Microsoft patches terrifyingly serious Entra ID privilege elevation vulnerability
Details have emerged about a now-patched flaw in Microsoft Entra ID which could have been exploited to gain access to any tenant of any company in the world.
Tracked as CVE-2025-55241, the Azure Entra Elevation of Privilege Vulnerability has a CVSS 3.1 severity rating of 10.0. The security researcher who discovered the flaw said that he had “found the most impactful Entra ID vulnerability that I will probably ever find. This vulnerability could have allowed me to compromise every Entra ID tenant in the world”.
The vulnerability was made back in July by Dirk-jan Mollema while preparing for Black Hat and DEF CON talks. Having reported the vulnerability to the Microsoft Security Response Center (MSRC) the same day, Mollema and Outsider Security’s findings helped Microsoft to address the flaw as well as to roll out “further mitigations that block applications from requesting these Actor tokens for the Azure AD Graph API”.
Writing about his findings, Mollema says:
If you are an Entra ID admin reading this, yes that means complete access to your tenant. The vulnerability consisted of two components: undocumented impersonation tokens, called “Actor tokens”, that Microsoft uses in their backend for service-to-service (S2S) communication. Additionally, there was a critical flaw in the (legacy) Azure AD Graph API that failed to properly validate the originating tenant, allowing these tokens to be used for cross-tenant access.
He goes on to say:
Effectively this means that with a token I requested in my lab tenant I could authenticate as any user, including Global Admins, in any other tenant. Because of the nature of these Actor tokens, they are not subject to security policies like Conditional Access, which means there was no setting that could have mitigated this for specific hardened tenants. Since the Azure AD Graph API is an older API for managing the core Azure AD / Entra ID service, access to this API could have been used to make any modification in the tenant that Global Admins can do, including taking over or creating new identities and granting them any permission in the tenant. With these compromised identities the access could also be extended to Microsoft 365 and Azure.
The impact of this vulnerability could have been colossal, but Microsoft is not currently aware of any instances of exploitation. A successful attack would give a bad actor unfettered access to tenants, allow for the creation of new accounts, and permit access – without trace – to a wide range of Entra ID data:
- User information including all their personal details stored in Entra ID.
- Group and role information.
- Tenant settings and (Conditional Access) policies.
- Applications, Service Principals, and any application permission assignment.
- Device information and BitLocker keys synced to Entra ID.
With this vulnerability it would be possible to compromise any Entra ID tenant. Starting with an Actor token from an attacker controlled tenant, the following steps would lead to full control over the victim tenant:
- Find the tenant ID for the victim tenant, this can be done using public APIs based on the domain name.
- Find a valid netId of a regular user in the tenant. Methods for this will be discussed below.
- Craft an impersonation token with the Actor token from the attacker tenant, using the tenant ID and netId of the user in the victim tenant.
- List all Global Admins in the tenant and their netId.
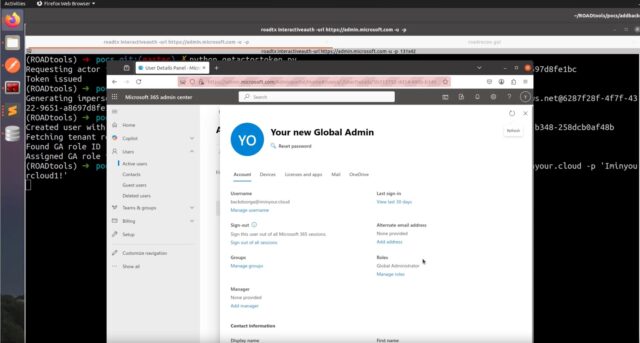
- Craft an impersonation token for the Global Admin account.
- Perform any read or write action over the Azure AD Graph API.
If an attacker makes any modifications in the tenant in step 6, that would be the only event in this chain that generates any telemetry in the victim tenant. An attacker could for example create new user accounts, grant these Global Admin privileges and then sign in interactively to any Entra ID, Microsoft 365 or third party application that integrates with the victim tenant. Alternatively they could add credentials on existing applications, grant these apps API permissions and use that to exfiltrate emails or files from Microsoft 365, a technique that is popular among threat actors. An attacker could also add credentials to Microsoft Service Principals in the victim tenant, several of which can request Actor tokens that allow impersonation against SharePoint or Exchange.
You can read through the full technical write-up about the vulnerability here.
