Forced to use Windows XP past April? 10 ways to make the best of a bad situation
 I've been pressing my day to day clients, as well as informed readers here on BetaNews, on the case for ditching Windows XP altogether. I'm guessing by now that chances are, if you're still running XP at this point, you're probably going to stick it out on the platform for the indefinite short term. I've already written about the best ways to safely migrate off XP without losing functionality in the workplace, but if you absolutely have no choice but to keep riding the sinking ship for now, here's hoping at least you are going to be smart about how you do so.
I've been pressing my day to day clients, as well as informed readers here on BetaNews, on the case for ditching Windows XP altogether. I'm guessing by now that chances are, if you're still running XP at this point, you're probably going to stick it out on the platform for the indefinite short term. I've already written about the best ways to safely migrate off XP without losing functionality in the workplace, but if you absolutely have no choice but to keep riding the sinking ship for now, here's hoping at least you are going to be smart about how you do so.
No, your PC is not going to explode, implode, or just stop working come the April cutoff date Microsoft has set. In fact, your system is probably going to continue humming away as usual. But it's what you can't see that will hurt you the most, and that's what XP holdouts are forgetting: the bad guys are arming themselves to the teeth with exploits, just waiting for April 8 to come and go.
And it makes perfect sense. If your enemy (Microsoft) has clearly told you they are leaving legions of XP users at bay once April passes, then unleashing the big guns once the safety net comes down is a pretty smart battle tactic, as much as I despise the bad guys.
I can only preach to the choir so much. April is looming and those XP users left out there are wondering what they can possibly do to mitigate their risks as much as possible. The best course of action without a doubt is moving to Windows 8.1 or Windows 7, but if you can't or won't make such a bold move, then here's the best of what's left on your plate of options.
#1: Ditch the Free AV - Get a Paid Solution
We've been able to move over 90 percent of our client base off XP at this point. Pretty impressive, but we still have our holdouts. For all these lone rangers, we have been very strict about ensuring that they are not relying on any of the free AV products (Avast, AVG, Security Essentials, etc) out there. These programs provide a false sense of security, and for a situation where a "wild west" of exploits is just about certain to erupt soon, it's silly to place all your eggs into the basket of a free AV product.
It's not that I have something against free antivirus. In fact, I used to recommend them back in the day when they actually did a good job. But I don't see this as being the case anymore. As I tell clients, the bad guys are too good -- and the free products just can't keep up. Aside from a few instances here or there, free products rarely breach the top 5 list of any of the major independent testing bodies, namely Virus Bulletin and AV-Comparatives.
Asking an IT pro what antivirus he/she prefers is like asking what car they drive, to some extent, as every opinion carries different experiential and expert insight. But I will say that my company usually relies on ESET's NOD32 for residential customers, and ESET's Endpoint Antivirus for our commercial/nonprofit customers.
And no, we don't push the "Macs don't get viruses" mantra either; our Mac clients are usually informed about installing ESET Cyber Security. We have seen Macs come into our office with infections and think it's going to become ever more problematic as attackers seek out Apple users as juicer targets. Other writers like Tim Worstall at Forbes are toting the same line these days.
While we don't keep scientific records on infection rates between free AV users and paid users, on the average, the number of malware breaches we see on ESET-protected machines are far and beyond less than anything we get on the other side.
And I will probably go as far to say that you should probably double up your defenses if you do a lot of internet activity on an XP machine and plan on doing so past April 8. We have been recommending MalwareBytes as a failsafe to work in unison with ESET, for high risk users. Such a tag team security effort should give you a great leg up over the bad guys, even though you will still be a high risk target for their exploits.
If you truly believe in using a free AV product like MS Security Essentials past April 8, I'm not going to lie: you're on your own, my friend.
#2: Get a Firewall That Supports Multiple Subnets & VLANs
If you don't already use a good security router/firewall with your XP system(s), then there is no better time to do so. A great unit from Cisco that we have been having success with, and not breaking the piggybank, is the RV320 Small Business unit they offer. You can snag one on Newegg or another reputable online vendor for $180USD or less these days. Yes, it's more expensive than buying a home level Linksys or Netgear, but it will provide you with leagues better security. And if you have an office that is still relying on XP, I shouldn't need any more reason to recommend this if you care about your business.
Units like the RV320 allow you to use a combination of differentiated subnets as well as VLANs to separate out your traffic to your internet connection. This means that you could have your XP system(s) on a 192.168.2.x address and VLAN 5 while the rest of your network can work on a 192.168.1.x and VLAN 1 without having any connection to the XP machines. This creates a safe and secure "quarantine zone" that can keep traffic segregated in the event that a malware breakout occurs on an XP machine. This is what we are implementing for some clients who are not going to make the XP cutoff deadline next month.
While I don't think this is a great long term solution, it will definitely help mitigate your cross-infection potential until you can get off XP for good.
#3: Virtually Freeze your XP PC with DeepFreeze
While we have not used this as much with our own customers, a nifty product my former school district employer had at its disposal was something called DeepFreeze by Faronics. The tool is aimed at organizations with PC fleets that are prone to getting "screwed around" with by end users, like students for example. The advent of introducing Group Policy with a big Windows 7 transition we did years ago helped mitigate most of the risk caused by XP, so we stopped using DeepFreeze, but for home users or small offices, this is a great way to thwart the risk of infection.
In fact, I admit: I use this software on my mom's home laptop. She still runs ESET NOD32, but this allows me to pretty much "set it and forget it" when it comes to her system. DeepFreeze is a product that does just like its name says: it freezes your system state in the same condition as set prior to a final reboot you make before "freezing" the machine. Thawed state allows you to make changes and delete files on your frozen disk volume; frozen mode allows you to restart the machine and rid viruses, malware, or other induced changes to be wiped away after the reboot. Pretty cool.
Now, yes, this does introduce its own sense of potential false security if you are using it without an AV product. If you have one frozen XP machine with DeepFreeze, while that machine may be well protected by your AV/DF combo, other systems on your network may be at risk if they aren't segregated using a firewall like I recommended above. This is because DeepFreeze is meant to extinguish any malware upon reboot on the protected host only; it is NOT a first line of defence at stopping the spread of initial infection to non-frozen machines.
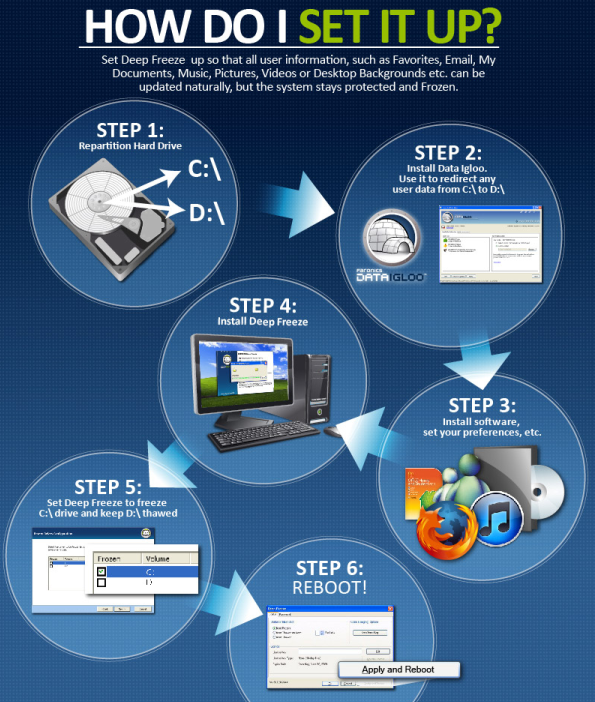
DeepFreeze is a great way to provide a safety net for any exploits that make it past your AV program (we love ESET NOD32). It virtually "freezes" the contents of your Windows drive, or any other chosen drive, and any changes due to malware can be wiped away with a simple restart. Very powerful, yet super simple to use. (Image Source: Faronics)
If you have kids in the home using XP machines past April for browsing or gaming, DeepFreeze is a great way to configure these systems with the latest patches and AV, and then freeze them in their current state. A reboot is all that is needed to wipe away the harmful effects of malware or sneaky fingers making changes we don't want.
DeepFreeze Standard is the edition we purchase for home or small office users, and it costs $45USD per PC (one time purchase). Dirt cheap for the peace of mind it provides. You can check out the full infographic for how DeepFreeze works on the Faronics website.
#4: Make Sure All Latest Windows Updates Are Installed
Not much more to say about this point, but people still do forget to do their Windows Updates on XP machines. The automatic update functionality in Windows XP stinks bad, and I never use it. The real way IT pros like myself check for updates on XP machines is to use the actual Windows Update site (sometimes labeled Microsoft Update if you opt for all the optional checking of other MS products) which re-scans your entire PC for missing Windows XP patches, as well as items from Office, SQL Server, and other products from Redmond.
Microsoft is releasing its last batch of patches through April 8, so checking for any new releases through that date will be the best way to ensure you have the best baseline of security possible on an XP machine. While the situation is bound to degrade as time goes on and hackers let loose their new exploits, getting all of the remaining patches possible for XP is a wise thing to do.
#5: Use Secunia PSI to Inspect your Third Party App Footprint
We put a lot of heat on Windows XP and its aging codebase for exploits aimed at the users relying on such systems, but we tend to overlook the other dangerous side of the equation: third party apps. Items like Flash Player, JAVA, and Adobe Reader are in just as much troubled water with older editions as Windows XP is these days, so leaving an otherwise secure XP machine with legacy versions of these products is like turning half a blind eye to your overall security situation.
Secunia PSI is a completely free tool you can use that can scan over all third party software on your machine, show you just how out of date any old versions are, and provide you with a streamlined upgrade path for the apps. I like using this tool in combination with our favorite app installation site, Ninite.com, to quickly round up and install updates in a minimal number of clicks. Let Secunia do the spotting for you, and then just click-click-click the products you need updated on Ninite for an easy way to get updated.
Mind you, Ninite was forced to remove Flash Player for Windows links a few months back, so you will be forced to download that from the Adobe site directly. This only applies to Windows 7 and below users that are either on IE or relying on FireFox. Chrome has had built in flash for some time now. Another reason to just use Chrome! Which brings me to my next point...
#6: Ditch Internet Explorer; Move to Chrome or Firefox
The last version of Internet Explorer that is allowed on Windows XP is IE8. That's an antique in computing time, plus it's a very dangerous browser since it effectively loses all support the same day Windows XP does. Microsoft isn't releasing IE10 or IE11 for Windows XP since it wants to overtly nudge all you holdouts over to Windows 7 and Windows 8.1, which I agree with. But for those who refuse to move, Google Chrome or Firefox are your best bets at staying relatively safe online.
Google Chrome is probably the best pick since it has the most aggressive update cycle with new releases almost every week or two. Plus, the fact that Google bundles the latest Adobe Flash Player into the browser, plus its own internal PDF viewer, reduces your need for third party apps. Very important in a post-April XP world. What's the easiest way to get Chrome? Just head over to Ninite, checkbox Chrome, and let the installer handle the rest for you.
#7: Don't Need Internet on Your XP PC? Cut the Cord!
Using XP for a custom line of business app or proprietary hardware-driven program you need? Most of these aging, legacy products don't require an internet connection. And if that's the case, you can likely just cut the cord (LAN cord, that is) and get the machine off the internet completely.
I still think that using the firewall approach with VLANs and a separate subnet is the smartest bet, since you will be able to continue getting patches and antivirus updates in this manner while keeping the rest of your machines safe, but this is a good secondary (free!) option.
#8: Ditch the 'Ole Whitebox: Virtualize your XP PC on VirtualBox or Hyper-V
Not only does your old XP box present a security risk in its physical form, but it also likely isn't the most energy efficient computer, either. To give yourself a middle ground to continue operating XP in a controlled environment, while getting rid of the energy waste associated, you can opt to virtualize. There are many different ways to do this, with options out there from VMWare, Oracle, Microsoft, and numerous others. But I'm going to focus on the two that happen to be completely free.
Our favorite virtualization platform is Microsoft's Hyper-V, which is available for free in the Pro and Enterprise editions of Windows 8 and 8.1. You can also find it in Server 2008 R2 and above, but non-infrastructure geeks likely won't go this more complicated route. You can follow this excellent guide on getting started with Hyper-V in Windows 8/8.1 from Greg Schultz.
You may be wondering how you can easily get your Windows XP system "as is" into a virtual machine image, usable by Hyper-V or something else. Good question, and we've got a very simple answer. Microsoft has a free tool called Disk2VHD that can convert your actual physical machine into a compressed VHD (virtual hard drive) file which can then be mounted into Hyper-V or another virtual machine program, like VirtualBox. The conversion process is usually fairly painless as long as you don't have too bad of a fragmentation problem on your disk.
The great thing about Hyper-V in Windows 8/8.1 is that you can keep your risk footprint relatively low by switching on/off external internet access to your XP virtual machine through the use of the virtual switch. This means, for example, you can connect your XP machine to the plain old internet for periods of time by giving your machine external access in the vswitch, and then turning it off or just enabling private connectivity when you are done patching or downloading updates. A solid, secure way to use internet when you need it in your VM and then shutting off access.
Alternatively, Hyper-V is available in Windows Server 2008R2/2012/2012R2 in the full GUI installation of the products, or as a standalone "Hyper-V Server" type 1 hypervisor edition that is a truly free product available for download. We use the GUI edition of 2012 R2 on our office VM server that doubles as a backup file server. It works well, but again, licensing for Server 2012 R2 is quite more costly than just using Windows 8.1 Pro that comes bundled with your regular PC.
Windows 8/8.1 Pro come with a completely free virtualization platform called Hyper-V, which merely needs to be installed and configured right within the Control Panel. We run our virtual machine testbeds on Hyper-V within Server 2012 R2 without any issues. Using a simple free tool like Disk2VHD, you can convert your aging physical XP PC into a virtual machine. It's awesome technology and Microsoft gives it away at no charge. (Image Source: MSDN Blogs)
While Hyper-V is a great option that requires no extra software, Oracle provides a free type 2 hypervisor called VirtualBox. This open source program runs on nearly any platform (including Mac and Linux) and is updated fairly frequently. I consider it a great alternative if you don't have the means or hardware that supports Hyper-V, but I will warn you that the experience is just a little more "buggy" in my testing. VirtualBox has its quirks, and for the most part works well, but be forewarned that it is sometimes picky on the hardware it likes, and has a tendency to crash at the oddest moments.
Not to knock it in any way, as it's a great way to get that XP PC taken down so you can virtualize your needs. For situations where I don't want to fiddle with configuring a full Hyper-V VM (which doesn't take long - but Vbox is quick and dirty) I just fire up VirtualBox and do my testing as needed. It can take VHD files that are spat out by Disk2VHD that I mentioned earlier, which means you have an easy conversion route for your physical machine to a virtual file that is bootable.
One great thing about VirtualBox is that you don't need any virtual switch knowledge to get networking running in a virtual machine. It's as plug and play as it gets. But be careful -- this may be as much of a curse as it is a blessing, if you aren't careful (especially if your XP machine isn't protected by good AV).
#9: Switch to a Limited User Account, as Rights can Kill
Kill may be a strong word, but it's an accurate description of what administrative rights can do to a poorly protected Windows XP PC. Microsoft, for better or worse, trained legions of Windows XP users that Administrative rights on every user account were a necessary evil. Standard user accounts and UAC helped reverse this mistake by the time Windows Vista came out, but it was too late: a decade of XP machines with full admin rights have been killing PCs virtually due to infection.
While you can't eliminate your infection threat, you can surely minimize it by converting your user account on XP into a limited user profile. This will give it rights more in line with what a standard user account in a company with Active Directory has privy to. Enough to get your work done; but not enough to do serious harm most of the time.
The procedure for doing this is relatively simple and outlined by Microsoft here. Be mindful that some legacy software may require constant admin rights to run properly. If this is the case, you may be out of luck, but it's worth a shot -- for your security sanity.
#10: Use DNS Filtering From OpenDNS or Norton DNS
There's an old adage that says you might as well stop 'em before they even reach the gates. Well, in the world of computer security, one way of doing just this is by enlisting the help of a third party DNS provider that literally filters out the bad stuff before it can even get to you. While you may have heard about Google DNS, do know that Google's DNS service does not explicitly filter out infected domains or malware links.
Two providers that do actually provide such filtering are OpenDNS and Norton DNS (by Symantec). I wrote extensively about the benefits of OpenDNS a while back, but the information is still extremely relevant. In plain terms, an alternate DNS provider is the digital yellow pages provider that converts all of your computer's internet website requests from FQDN (fully qualified domain names) into standard IP format used by the world's computers to communicate.
Every PC that connects to the "web" as we know it uses some sort of DNS provider, whether it be your ISP's default internal servers or you can opt for a third party service like OpenDNS. As a matter of practical security, we usually configure customer homes and offices with a combination of third party DNS providers in order to not only provide resiliency in the face of outages at ISP datacenters, but also to keep blatant phishing and malware links at bay.
If you are running your XP machine physically or in a VM, it's super easy to configure your manual DNS settings within that box to use something like OpenDNS or Norton DNS. You can find detailed instructions on how to do so from this OpenDNS support article. Norton DNS provides a similar help document if you want to use Symantec's servers.
While using alternative filtering-enabled DNS will not bullet proof your internet experience, it will help cut down the largest malicious links that are tormenting users with malware or phishing on the web. It's another extra layer of security that is worth the 5 minutes it takes to configure.
Riding XP Into the Sunset with a Safety Belt
I know full well that many readers will go against the words of Microsoft, IT pros such as myself, and numerous others warning against using XP past April. To each his own, I say. But if you're going to head into battle on an aging stallion, you might as well have the information to give you the safest possible experience. We've been using a mixture of the above solutions for customers, and feel fairly confident in their ability to make the best of a bad situation.
What kind of things are you doing to keep XP safe after April? Virtualization? DeepFreeze? A mixture of a few different things? Let us know in the comments area below. Perhaps there's something glaring that even I missed in the above list, which may be useful for other readers.
Sharing is caring, and in the case of Windows XP security, many holdouts will be thankful.
 Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net
Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net