Two-thirds of office workers bypass security protocols

Almost two-thirds of office workers admit they've prioritized productivity over safe cybersecurity practices -- 63 percent also own up to using a corporate device to access social media, messaging or entertainment sites/applications.
Research from identity and access management company CyberArk also shows that 80 percent access work applications from personal devices, with C-suite executives being among the worst offenders.
Small businesses lack mobile device security policies

Smaller businesses lack the tech resources of larger ones so it's common practice that they not only allow employees to use their personal mobile phones to complete work tasks but in many cases actively expect them to.
Research carried out by OnePoll for SME security solutions company CyberSmart finds that 60 percent of organizations expect their employees to use mobile devices to carry out work tasks despite not providing all of them with work phones.
79 percent of security pros don't think their company has adequate protection

Half of security professionals say it's almost impossible to find the right balance between security and employee productivity, and 79 percent don't think their security protections are adequate.
A new study from 1Password, based on a survey of 1,500 North American workers, including 500 IT security professionals, finds 69 percent of security pros admit they're at least partly reactive when it comes to security. While 61 percent believe they're being pulled in too many conflicting directions.
Why identity security could be the Achilles heel of your business [Q&A]

Most successful cyberattacks rely on compromised identity or social engineering. Yet this can be a major blindspot for enterprises with basic awareness of the problem lacking and a growing number of personal devices used for work.
We spoke to Jim Taylor, chief product officer of identity platform RSA, -- which recently published a report on the issue -- to learn more about the problem and how it can be addressed.
Unauthorized apps put businesses at risk

The risks from shadow and unauthorized apps have been known for years, but new research from Armis finds employees of 67 percent of UK organizations are introducing risk to the business by downloading applications and software onto assets without the knowledge or management of IT or security teams.
In addition the study, carried out by Vanson Bourne, finds 39 percent of enterprises admit to feeling challenged by increasingly complicated regulations and governance requirements.
Half of European enterprises have no formal BYOD policy

The shift to remote and hybrid working has led to many more people using their personal devices for work purposes.
Yet a new survey, from Apple device management specialist Jamf, reveals that 49 percent of enterprises across Europe currently have no formal Bring-Your-Own-Device (BYOD) policy in place, meaning they have no visibility into or control over if and how employees are connecting personal devices to corporate resources.
Microsoft releases Windows 365 Switch to simplify moving between a cloud PC and the desktop
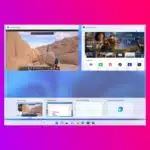
Microsoft has announced the availability of the public preview of Windows 365 Switch. The utility makes it easy for Windows 11 users to jump between a Windows 365 Cloud PC and the local desktop.
The company highlights the benefits of the feature to BYOD scenarios, pointing to a seamless experience from within Windows 11 via the Task view feature. Using Windows 365 Switch, switching between a Cloud PC and a local desktop can be achieved with keyboard commands, as well as a mouse-click or a swipe gesture.
Summer time and cybersecurity ain't easy

Cybersecurity concerns are likely to go out of the window during the summer months according to a new study which finds that 33 percent of employees in the US and UK are less likely to worry about following best practices while working in the summer.
The research, from API and application protection platform ThreatX, also shows IT teams are struggling to monitor and enforce BYOD policies during summer months when more employees are traveling or working remotely.
71 percent of employees have sensitive work data on personal devices

Allowing people to use their own devices for work comes with risks. A new report from SlashNext shows that 43 percent of employees were found to have been the target of a work-related phishing attack on their personal devices.
When it comes to securing BYOD hardware, 90 percent of security leaders say that protecting employees' personal devices is a top priority, but only 63 percent say they definitely have the tools to do so adequately.
Why BYOD could be the key to increased business productivity

A 'work device' isn’t what it used to be. Employees are no longer restricted to a single, company-issued device. Instead, they move between devices based on task, time of day, and location. One minute, they might be working at a desk on a Mac, while the next they are on the move, staying productive from an iPhone.
Research has shown that employees highly value the ability to choose which device(s) they use. In fact, 87 percent of respondents in an independent global survey, conducted by Vanson Bourne in 2021 said choosing their work device was important to them, and 89 percent said they’d even be willing to sacrifice part of their salary to be empowered to choose their own technology.
Fueling the Apple BYOD revolution [Q&A]

It's no secret that BYOD provides incredible benefits on paper -- from increased productivity to more flexibility and streamlined output. But unfortunately, many initiatives fail to take off due to security and privacy concerns.
Mosyle CEO Alcyr Araujo believes this doesn't always have to be the case, and that Apple devices are primed to offer the best balance for BYOD. We spoke to him to find out more.
The changing face of the digital workspace

One of the effects of the pandemic was a rapid and massive shift to remote working and it's becoming increasingly clear that we're not going to be returning to quite the way things were before.
The Digital Workspace Ecosystem Alliance (DWEA) has produced a State of the Digital Workspace 2023 report, based on the responses from 2,660 enterprise IT survey respondents worldwide, looking at the current work landscape.
Hybrid work needs to move on from pandemic-era tech

When the pandemic-inspired lockdowns hit in 2020, businesses rushed to established technologies like VPNs in order to support remote working.
But new research conducted by Gartner Peer Insights for Citrix Systems shows 96 percent of IT leaders think these technologies no longer cut it and are rethinking their approach.
Bring Your Own Device can empower your employees, and increase productivity too

Companies have been more trusting of their employees since the pandemic forced everyone to work at home. In much the same way that employers realized their staff could be trusted to get on with the job despite being unsupervised, they are also realizing that they can trust them to use their phone for work without opening Candy Crush.
Technology is encouraging employee autonomy and the advantages of convenience, efficiency and productivity are being recognized by forward-thinking businesses.
Poor security practices still a challenge for hybrid work

Almost a third (29 percent) of workers still use the same passwords for both personal and work accounts, potentially compromising their organisation if a personal account gets hacked.
A new study of 2,000 UK adults carried out by OnePoll for professional services company Gemserv also shows 39 percent of respondents access corporate accounts and content from their personal devices often or always, with another 24 percent doing so sometimes.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.