
Cybercriminals recruit malicious insiders via the dark web
Cybercriminals can use malicious insiders as a direct means to access sensitive company resources, stealing confidential data or using the access to deploy a devastating cyberattack. New research shows that they’re actively searching for insiders from various organizations via the dark web.
Over the past 12 months, the team at threat exposure platform NordStellar has identified 25 unique dark web posts seeking out insiders. A significant portion of these posts focus explicitly on insiders who work for social media or cryptocurrency platforms.

Google is discontinuing its dark web report security tool
Google has suddenly – and quietly – announced that its dark web report is to be discontinued. Designed to scan the dark web for leaked personal data, Google has decided that the tool is no longer needed.
There is not long to go until the tool shut down. In just a month’s time, there will be no more scanning of the dark web for data; one month after this, the dark web report will disappear entirely. Here’s what you need to know.

Proton’s new Data Breach Observatory shines a light into the dark web
Date breaches affecting businesses and online services are ever more frequent and can affect anyone who is unfortunate enough to be a customer or supplier.
Finding out the facts about a breach can be tricky, however, as information is heavily reliant on self-disclosure. Proton is launching its Data Breach Observatory, which delivers a truer picture of the risks by monitoring and reporting cyberattacks and data breaches based on data sourced directly from the dark web.
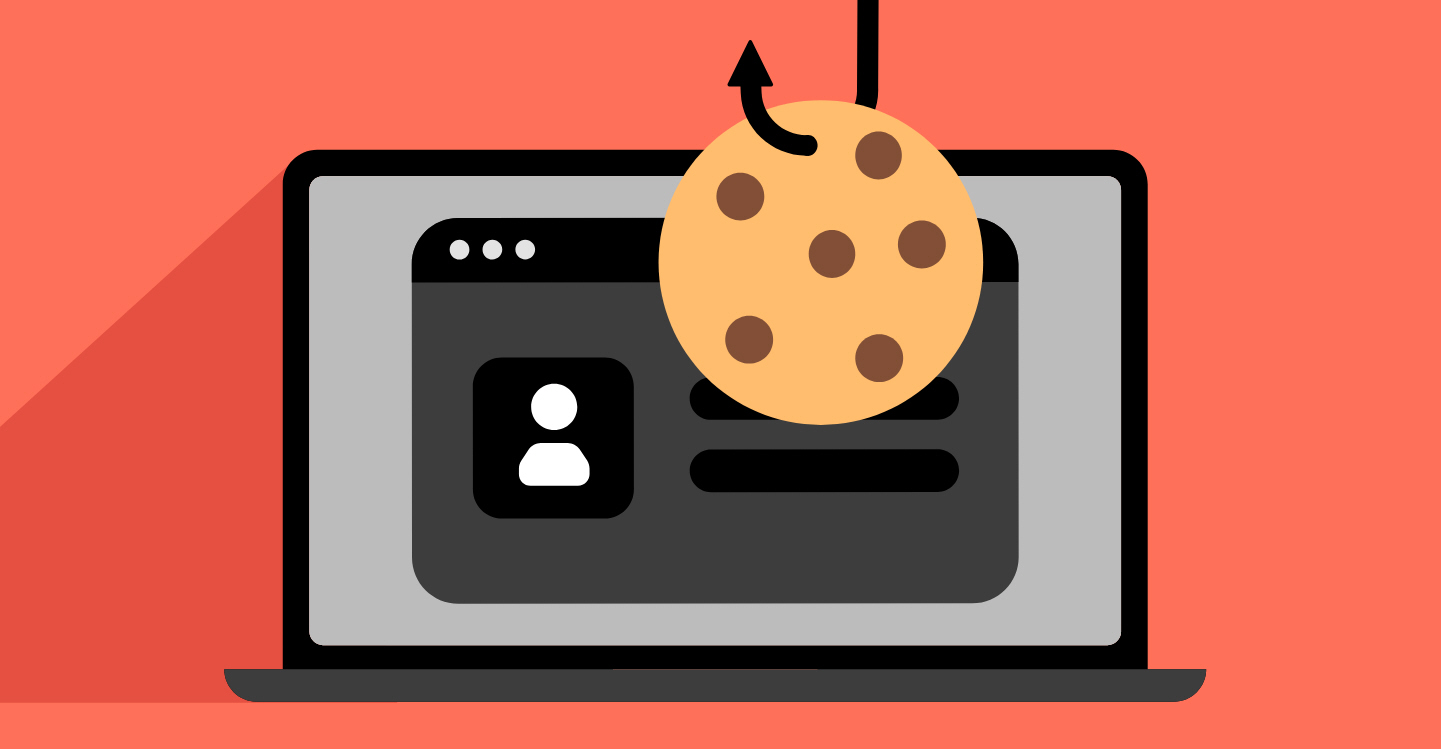
NordVPN adds hijacked session alerts to warn users of stolen cookies on dark web
NordVPN has introduced a hijacked session alert, a new feature designed to protect users from stolen authentication cookies being sold on the dark web.
The new feature forms part of the company’s Threat Protection Pro service and sends immediate notifications when active session data is compromised, giving users the chance to act before criminals are able to exploit their accounts.

UK Online Safety Act leads to rise in searches for fake ID and dark web access
We know that the UK’s Online Safety Act has had a number of consequences including a surge in interest in the use of VPNs. But VPNs aren’t the only things that have seen greater interest.
New research from Comparitech shows more people are searching for fake IDs, how to access the dark web, and torrenting services. The company has recorded a 56 percent increase in impressions for blog posts related to the law and guides to using VPNs as a means of accessing restricted content.

How access to company networks is sold on the dark web for under $1,000
New analysis of illicit dark web marketplaces where cybercriminals buy and sell access to corporate networks uncovers new insights into how initial access to compromised businesses is being sold -- often for less than $1,000 -- and the steps defenders can take to disrupt the process in its earliest stages.
Rapid7’s threat intelligence researchers analyzed hundreds of posts by Initial Access Brokers (IABs) offering access to compromised networks across a range of industries and regions. Their findings show that ‘initial’ access doesn’t necessarily equate to minimal; in many cases, this access represents a deep compromise.

Sudden Dropbox Passwords closure leaves users seeking alternatives
Dropbox has suddenly announced that it plans to discontinue its password manager, Dropbox Passwords. With the discontinuation coming at the end of October, users are left with very little time to find an alternative service.
The company is best known for its cloud storage service, and in announcing the impending shuttering of Dropbox Passwords it says that it wants “to focus on enhancing other features in our core product”. More than just closing down the password management side of things, Dropbox is also bringing dark web monitoring to an end.

Initial access brokers target mid-sized businesses for ransomware
Initial access brokers (IABs) are the invisible engine of modern cybercrime. They don't execute ransomware attacks, but they do enable them.
Research from Check Point External Risk Management (formerly Cyberint) shows that IABs are increasingly targeting smaller businesses, with 60.5 percent of listings targeting SMBs (companies with $5M - $50M revenue), representing a new 'sweet spot' for attackers.
Fraud-as-a-Service allows cybercriminals to launch complex attacks with minimal skills
User-friendly fraud kits that enable amateurs to execute complex attacks against thousands of accounts in minutes are widely available on the dark web according to the latest 2024 Report on Global Identity Fraud from AU10TIX.
FaaS platforms provide all the tools, templates and automation that fraudsters need, including deepfake generators to create synthetic selfies and videos, botnets to automate mass-scale account creation and takeover, and phishing kits for email and web-based scams.

Number of active dark web ransomware groups up 38 percent in 2024
A total of 94 ransomware groups listed victims in 2024 (a 38 percent increase on 2023) with 49 new groups observed, according to a new report, reflecting further complexity in the ransomware landscape.
The study from Searchlight Cyber also finds an 11 percent increase in the number of total victims posted on ransomware leak sites in 2024 (5,728) compared to 2023 (5,081).

Holiday deal hunting mirrored by dark web behavior
Just as shoppers heading online for Black Friday and Cyber Monday deals a new report from Bitdefender uncovers interesting parallels with behavior on dark web marketplaces.
Cybercriminals too, it seems, browse for the best deals on an assortment of unconventional goods and services. In a digital underground that mirrors traditional e-commerce in many ways, these markets cater to buyers with specific -- and often illegal needs.

Dark web activity targets US election
A new report from Fortinet shows a range of activity around the upcoming US election including phishing scams aimed at voters and malicious domain registrations impersonating candidates.
Threat actors are selling affordable phishing kits on the dark net designed to target voters and donors by impersonating the presidential candidates and their campaigns.
Dark web exposure increases risk of attack
The presence of any data relating to an organization on the dark web demonstrably increases its risk of a cyberattack.
This probably won't come as too much of a surprise but it's confirmed by new research from Searchlight Cyber, the dark web intelligence company, and the Marsh McLennan Cyber Risk Intelligence Center.

Cybercriminals get faster at exploiting new vulnerabilities
A new report from Fortinet shows that the second half of 2023 saw attackers increase the speed with which they capitalized on newly publicized vulnerabilities.
Attacks were carried out 43 percent faster than 1H 2023, starting on average 4.76 days after new exploits were publicly disclosed.

Proton Mail launches Dark Web Monitoring to alert users to leaks
One of the most common forms of cyberattack is credential stuffing, using exposed details on different sites to exploit the fact that people frequently reuse passwords.
Proton Mail is introducing a new Dark Web Monitoring feature that will alert customers if their credentials are exposed on the dark web, where stolen emails and credentials get bought and sold.
