The biggest data security risk? Downloading data to a spreadsheet
These days, it seems like every time you turn around another company announces a data breach. At the same time, organizations spend millions on their data warehouses, security solutions, and compliance initiatives. But all of that spend can instantly be rendered useless by the everyday business workflow of downloading data to a Microsoft Excel spreadsheet.
Of course, business experts aren’t looking to circumvent enterprise governance practices. They’re just trying to get the answers they need to make better business decisions. And because they lack the SQL programming expertise or extensive training required to work with data directly in most business intelligence (BI) tools, they are often powerless to answer the questions raised in the last meeting or email. So they turn to what they know best: the spreadsheet.

How to secure Windows 10 -- Microsoft reveals SECCON framework to protect systems
Based on the DEFCON levels, Microsoft has unveiled the SECCON framework -- a series of guides for securing a range of Windows 10 configurations in different environments.
Starting with an "Administrator workstation" at level 1 and building up to "Enterprise security" at level 5, the framework is Microsoft's attempt to simplify and standardize security. While it is not a one-size-fits-all solution, the company says it is "defining discrete prescriptive Windows 10 security configurations to meet many of the common device scenarios we see today in the enterprise".

Gmail now supports the MTA-STS and TLS Reporting security standards
In a first for a major email service, Google has announced that Gmail now supports the MTA-STS and TLS Reporting security standards.
The two standards help to avoid man-in-the-middle attacks, using encryption and authentication to add new layers of security. Google says that Gmail's MTA-STS adherence is now in beta, and the company hopes that by supporting the standard other providers with follow suit.

Security professionals think cybersecurity is a bigger threat to the US than border security
A new survey of security professionals taken at this year's RSA reveals that 92 percent of respondents feel that cybersecurity is a bigger threat to the US than border security. Yet government, and media, attention seems far more focused on the latter.
The study from AI-powered security company Lastline also asked respondents which of the tech giants they trust the least with their data, not surprisingly 76 percent name Facebook. Others, Amazon (25 percent), Apple (24 percent), Google (20 percent) and Microsoft (27 percent) all scored relatively evenly when asked who they trust most.
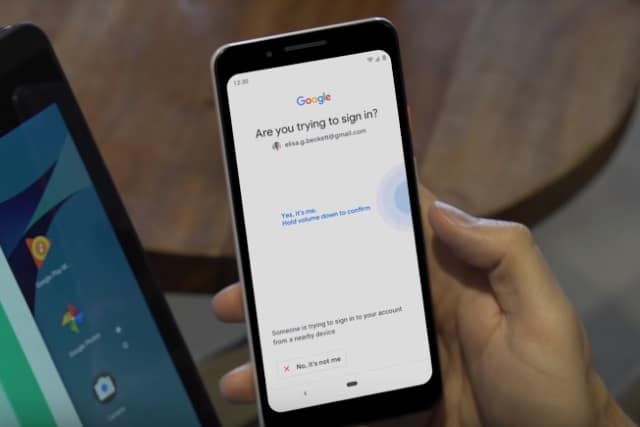
Google now lets you use your Android phone as a 2SV security key
If you have a phone running Android 7.0 Nougat or higher, you can now use it as a FIDO security key. This new option was announced at Google Cloud Next 2019, and it makes using 2-Step Verification much more accessible thanks to the fact that people are likely to have their phones with them most of the time.
The system -- currently in beta -- can be used to access ChromeOS, macOS or Windows 10 computers running Chrome, and can replace or supplement other FIDO-based security keys like Google's own Titan Security Key.

Businesses complacent about mainframe security
Although 85 percent of companies say mainframe security is a top priority, just 33 percent always or often make mainframe decisions based on security finds a new report.
The study from mainframe vulnerability specialist Key Resources Inc, based on research by Forrester Consulting also finds 67 percent of respondents admit that only sometimes or rarely are they factoring security into mainframe decisions.

A quarter of phishing emails bypass Office 365 security
According to a new study analyzing more than 55 million emails, 25 percent of phishing emails bypass Office 365 security, using malicious links and attachments as the main vectors.
Other findings of the report from cloud-native security firm Avanan include that 33 percent of emails contain a link to a site hosted on WordPress and 98 percent of emails containing a crypto wallet address are phishing attacks.

Securing serverless computing, the latest cloud paradigm [Q&A]
The cloud-skills shortage has made security a major challenge for enterprises. In fact, virtually every data breach in the cloud today is due to human error, rather than brilliant hacking. Hackers don't even bother launching attacks in the public cloud; they simply look for misconfigured systems that leave data exposed.
Against this backdrop, a whole new cloud model is taking hold -- serverless computing. In a world where cloud certifications and security skills are already in short supply and causing chaos in the cloud, what will serverless computing do to compound that problem for enterprises? Is it possible for organizations to avoid making the same mistakes with this new paradigm that they are making in traditional cloud environments?

Beta and nightly builds of Firefox now protect against fingerprinting and cryptomining
Mozilla has added new protective features to the nightly and beta versions of Firefox. Through a partnership with Disconnect, the browser is now able to block cryptocurrency mining and fingerprinting scripts.
The new features mean that users are protected against scripts that can be used to track them online, as well as those that use CPU cycles to mine for cryptocurrency. Mozilla says it is part of its mission to protect people from "threats and annoyances on the web".
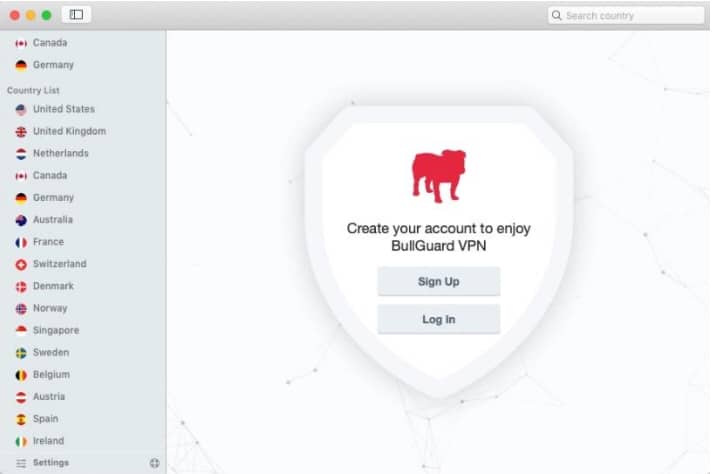
BullGuard adds to its product line with a VPN
Cybersecurity company BullGuard is launching its own VPN for Windows, Mac, Android and iOS, intended to make it simple for users to ensure their online privacy.
Designed to be easily used across multiple devices, BullGuard VPN features a simplified user interface and quick connect functionality, enabling consumers to fly under the radar and surf the internet in stealth mode while retaining complete anonymity via military-grade encryption.

Understanding the LockerGoga ransomware attacks
Last month Aluminum manufacturer Norsk Hydro was hit by a large scale ransomware attack that affected its systems across the globe and caused severe disruption to its operations with an estimated impact of more than $35 million..
The attack used the LockerGoga ransomware and the threat research team at Securonix has been monitoring the malware, which also caused problems for a number of other companies.

Credential stuffing attacks target media streaming services
The entertainment industry and in particular streaming services is among the biggest targets of credential stuffing attacks according to a new report.
The study from digital delivery platform Akamai, unveiled at the NAB Cybersecurity and Content Protection Summit in Las Vegas this week, focuses on credential abuse attacks against online video and music streaming services.

Huawei's 'shoddy' security could mean it is banned from sensitive parts of the UK's 5G network
Concerns about Huawei's "very, very shoddy" security could mean that the Chinese company's technology is barred from key parts of the UK's 5G mobile network.
A UK watchdog has already said that Huawei poses a national security risk, but a statement from the technical director of GCHQ's National Cyber Security Centre has stepped things up. Dr Ian Levy says that "the security in Huawei is like nothing else -- it's engineering like it's back in the year 2000 -- it's very, very shoddy".

Emsisoft Decrypter for Planetary gets your ransomware-riddled files back for free
Emsisoft has released a free decrypter tool for anyone who has been struck by the Planetary Ransomware, eliminating the need to pay a fee to the attackers.
Before using the tool you are advised to ensure that you have removed the malware from your computer -- something you can do with the free version of Emsisoft Anti-Malware. You also need to ensure that you don't delete the ransom note ("!!!READ_IT!!!.txt") or the decrypter won't work.

90 percent of critical infrastructure hit by cyberattacks
A new survey of professionals in industries using industrial control systems (ICS) and operational technology (OT) finds 90 percent of respondents say their environment has been damaged by at least one cyberattack over the past two years, with 62 percent experiencing two or more attacks.
The study commissioned by Tenable from the Ponemon Institute also finds 80 percent of respondents cite lack of visibility into the attack surface, knowing what systems are part of their IT environments, as the number one issue in their inability to prevent business-impacting cyberattacks.
