Apple apologizes for privacy-invading FaceTime bug, promises delayed software update
Apple has issued an apology for the recently-discovered bug that made it possible to eavesdrop on people via FaceTime.
The company had promised that a software update would be delivered later this week, but the interim solution was to simply disable the group FaceTime feature server-side. Apple now says that the problem has been fully fixed, but a software update that re-enables the group function will not be issued until next week.

Are 'pop-up' SOCs the answer to protect major events? [Q&A]
Increasingly high profile one-off events like sports tournaments and elections are becoming the target of hackers.
Protecting these is tough because even if the hosts have a sound security infrastructure for day-to-day operations, they often don't have the resources necessary to lock down a large scale, high-profile event which requires additional physical and cybersecurity to protect against disruption, revenue loss or other irreversible damage.

Over 90 percent of organizations hit by targeted email attacks
Over the past year, business email compromise (BEC) scams have jumped by 60 percent. In addition more than 90 percent of organizations report being hit by targeted email attacks, with 23 percent suffering financial damage as a result.
These findings come from the Q1 2019 Email Fraud and Identity Deception Trends report by secure email specialist Agari.

CISOs must change their outlook or lose their jobs
Chief information security officers (CISOs) are now involved in 90 percent of significant business decisions, but just 25 percent of business executives see CISOs as proactively enabling digital transformation -- which is a key goal for 89 percent of organizations.
These are among the findings of a new study by IDC sponsored by Capgemini but which also shows 15 percent still believe information security is a blocker of innovation.

The elements of cybersecurity hygiene and secure networks - Part 3
While it’s essential that employees consistently avoid taking risks that could lead to a data breach, even top-performing employees don’t necessarily have top-notch cybersecurity knowledge. Thus, organizations are in charge of bridging the cybersecurity skill gap to keep employees from damaging the company’s network by accidentally uploading of a malicious program or sharing confidential documents with the wrong people.
Though it’s easy for IT and leadership teams to put systems in place that defend their network from external threats, well-intentioned internal users can be a hackers easy way in. The only way for organizations to counter this is with education and training.

Symantec boosts its endpoint security offering
Sophisticated attackers are increasingly taking advantage of the complexity of endpoint environments to exploit gaps and discover new paths to lucrative targets.
Symantec is announcing enhancements to its endpoint security portfolio designed to defend against the most sophisticated cyberattacks as well as improving application discovery and risk assessment.

Rush to digital transformation puts security of data at risk
Digital transformation projects are underway in the vast majority of businesses, according to a new report, but 'aggressive' transformers are most at risk from data breaches.
The latest Data Threat Report from Thales eSecurity shows digital transformation in some form is happening in 97 percent of organizations. 86 percent say they feel vulnerable to threats, yet less than a third of respondents (only 30 percent) are using encryption within these environments.
How to disable FaceTime and protect your privacy
By now you have probably heard about the bug that's been discovered in Apple's FaceTime. In short it is an exploit that lets you connect a call you have placed rather than waiting for the recipient to pick up -- so you can then listen to audio and watch video.
Apple is working on a fix, and it you want to be sure that you don't fall victim to eavesdropping, you should think about disabling FaceTime on your iOS device. Here's how to do just that.
Massive FaceTime privacy bug lets people eavesdrop on audio and video calls before they've been answered -- and Apple doesn't have a fix yet
Apple is scrambling to fix a serious bug that has been discovered in its FaceTime messaging services. The bug makes it possible to spy on the people being called, even if the call is not picked up.
This is a serious privacy issue, as it gives someone the ability to secretly eavesdrop on someone -- or even watch them -- without their knowledge. At the moment, Apple does not have a fix but the company says it is working on the problem and will address it by the end of the week. In the meantime, you may want to consider disabling FaceTime on your iOS device.

69 percent of employees share passwords with colleagues
According to a new study, 69 percent of respondents admit to sharing passwords with others in the workplace, and 51 percent reuse an average of five passwords across their business and personal accounts.
The study by authentication key vendor Yubico and Ponemon, released to coincide with Data Protection Day, also finds two-factor authentication isn't widely used, 55 percent don't use it at work and 67 percent don't use it for their personal accounts.

Leak shows that Android Q will bring native face unlock to more phones
A new Android Q leak suggests that Google is ready to copy another of the features iOS users have come to know and love: facial unlock.
There are already a number of Android handsets -- including recent phones from OnePlus -- which have their own implementation of the biometric security feature, but with Android Q, it is looking as though the feature will be hard-baked into the operating system.

Automated attacks target cloud infrastructure
Enterprises continue to grow their cloud usage, but this inevitably presents challenges when it comes to keeping systems secure.
New research from Securonix Threat Research highlights an increase in automated attacks targeting cloud infrastructures.

Feel overlooked and underappreciated? You must work in IT security
Most IT security professionals in the UK feel they’re suffering from an image problem among fellow workers, according to new research commissioned by privileged access management specialist Thycotic.
Almost two thirds of respondents (63 percent) feel that their security teams are either viewed as the company naysayers -- specifically either 'doom mongers' or a 'necessary evil' (36 percent).

New solution protects enterprises against ransomware
Ransomware attacks are increasingly well targeted and complex, and they can prove devastating for businesses.
Storage specialist Cohesity is launching a new set of anti-ransomware capabilities for its DataPlatform that can directly combat attacks.
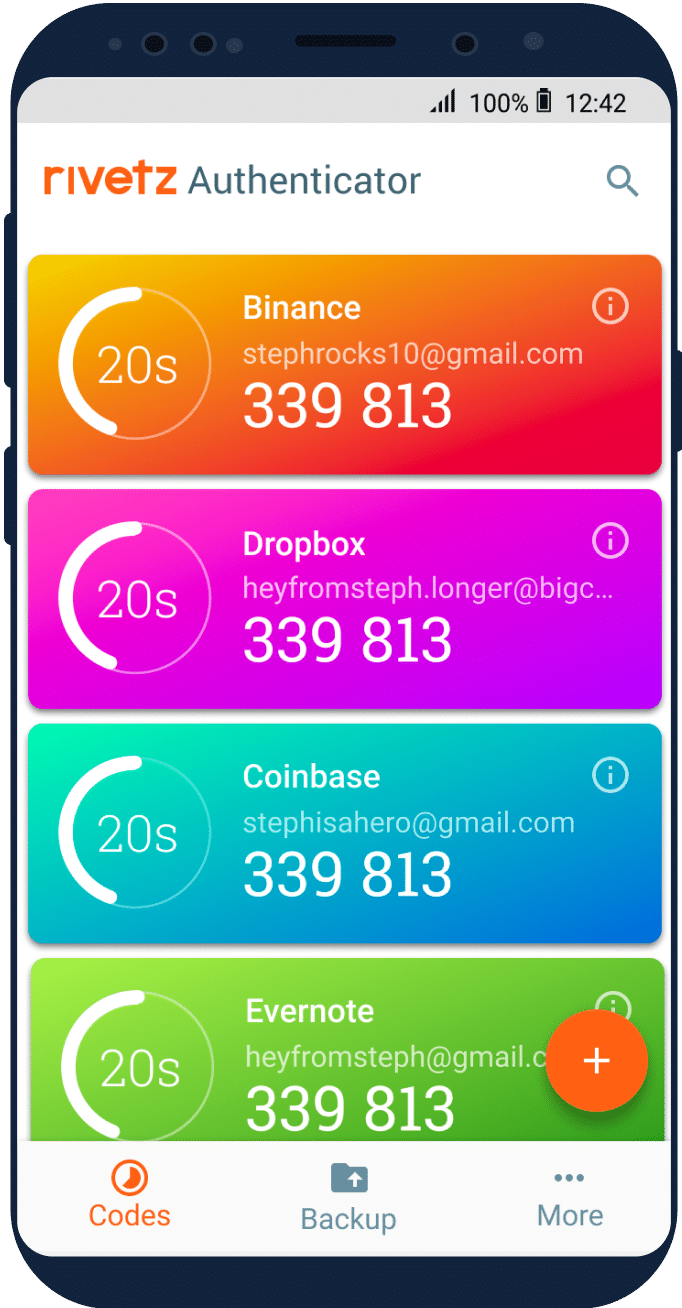
New Android app allows simple two-factor authentication across all apps and accounts
We're all being encouraged to use two-factor authentication to make our online accounts more secure.
But 2FA can be a major pain when you update to a new device and have to re-authenticate everything. Even when users save their private 2FA keys to migrate onto new devices, it can still take time to manually reset 2FA for each account.
