
Firefox's address bar has become an ad-stuffed privacy nightmare
Mozilla has just released Firefox 93 and there is a big and controversial change to the address bar. Not content with making helpful suggestions from your browsing history as you type, Firefox Suggest now also includes "relevant suggestions" and "sponsored suggestions" from "trusted partners"; in other words, ads.
There are privacy concerns associated with making these suggestions. Mozilla may insist that it only deal with partners that meet its privacy standards for Firefox, but it still means that whatever is typed into the address bar is sent back to Mozilla and processed in order to deliver ads it hopes you will click on. The good news is that you can disable Firefox Suggest and hide ads in Firefox.

Yubico YubiKey Bio authentication dongle uses biometrics for added security on Windows, Mac, and Linux
Portable hardware authentication dongles are pretty darn cool -- they can be a great way to secure access to various devices, applications, and services using hardware. Google offers its own Titan security keys, for instance, but the search giant likely isn't the first company that comes to mind for these products. Actually, Yubico is probably the name most associated with authentication dongles.
Believe it or not, Yubico's popular YubiKey devices have not yet been offered with biometric support. Thankfully, this changes today. You see, the all-new YubiKey Bio features a fingerprint reader for an added level of security. Not only must you physically have possession of the YubiKey Bio to use it, but you must prove you are its owner by scanning your finger.

Consumers are becoming more active in protecting their privacy
Almost a third of consumers have taken a more active role in protecting their privacy this year, including leaving organizations over their data practices or policies.
The 2021 Consumer Privacy Survey from Cisco has gathered results from 2,600 people across 12 countries and finds consumers are very concerned about the use of their personal data in AI decision-making, and their trust is at stake.

Lithuanian government warns consumers not to buy new Chinese phones and to throw out old ones ASAP
The Defence Ministry of Lithuania has issued a warning that people should stop buying phones from China and should "get rid of those already purchased as fast as reasonably possible".
The extraordinary advice comes after a government report found that handsets produced by Xiaomi and Huawei include a feature to detect and censor certain words and phrases. On the blacklist are terms such as "free Tibet", "long live Taiwan independence" or "democracy movement", and while the censoring functionality was disabled for the European market, there is the potential for it to be remotely activated at any time.

Data privacy and consent in the age of CCPA, GDPR and impending federal privacy law [Q&A]
When it comes to consent and data privacy, the rise of regulations like the General Data Protection Regulation (GDPR), along with increased consumer awareness of data infractions and breaches, has raised the stakes.
When the California Consumer Privacy Act (CCPA) passed in 2018, many states began following California's lead. Currently, more than 30 states have comprehensive privacy bills that are close to passing or in early stages of being drafted.

Assessing the viability of first-party data
In the wake of expanding regulations surrounding the use of consumer data for unprecedented purposes, the digital advertising industry is in for a massive overhaul. Google has announced the removal of third-party cookies and, although they have pushed the date of obsolescence back to 2023, companies are now forced to reckon with a future devoid of third-party data collection. Big Tech is looking to lead the rest of the industry in the development of innovative alternatives.
Unsurprisingly, Google has been at the front of these efforts thus far. The technology giant controls the largest browser, adtech, and search engine products in the industry, a powerful trio that leaves them perfectly positioned to navigate the digital advertising industry through uncharted territory. In addition to removing third-party cookies from their Chrome browser, Google is also fostering the development of responsible adtech in their Privacy Sandbox.

Starting today, Microsoft 365 usage analytics is anonymized by default
As of September 1, 2021, Microsoft is making an important privacy change for Microsoft 365 usage analytics -- pseudonymization of user-level information by default.
Microsoft says that this change will help companies to more easily comply with local privacy laws, but it is something that is likely to be welcomed for various other reasons.

Value of personal data increases 1,800 percent in 20 years
If you use the internet it's almost impossible to avoid exposing at least some of your personal information to the sites you use. What you may not be aware of is just how valuable this personal data is to businesses.
New research from marketing specialist MIQ Digital shows that in 2001 an average user generated around $1.97 (£1.45) worth of Google Ads revenue, in 2021 this is up to $35.40 (£26), an 1,800 percent increase.
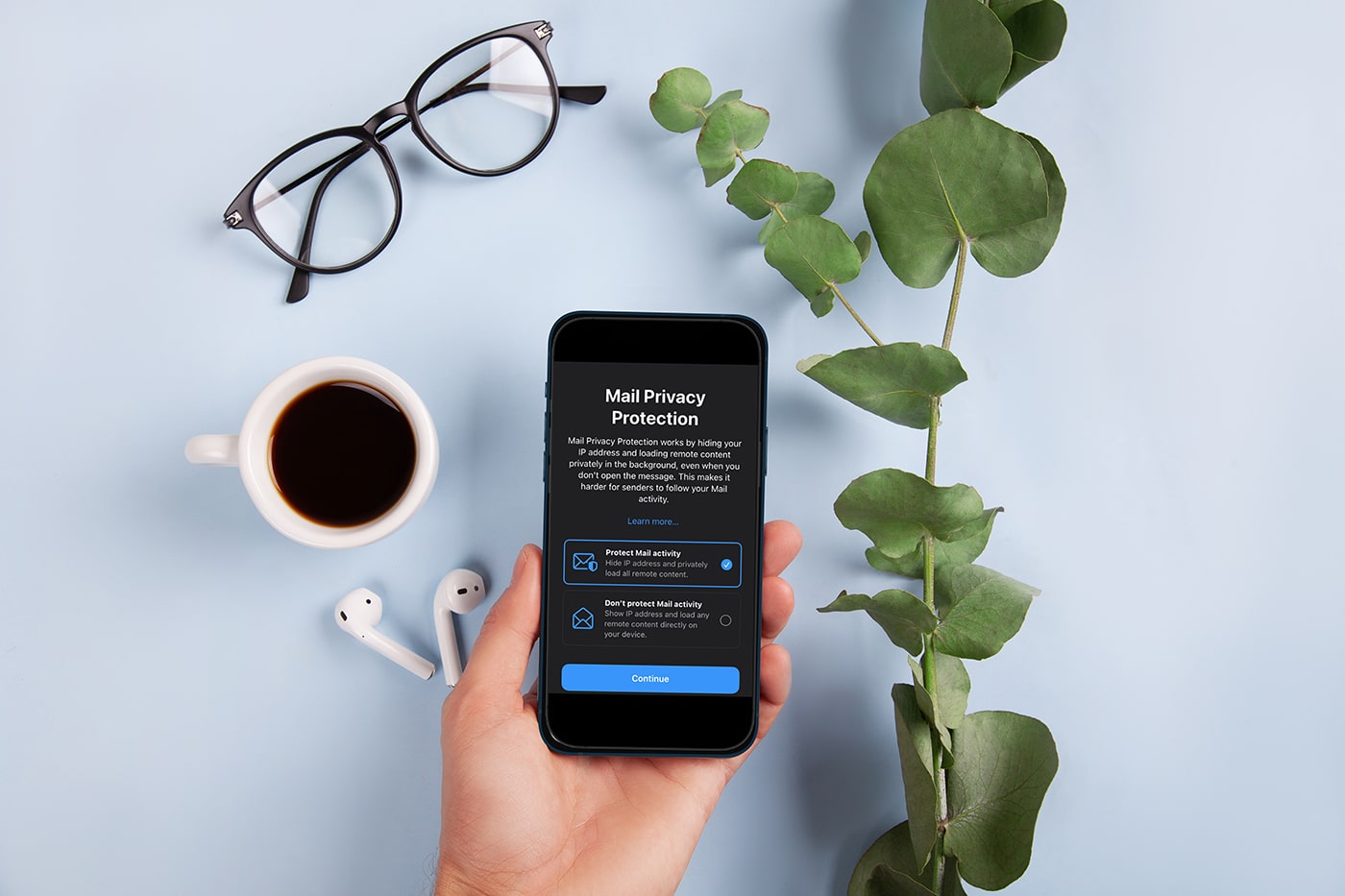
How long until others copy Apple's Mail Privacy Protection?
When iOS 15 is released this fall, users will have access to enhanced Siri capabilities, new ways to personalize their device, helpful improvements to the Find My iPhone/iPad, and several other new features and functionality to play with. But in the worlds of digital privacy and marketing technology, there's one update in particular that has been sending shockwaves up and down the industry.
Companies who care about email marketing have been in a sort of panic mode ever since the full slate of iOS 15 updates was revealed a couple months ago, due to a new feature called Mail Privacy Protection. In what Apple is calling an advancement of its "privacy leadership," the ability to block marketers from tracking the open behavior of their emails is the first step in what could be a cataclysmic shift for the entire spam (I mean, "email marketing") industry.
Thousands sign letter asking Apple to scrap plans to scan users' photos for child abuse images
An open letter signed by privacy advocates, security experts, technology companies and legal specialists has been sent to Apple, decrying the company's plans to scan the photos of Mac, iPad and iPhone users for evidence of child abuse.
While on the face of it, Apple's "Expanded Protections for Children" plans are a good thing, it has also come in for heavy criticism. With the release of macOS Monterey, iOS 15 and iPad OS 15, the company is implementing CSAM (Child Sexual Abuse Material) detection which will check image hashes to see if they feature in databases of known abuse images. It has been likened to creating a backdoor to users' files and has horrified privacy experts.

Google unveils new Nest smart home stuff
Google bought Nest more than seven years ago now, and since that acquisition, there have been many cool smart home devices to come from the search giant. Under the Nest branding, there's not just smart thermostats and cameras, but other products too such as doorbells and speakers. Ultimately, the name "Nest" has become synonymous with the smart home.
Today, Google unveils some new Nest smart home devices, and they are all camera-related. There is a new doorbell (with integrated camera) plus three new dedicated security cameras. What's notable is that the new doorbell and one of the new cameras can be run from a battery, meaning they do not require a hardwire power connection. One of the cameras features nifty floodlights too.
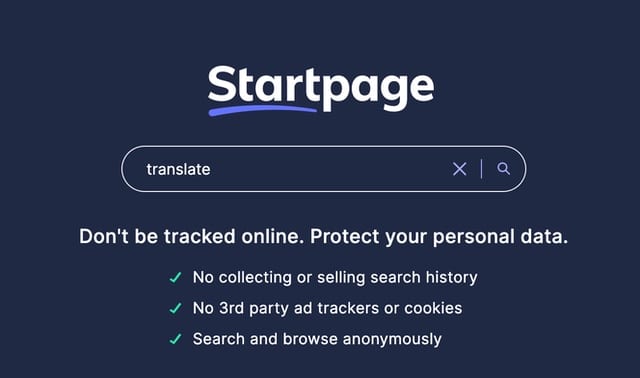
Startpage launches its privacy-centric Google Translate alternative, Private Language Translator
As a search engine for people looking to avoid Google -- or for anyone with privacy concerns in general -- Startpage has earned itself a strong following and a solid reputation. Building on the popularity of its private search tool, the company is continuing the expansion of its privacy-focused services.
Having already launched Private Shopping, Private Currency Converter and Private Stocks this year, Startpage has now added Private Language Translator to its rostrum.

Audacity says it is 'deeply sorry' for privacy policy fiasco, publishes lengthy update and explanation
The development team behind Audacity learned the hard way that people do not take kindly to the introduction of telemetry, particularly when communication is poor.
Over the last few months, there has been a very public debacle involving Audacity's proposed changes to its privacy policy. It resulted in the software being branded "possible spyware" and led to explanations, apologies and backtracking. Now the team behind the open source audio editor has published its updated privacy policy along with a lengthy explanation about various elements of it and an apology for the "significant lapse in communication".

DuckDuckGo launches privacy-focused @duck.com email forwarding
DuckDuckGo is a pretty cool company that focuses heavily on privacy. Its claim to fame is its search engine that aims to compete with the likes of Google and Bing, but without tracking you. Believe it or not, its search results are pretty good comparatively, although Google still edges it out.
Over time, DuckDuckGo has launched its own web browser and browser extensions, constantly trying to keep humans safe from the eyes of "Big Tech." And now the company announces its latest creation -- @duck.com email accounts.

Investigation uncovers global abuse of Pegasus malware to spy on journalists, activists and more
Spyware produce by the Israeli surveillance firm NSO Group has been abused by governments to target dissenting journalists, activists, lawyers and more, an investigation by human rights groups and media organizations has found.
The Pegasus spyware was produced with the intention of targeting terrorists and other criminals, but an investigation into a huge data leak shows that it has also be misused by authoritarian governments to gather text message, photos, call logs and more from iPhones and Android handsets. The malware can also be used to acti8vate the microphone of a targeted device to eavesdrop on conversations. Targets includes not only journalists and activists, but also key business figures, members of government, presidents and prime ministers.
