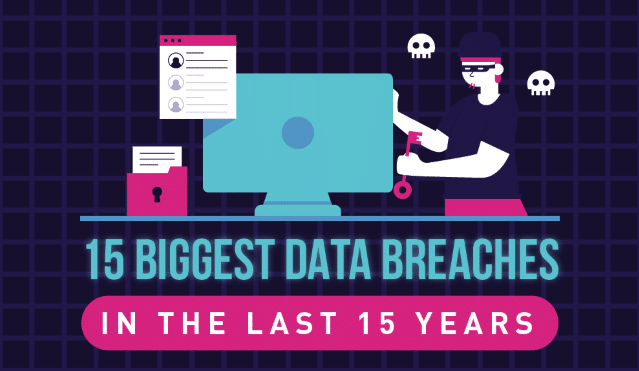
The biggest data breaches of the last 15 years
We've become pretty well accustomed to large scale data breaches over recent years. But that doesn’t mean that the numbers involved aren't still significant.
Web hosting comparison site HostingTribunal has put together an infographic looking at the 15 biggest breaches of the last 15 years.

Microsoft advises Azure customers to update Exim to avoid a Linux worm
Microsoft has issued a warning to Azure customers using Linux Exim email servers running Exim version 4.87 to 4.91.
The company explains that these versions of Exim are vulnerable to a critical Remote Code Execution (RCE) security flaw and need to be updated to prevent the spread of a worm.

3 attacks you'd miss without AI
There has been a lot of hype around AI to the point where some people are simply tuning it out. I think this is a mistake. While there are limits to what AI can do, there also are sophisticated attacks that we’d miss without it.
The need for AI is driven by three fundamental yet significant changes in the enterprise computing environment.

Humans are still the weakest link in information security
According to a new report, more than half of all C-suite executives (53 percent) and 28 percent of small business owners who suffered a data breach say that human error or accidental loss by an external vendor/source was the cause.
The annual data protection report from information security service Shred-It also finds 21 percent of executives and 28 percent of small business owners admit deliberate theft or sabotage by an employee/insider was the cause of the data breach.

Hacker hits Symantec and accesses passwords
Security firm Symantec was attacked by a hacker back in February, but the company did not reveal details of the incident.
The attack has been brought to light by Guardian Australia which has seen some of the data extracted by hackers. This comprises not only passwords, but what is thought to be a list of Symantec clients -- including government agencies. But Symantec is downplaying the data breach, dismissing it as a "minor incident".

Organizations urged to patch for BlueKeep as latest malware charts are revealed
Check Point Research, has released its Global Threat Index for May 2019 and is warning organizations to check and patch for the BlueKeep Microsoft RDP flaw in Windows 7 and Windows Server 2008 machines, to prevent the risk of it being exploited for ransomware and cryptomining attacks.
BlueKeep affects nearly a million machines accessible to the public internet and many more within organizations' networks. The vulnerability is critical because it requires no user interaction in order to be exploited. RDP is already an established, popular attack vector which has been used to install ransomware.

Security startup aims to provide better visibility into the cloud
As businesses move more of their systems to the cloud to drive digital transformation and gain a competitive edge, IT security teams can struggle to retain the ability to secure data and manage risk.
Israeli startup Orca Security is announcing its Cloud Visibility Platform which uses patent-pending SideScanning technology to deliver comprehensive visibility into the security posture of an organization's cloud footprint in a matter of minutes.

Rowhammer-based RAMBleed exploit lets hackers steal data from memory
Security researchers have revealed an exploit that can be used by hackers to steal data from DRAM, even if ECC protection is in place. RAMBleed is a Rowhammer-based attack that can also be used to alter data and increase privilege levels.
Taking advantage of the design of modern memory chips, a Rowhamer attack works by "hammering" the physical rows of data in quick succession causing bit-flipping in neighboring rows. RAMBleed takes this in a different direction, using a similar technique to access data stored in physical memory.

LastPass Business brings single sign-on to over 1200 apps
Hundreds of cloud applications are being used in businesses and IT teams are pressured to achieve high levels of security without introducing complex authentication processes that may reduce workforce productivity.
LogMeIn, developer of the LastPass password management program is launching a new suite of LastPass Business solutions delivering a comprehensive identity offering, built for small and medium sized businesses.

New enterprise platform secures digital assets in transit
Last month $40 million worth of Bitcoin was stolen in the Binance hack and it's estimated that more than $3 billion has been stolen over the last 18 months due to key theft and stolen credentials.
In order to guard against this type of theft, new company Fireblocks is launching an enterprise platform to protect crypto currency and other digital assets in transit.

Over three billion fake emails sent out daily
At least 3.4 billion fake emails are sent around the world every day, according to a new report from email verification company Valimail, with the majority of suspicious emails coming from US-based sources.
The report shows that email impersonation -- accounting for 1.2 percent of all email sent in the first quarter of 2019 -- is a phishing attacker's primary weapon to gain access into an organization's network, systems, intellectual property and other sensitive assets.
VLC 3.0.7 includes more security fixes than ever thanks to the European Commission
Version 3.0.7 of VLC has been released, and while it may seem like a minor x.x.x update, it includes more security fixes than any other previous release -- including two high security issues.
Jean-Baptiste Kemp, the president of VLC-maker VideoLAN, says the number of fixes included in this version is due to the EU-FOSSA bug bounty program, funded by the European Commission.

US Customs and Border Protection says photos of thousands of travelers were stolen in a data breach
Hackers have stolen the photographs of travellers entering and leaving the US, as well as photos of their license plates, US Customs and Border Protection (CBP) has said.
The cyberattack was carried out on the network of a federal subcontractor, and the images were taken as part of a "malicious cyberattack". Although the hack attack has only just been revealed publicly, CBP first learned of it on May 31.

Microsoft takes down huge MS-Celeb-1M facial recognition database
Microsoft has deleted a database containing around 10 million photographs that was being used to train facial recognition systems.
Known as MS-Celeb-1M, the database was created in 2016, and originally contained photos of celebrities. Over time, however, images of writers, journalists and others crept in, and ultimately 100,000 individuals were to be found in it. Microsoft has not made much noise about the deleted content, but has said that the database was wiped as the person maintaining it was no longer a company employee.

Want someone's personal data? Give them a free donut
While you might expect Homer Simpson to hand over personal details in exchange for a donut, you wouldn't expect cybersecurity professionals to do the same.
However, technology services provider Probrand has carried out a study at a cyber expo attended by UK security professionals, where attendees voluntarily shared sensitive data including their name, date of birth and favourite football team -- all to get their hands on a free donut.
