig deeper into their pockets as the cost of the streaming service goes up again. In what is becoming an annual occurrence, subscription charges are increasing across the board.
If you were hoping that opting for an ad-supported tier would help with avoiding price increases, think again – even this subscription package is going up. With Disney having irritated many of its customers after the (since reversed) decision to suspend Jimmy Kimmel, the company should expect an even frostier reception than normal to asking people for more money each month.
Microsoft releases out-of-band Windows 11 update to fix Office problems
Microsoft has been forced to release an unscheduled update for Windows 11. The newly unleashed KB5068221 update addresses issues with Microsoft Office running in virtualized environments.
For those who have been experiencing the issue, the fact that this update fixes things is reason enough to install it. But Microsoft has also used this update release to share details of a workaround for a SMBv1 share problem.

WhatsApp goes multilingual with new message translation feature
WhatsApp has announced the launch of message translations after years of requests from users. Gone are the days of copying and pasting foreign language text into a translation too – everything is now taken care of in the app.
The aim is to allow for easy communication, wiping out language barriers. This is something that can benefit users having one-to-one chats, but it is also helpful in group chats where two or more languages may be in use. For now, it is something that is rolling out to Android and iOS users, and users with Android devices have access to a unique extra feature.


