
Microsoft releases KB5018427 update to address security issues with Windows 11 2022 Update
Microsoft has released its first update to Windows 11 22H2 / Windows 11 2022 Update in the form of KB5018427. This is a cumulative security update that includes the improvements from the previously released KB5017389 update, as well as additional "security issues".
While the update addresses quite a large number of problems with Windows 11 22H2, it does not fix the known issues with provisioning packages or slow file copying.

Acer Chromebook 516 GE proves PC gamers no longer need Microsoft Windows 11
Chromebooks sure have come a long way. What was once merely a glorified web browser running atop meager hardware has morphed into a legitimate Windows alternative for home, education, and business use. You can even get Chromebooks with high-quality hardware these days. Thanks to cloud-based video-game-streaming, Chromebooks can serve as gaming computers nowadays too.
Today, Acer launches its first-ever Chromebook designed specifically for gamers. Powered by a 12th Gen Intel Core processor and equipped with at least 8GB of RAM, the 16-inch Acer Chromebook 516 GE should be perfect for game-streaming platforms like NVIDIA GeForce NOW, Xbox Cloud Gaming, and Amazon Luna to name a few. And yes, this Chrome OS laptop has an RGB keyboard.
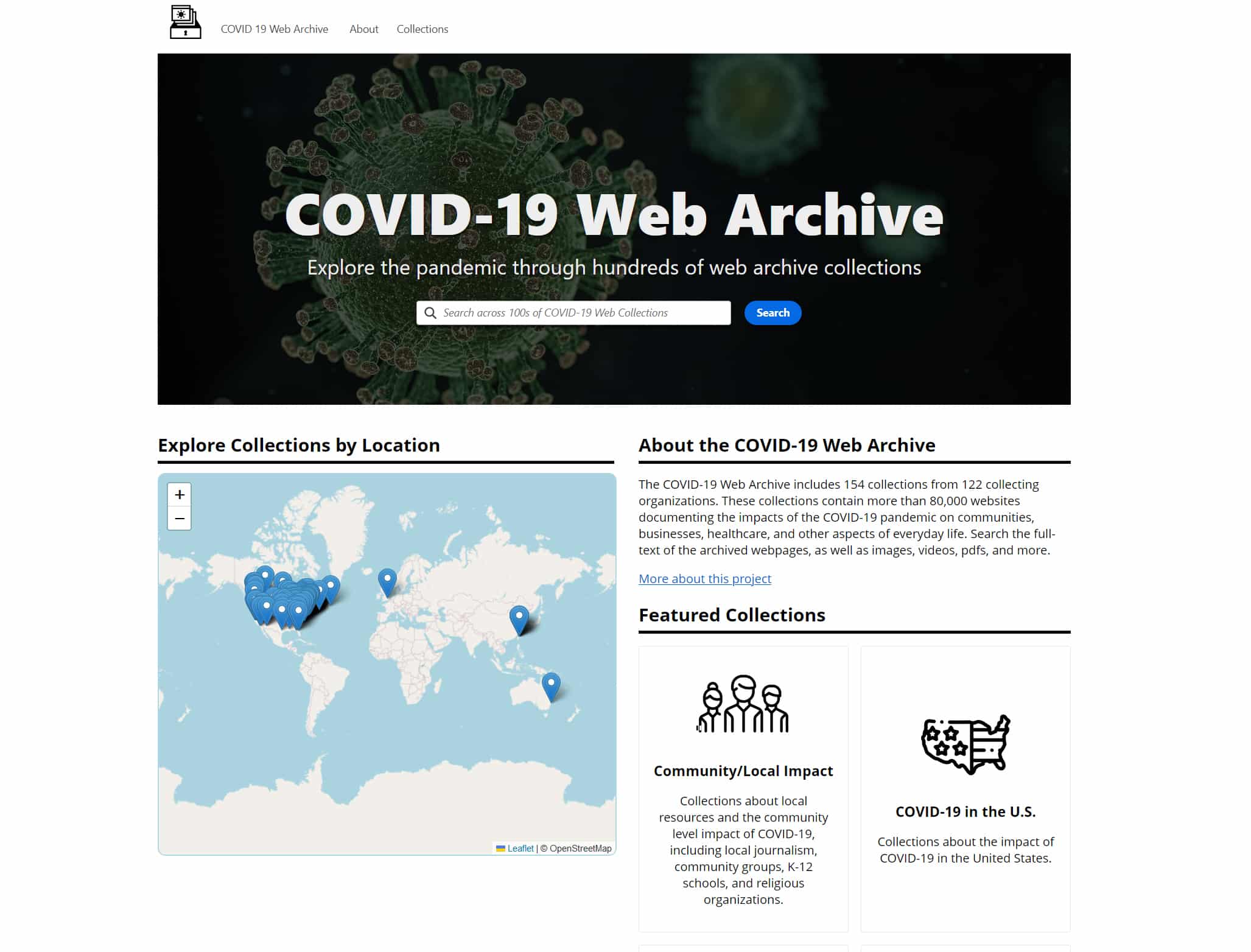
Internet Archive's new COVID-19 Web Archive lets you explore the pandemic from different perspectives
There are moments in everyone’s lives when they become aware that they are living through history. The COVID-19 pandemic, with its global lockdowns, was definitely one of those times.
In a bid to document the "personal, cultural, and societal impact" of the global pandemic from a number of different perspectives, the Internet Archive has created a giant COVID-19 web portal for anyone to explore.

Remote workforces at SMBs are being left unprotected
Cyberattacks and other threats aren't limited to large organizations, indeed SMBs are often targeted as they are seen as having fewer resources to devote IT security defenses, particularly related to remote workers.
A new survey from software company Devolutions bears out this view, with only 18 percent of SMBs checking all the requisite IT security boxes and 13 percent not implementing any essential IT security measures at all.

Protecting sensitive data in the 'golden age' of cybercrime
Like it or not, the global cybercrime industry has grown at a prolific rate over the last decade, making it harder than ever for organizations to keep sensitive data safe. To put the size of the issue into perspective, a recent IDC report found that around 50 percent of organizations have suffered unrecoverable data loss in the last three years. What’s more, the data also demonstrated how the pandemic turbocharged the issue, with attacks surging by an eye-watering 238 percent between February and April 2020. Simply put, the world seems to be in an extremely worrying 'golden age' of cybercrime at the moment.
As every business knows, a successful cyber-attack can have a devastating effect, potentially costing huge amounts of time and money to resolve, as well as inflicting major reputational damage, should sensitive information be taken or lost. In some cases, the organizations involved never recover.

Using just-in-time credentials to minimize access-based DevOps security risks
While the rapid adoption of DevOps processes has helped companies assume an agile product position in the market, security has lagged. Specifically, DevOps's prioritization of tools and automation has led to an explosion of machine identities that traditional waterfall-based security mechanisms cannot keep pace with.
Verizon's 2021 Data Breach Investigations report highlighted the extent of the problem by revealing that 61 percent of data breaches involved misused credentials data. These breaches are rarely incidents of a malicious actor stealing a human entity's password. Instead, hackers leverage expired or unused machine identities, also known as workload identities, to penetrate networks. As a result, some 92 percent of respondents to a recent Enterprise Strategy Group (ESG) survey indicated that they see workload identities as "critical" or "very important" risks.

One in five CISOs works over 25 hours overtime each week
According to new research from Tessian, 18 percent of UK and US security leaders work over 25 hours extra a week, double the amount of overtime they reported in 2021.
On average, they work 16.5 hours over their contracted weekly hours, up from 11 hours in 2021. Also three-quarters of security leaders say they aren't able to always switch off from work, 16 percent of these say they can rarely or never switch off.

Consumers want businesses to be more transparent about handling data
Consumers want to see more transparency from businesses around how their data is handled, according to the Cisco 2022 Consumer Privacy Survey.
The survey also shows that while consumers are supportive of artificial intelligence -- 54 percent are willing to share their anonymized data to improve AI products -- they are concerned about how businesses use AI, with 65 percent having lost trust in organizations due to their AI use.

UK sees one case of fraud every 85 seconds
A new study finds that £95 ($105) is lost to fraud every second in the UK. This is according to analysis by fraud prevention specialist Outseer of all the reported incidents of fraud to Action Fraud -- the UK's national reporting center for fraud and cybercrime -- between 1st July 2021 to 30th June 2022.
The data shows one case was reported to Action Fraud every 85 seconds and reported losses totalled over £3 billion ($3.31 billion) during the 12-month study period.
YouTube launches @ handles for channels
YouTube has announced that creators can now make use of @ handles for their channels. The move is a long time coming and the aim is to help increase engagement on the platform.
With the introduction of handles, YouTube is making it easier for users to mention others in their comments and more. Handles are rolling out over the next month, and YouTube says that it will notify creators when they are able to choose one for their channel.

Oracle releases VirtualBox 7.0.0 with full Windows 11 support
There are plenty of virtualization tools to choose from, but if for anyone looking for one that offers solid support for a wide range of host and guest operating systems, it's hard to go wrong with VirtualBox. Bringing support for Windows 11 -- something previously available in the beta builds -- Oracle has now released VirtualBox 7.0.0.
As has been the case in the past, VirtualBox 7.0.0 is available for Windows, Linux and macOS (as well as Oracle's own Solaris), but this release is about more than adding full Windows 11 support. There are also new options for cloud-based virtual machine, as well as improved security and much more.

Considerably more businesses running Windows 7 than Windows 11
After Microsoft launched Windows 10 back in 2015 it devoted a lot of time and resources to -- shall we say -- 'encouraging' people and businesses to make the switch from Windows 7, even kindly going as far as to automatically upgrading their systems for them.
Things are very different with Windows 11 as Microsoft is happy for the new OS to coexist alongside its predecessor, for the time being at least. There is a downside to this approach however, as it means there’s not the rush to upgrade that Microsoft will have been hoping for, to the point where significantly more businesses are running Windows 7 than Windows 11, despite the former having reached end of life ages ago.

Cybersecurity fears likely to make businesses Metaverse averse
The virtual world of the Metaverse is already attracting people to attend virtual events and play games. It also has the potential for businesses to make money -- research from McKinsey suggests it could be a $5 trillion industry by 2030.
However businesses are still wary of the additional challenges, particularly with regard to security. New research carried out by YouGov for app security company F5 shows six out of 10 respondents say the Metaverse has introduced security complexities that their organization may not be equipped to address.

How Kubernetes and AI will combine to deliver next-gen services [Q&A]
The popularity of Kubernetes has led to its rapid adoption, but as with any advanced technology, the benefits come alongside challenges.
Being able to take full advantage of the technology means understanding what it can offer and how it fits with other developments like artificial intelligence. We spoke to Tobi Knaup, CEO of independent Kubernetes platform D2iQ, to find out about the current state of Kubernetes and what it promises for the future.

Silicon Power Boost Charger QM25 offers both USB-A and USB-C charging
If you are anything like me, you have several devices that use various chargers and cables. For instance, I recently went on a cruise with an iPhone and a Kindle. For the iPhone, I have a USB-C to lightning cable. For the Kindle, I have USB-A to micro USB cable. When packing for my trip, I had to pack both a USB-A and USB-C adapter so I could charge both devices. Isn't there a better way?
Yes, actually. Had I planned better, I could have purchased a single wall adapter that offered both USB-C and USB-A ports for simultaneous charging. This would have allowed me to pack less and use fewer outlets in my room. While there are plenty of these wall adapters on the market, a diminutive new model from Silicon Power, called "Boost Charger QM25," looks quite nice.


