Adobe acknowledges another JavaScript issue with Acrobat, Reader
An independent security research firm is warning of a non-ingenious JavaScript buffer overflow ploy that modern Web browsers would probably filter out, but which impacts recent versions of Adobe Reader for PDF files.
The surprise about the latest Adobe Acrobat issue is that there doesn't seem to be much new about it, at least in terms of methodology. A group called the Shadowserver Foundation announced yesterday that it was aware of an active ploy using malformed PDF files. Embedded JavaScript in those files can trigger a kind of managed buffer overflow, the group said, which leaves the heap full of shellcode that can be executed without the need for privilege.
But Shadowserver is not taking credit for the original discovery of this exploit; in fact, its blog post yesterday, it stated it had reason to believe Adobe had already been warned. "We want to make it clear that we did not discover this vulnerability and are only posting this information to make sure others are aware and can adequately protect themselves...We believe Adobe is aware of this issue and actively working to address it," the group's Steven Adair wrote. "However, we felt it was necessary to release this information to let people know how to mitigate against the attacks as they can be devastating."
The group is crediting security researcher Matt Richard with providing it with a sample of the malicious code, and giving it reason to believe targeted attacks using that code are currently ongoing. Last year, Richard was credited as directing the rapid response team for VeriSign's iDefense laboratories.
VeriSign's stated policy for iDefense says, "With more than 250 security researchers worldwide, VeriSign discovers original vulnerabilities and notifies our customers before making our research public." But while Shadowserver indicates that Adobe was already aware of the problem, iDefense hasn't issued a new bulletin on any subject since two weeks ago.
Richard -- whom Shadowserver's Adair only identifies as "a good friend" -- was not credited as working with iDefense or VeriSign. A citation from his message to the group reads, "Testing of the exploit with XP SP3 using Adobe Reader 8.1.1, 8.1.2, 8.1.3 and 9.0.0 shows that the vulnerability results in code execution on all of them. There may be cases where Adobe Reader crashes without code execution, especially on systems with more physical memory and faster processors. This is likely due to the race condition needed to populate the heap before certain data structures are parsed by Reader."
Adobe's security advisory this morning credits no one with this latest discovery, and tells customers that a patch for these versions of Adobe Reader and Adobe Acrobat will be available by March 11.
Unlike Web pages, relatively few PDF documents actually use JavaScript. Its principal use is in distributing forms, so that Acrobat can provide live instructions to the user on how fields should be filled out, for example. Although years ago, some developers have allowed Acrobat to serve as a kind of runtime platform for just about anything that can be executed in JavaScript, Web browsers proved to be far more ubiquitous for that purpose. As a result, JavaScript use in PDFs has been limited.
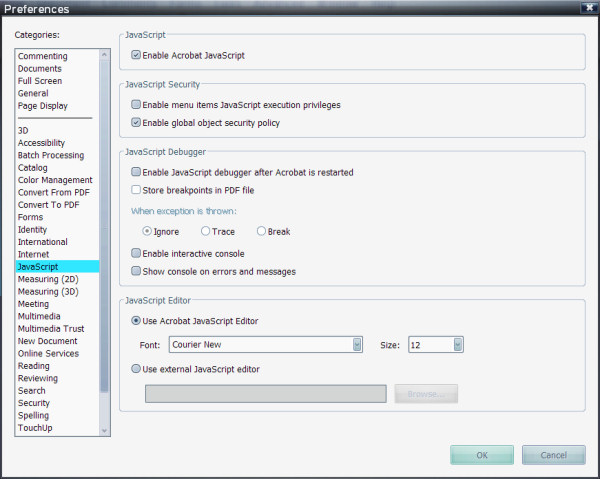
But recipients of PDFs don't actually know that little fact, and may also be blissfully unaware that JavaScript execution is turned on by default for both Acrobat Professional and the free Adobe Reader. Turning off JavaScript is easy, and probably won't impact most of the PDFs you'll ever use. In both Acrobat Professional and Reader, from the Edit menu, select Preferences, then from the Preferences dialog box, in the list marked Categories, choose JavaScript. At the very top, there will be a frame with a single check box marked Enable Acrobat JavaScript. Uncheck this box and click on OK. This will protect you from any possible PDF exploit with minimal impact on the documents you read every day, until Adobe releases its patch.