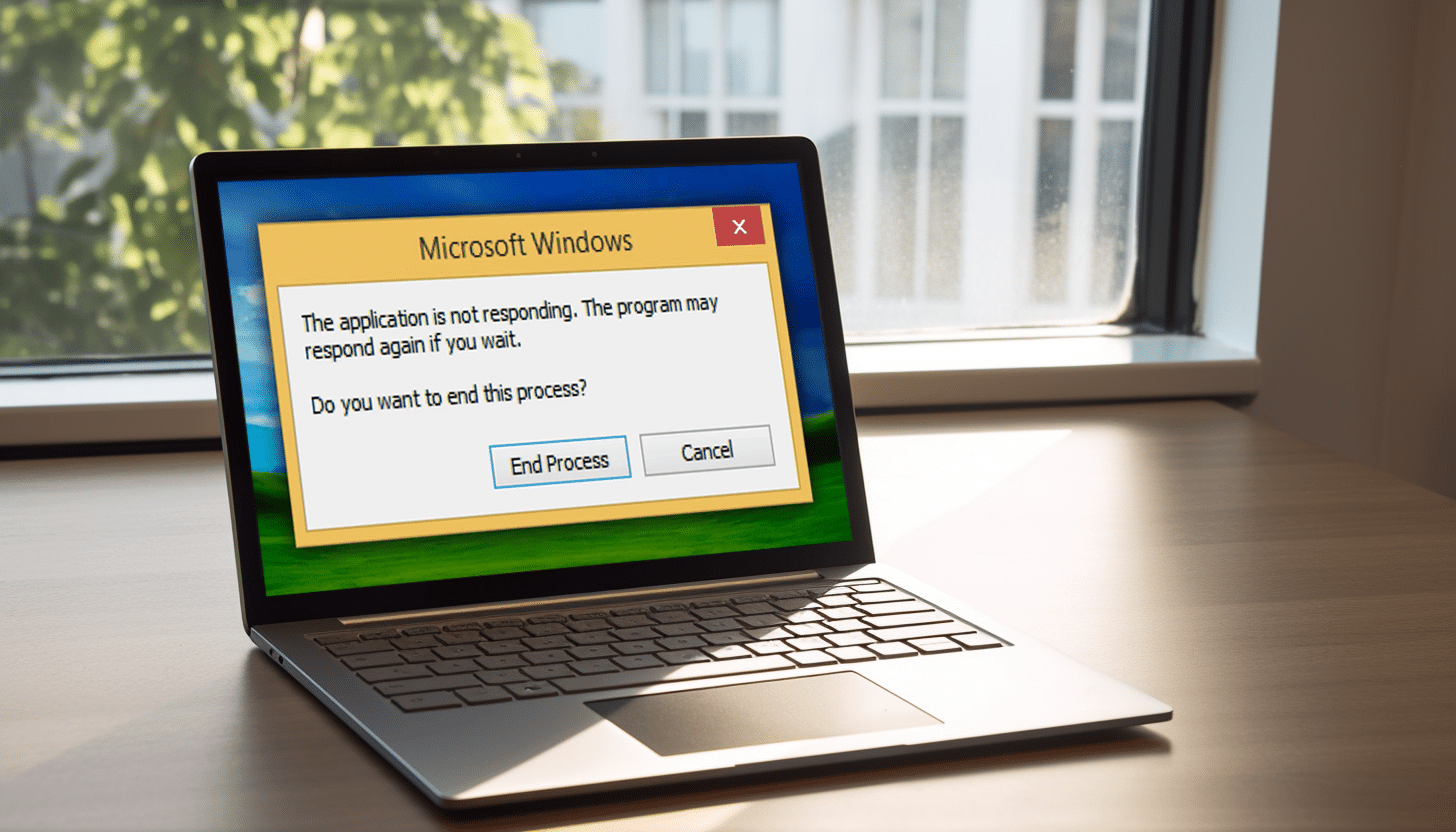
Watch 23 years' worth of programs failing to respond in Windows (from Windows 2000 to Windows 11) in just two minutes
In a nostalgic trip down memory lane, YouTube channel Nobel Tech has created a video showcasing the evolution of the infamous "This Program is Not Responding" Windows error message over the years.
The video starts with the prompt in Windows 2000 and takes viewers on a journey through time, ending with the message that shows up in the latest version of Microsoft’s operating system, Windows 11.

71 percent of employees have sensitive work data on personal devices
Allowing people to use their own devices for work comes with risks. A new report from SlashNext shows that 43 percent of employees were found to have been the target of a work-related phishing attack on their personal devices.
When it comes to securing BYOD hardware, 90 percent of security leaders say that protecting employees' personal devices is a top priority, but only 63 percent say they definitely have the tools to do so adequately.
Microsoft is bringing a new Registry Preview utility to PowerToys
This year has seen the addition of a veritable smorgasbord of tools to the PowerToys utility collection -- and the pace shows no sign of slowing. Recent arrivals include Mouse Jump and Paste As Plain Text, and next in line is a handy registry utility.
PowerToys developers are currently working on a new tool called Registry Preview. Designed with power users in mind, this upcoming module will make it possible to preview the effects of importing a .reg file into the registry as well as providing registry editing options.

Shadow data is a top concern for security teams
Shadow data is named as the number one concern around protecting cloud data by 68 percent of data security professionals.
A new study from Laminar reveals that the number of respondents expressing concern over shadow data has increased to 93 percent compared to 82 percent the year before.

Agent-based vs. agentless approaches -- how to implement cloud security
Implementing your security approach will depend on how you can translate your approach from strategy into reality. As part of this, you will have to make decisions on what tools you use based on the functions that they cover, how they help you create and use data, and how they work. This latter part is important as all security professionals have their own preferences. One of the big debates here is whether you use agent-based or agentless tools.
Using security tools that rely on agents can be an issue for some security professionals, while others will swear by their agent-based tool of choice, and you would have to pry it from their hands. The challenge here is when you have a combination of complex environments to consider, faster software development goals to support, real-time security pressures to contend with, and more data than you know what to do with. So what approach should you choose?

HEAT attacks: A new spin on browser exploit techniques
It is no secret that the web browser is becoming an increasingly popular target for cybercriminals looking to compromise an endpoint to gain entry to a network. The increased business use of the browser (remote work) on networks that lack the perimeter security infrastructure of traditional campus networks has made them easier to exploit. In recent months, we have seen an increase in cyberattacks and data leaks caused by browser-related security incidents, including a data breach caused by a phishing attack on Dropbox that gained the hacker access to over 100 of the company’s code repositories in November, and December’s CircleCi breach resulting from an infection of information-stealing malware.
Highly Evasive Adaptive Threats, or HEAT attacks, are a new spin on existing browser exploit techniques that make them much more dangerous. These attacks exploit browsers by leveraging features and tools to bypass traditional security controls and then attack from within, including compromising credentials or deploying ransomware. Comprised of known tactics such as phishing messages, HTML smuggling and dynamic drive-by downloads, these attacks frequently target SaaS applications and other web-based tools that are critical to productivity.

Reactive approach to cybersecurity is a problem for organizations
A new survey shows respondents feel a reactive approach to security is problematic for their organizations. 90 percent of them say they struggle with challenges when they react to cyber security problems as they arise.
The study, conducted by Forrester Consulting for WithSecure, shows most organizations currently approach cyber security on a reactive basis, with 60 percent of respondents saying they react to individual cyber security problems as they arise.
Microsoft is preparing to bring ads to AI-powered Bing Chat
In a move that will come as a surprise to just about no one, Microsoft has announced that it is "exploring" the idea of adding advertising to its GPT-4-based Bing Chat.
The company is framing the addition of ads to the AI-powered chat bot as a means of "driving more traffic and value to publishers from the new Bing". Microsoft says that it is seeking to do this by, among other things, "pioneering the future of advertising".

Microsoft Defender caught issuing false warnings about safe URLs
Microsoft has confirmed an issue with Defender which resulted in users being shown warnings about URLs that were entirely safe. The emails advised admins that "a potentially malicious URL click was detected", with affected users complaining that legitimate URLs, such as Zoom meeting links, were being flagged up as dangerous.
In addition to the false positives, the "View alerts" link included in the warning emails sent out to admins failed to provide any further information that could prove useful.
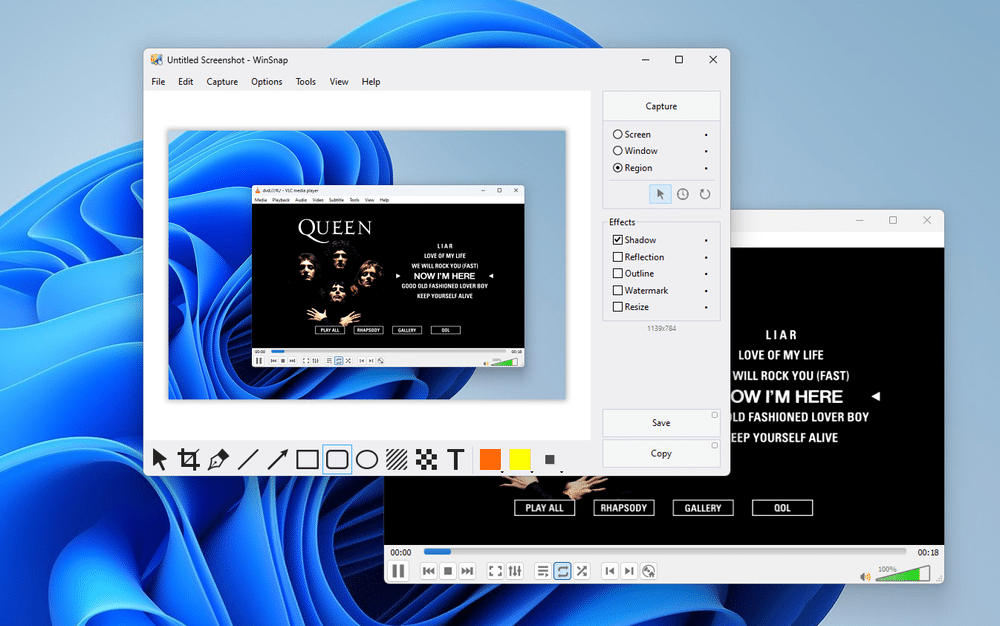
WinSnap 6.01 unveils modern facelift, major reorganization of tools
NTWind Software has unveiled a major new version of its powerful shareware screen capture tool for Windows. WinSnap 6.0.1 comes with a Windows 11-friendly facelift, a reorganization of its major tools and some useful improvements.
The biggest improvement is immediately apparent when the program first opens -- it now boasts a modern UI in keeping with the Windows 11 desktop, complete with support for automatic switching between dark and light modes.

The Last of Us Part 1 bombs on PC
The long awaited first part of the previously PlayStation exclusive The Last of Us game has been released on March 28, 2023 on Steam. The remastered version of the game has received praising reviews for PlayStation, but when you check the Steam ratings one day after release, you notice that they are mostly negative on the site.
In numbers, more than 4,200 of the 5,740 reviews are mostly negative, and this leads to the question how this could have happened. From Game of the Year to one that sits at the bottom of Steam’s ranking charts.

Get 'Difficult Decisions' (worth $18) for FREE
What do you do when the algorithm doesn’t have the answer?
Countless tools and frameworks claim to make decisions objective and bias-free. But in reality, the defining decisions that leaders face are complex ones with subjective information sources and conflicting courses of action. That’s why the toughest choices are left to the leaders, and that’s why formulas won’t answer them.

System76 refreshes Gazelle Linux laptop with Intel Core i9-13900H CPU and NVIDIA GeForce RTX 3050 GPU
Today, System76 unveils the latest generation of its Gazelle laptop. The Gazelle is a powerful and versatile laptop that is perfect for a wide range of users. It is a great choice for creative professionals, gamers, and anyone who needs a powerful laptop for work or play.
The Gazelle is powered by the 14-core Intel Core i9-13900H processor, which offers a max clock speed of 5.4Ghz. This new CPU provides up to 8 percent better performance compared to the previous generation of the Gazelle laptop. The computer also features an NVIDIA GeForce RTX 3050 GPU, which delivers exceptional performance for both gaming and graphics-intensive tasks.
Amid ChatGPT's rise to fame, how can enterprises work to eliminate AI bias?
Artificial intelligence continues to hog the headlines, as more people discover the power of tools like OpenAI’s DALL-E 2 and especially ChatGPT. These futuristic-seeming tools work by taking a human’s query or prompt and returning an intelligent textual or visual response.
From an enterprise perspective, AI adoption is growing rapidly. According to Forrester, spending on AI software is set to accelerate from $33 billion in 2021 to $64 billion in 2025 -- growing twice as fast as the overall software market. But while tools like ChatGPT may seem like magic, it’s important to understand these solutions aren’t perfect.

60 percent of organizations have had authentication breaches in the last year
Insecure authentication is a primary cause of cyber breaches and cumbersome login methods take an unacceptable toll on employees and business productivity, according to a new report.
The 2023 State of Passwordless Security Report, released by HYPR and Vanson Bourne, shows that 60 percent of organizations have reported authentication breaches over the last 12 months and that three out of the top four attack vectors are connected to authentication.



