
The internet's first .com was registered 40 years ago today -- six years before the launch of the web
In 1985, at a time when we were listening to the likes of Careless Whisper by George Michael and Material Girl by Madonna, and getting ready to go Back to the Future, Symbolics Computer Corporation was developing Lisp machines for use in early AI work. On March 15, 1985, 40 years ago today, the Cambridge, Massachusetts-based firm registered what was to be the world’s first .com domain name, symbolics.com.
In those days, well before the launch of the World Wide Web in 1991, requests were submitted by fax or mail and approved manually by the Stanford Research Institute under the Defense Data Network contract. The symbolics.com registration marked the beginning of commercial web addresses and came more than a decade before .com domain names became widely used by businesses and individuals.

Silicon Power Endura SSDs promise speeds up to 7000MB/s -- but where’s PCIe 5.0?
Silicon Power has announced its latest lineup of solid state drives, the Endura series, featuring four new models: E55, E60, ED90, and ES75. Built with 3D TLC NAND, these SSDs offer a mix of performance and reliability for different types of users. But here’s the thing -- there’s no PCIe 5.0 option. In 2025, that’s a tad surprising.
The E55 is the entry-level model, a meager 2.5-inch SATA III SSD. It comes in sizes from 512GB to 2TB and delivers read speeds up to 500MB/s and write speeds up to 450MB/s. If you’re still running a mechanical hard drive, this is an obvious upgrade.

Like it or not, Google Assistant is being replaced by AI-powered Gemini on millions of devices
Google Assistant is being consigned to history. Almost a decade after it first launched, Google’s voice-activated digital assistant will be replaced by Gemini, Google’s updated AI-powered assistant.
If you’re an existing user of Google Assistant, you will no doubt have noticed the offer of switching to Gemini. While this has been, and remains for now, an optional switch, soon there will be no choice -- it will be Gemini all the way.

AI PCs set to boost artificial intelligence at the edge
Research by IDC for chip maker AMD looks at how enterprise IT decision makers are adapting their strategy as high-performance AI PCs begin shipping.
AI PCs feature specialized neural processing units designed to enable AI at the edge. They combine with powerful CPUs and GPUs and are typically built as a single system on a chip, enabling local AI models.
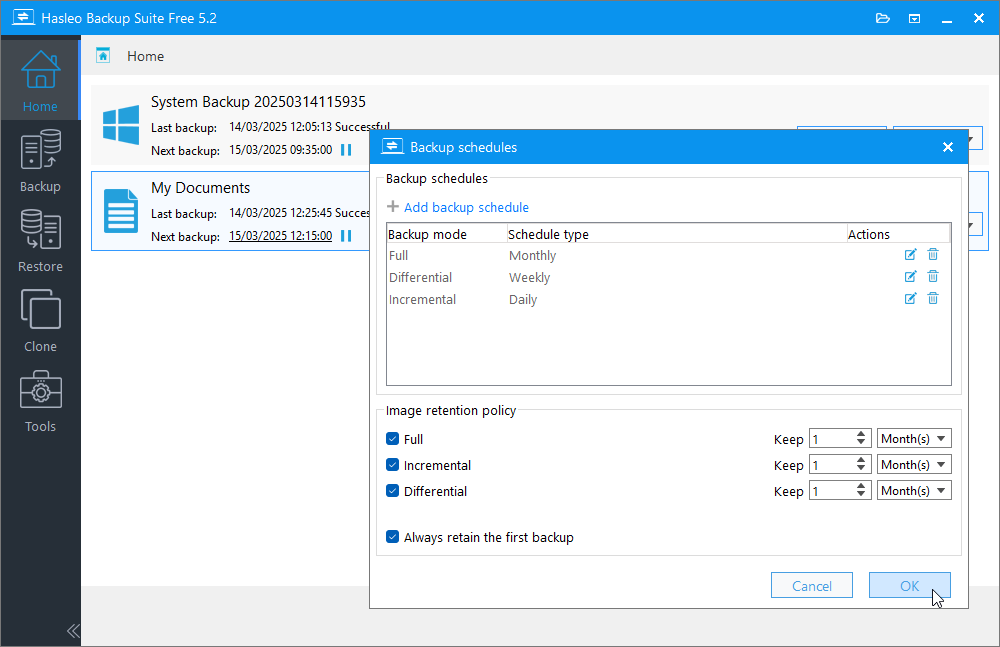
At last! New Hasleo Backup Suite Free gives Windows users the protection their data -- and system -- needs
Looking for a way to protect your PC from the dreaded specter of data loss or system corruption? The most effective strategy involves backing up both data and your Windows system, and the best free tool for the job is Hasleo Backup Suite 5.2 Free.
Windows’ own backup tools aren’t really fit for purpose, while our previous backup tool of choice -- Macrium Reflect -- dropped its free tier a few years ago. That was forgivable, but we draw the line at switching to a subscription model. Thankfully, Hasleo Backup Suite offers a comprehensive -- and completely free -- alternative.

AdGuard brings full-system ad blocking to Linux with new standalone app
For many years now, Linux users looking to block ads have needed to piece together a mixture of browser extensions, DNS-based filtering, and network-wide tools (such as Pi-hole). While these solutions certainly help, none of them offer complete system-wide protection.
Yeah, with Windows and macOS users having access to various tools for years, Linux users have mostly had to rely on workarounds. That’s where AdGuard for Linux comes in! Yes, folks, we finally have a dedicated ad blocker that works across all browsers and applications!

The poor the bad and the terrible -- popular passwords around the world
Passwords are an essential part of our digital lives, yet many people still use weak or simple combinations of letters and numbers that can be cracked in just a few seconds.
A new report from Safety Detectives, based on analysis of a 2.5TB database containing passwords compromised through data breaches and malware attacks across 44 countries, looks at the current state of password habits, to highlight how these practices have evolved over time.

Is AI the answer to compliance challenges? [Q&A]
Increasing amounts of regulation are creating an issue for businesses as they seek to ensure compliance whilst still delivering on their core activities. This is leading many to boost the size of their security teams.
We spoke to Jay Trinckes, CISO of Thoropass, who believes that using AI, with its ability to analyze vast amounts of data quickly and accurately, will be key to bridging this gap without the need for massively expanded staffing.

ADATA SC730 is a tiny external SSD with USB-C and USB-A connectivity
Well, folks, ADATA has announced the SC730 -- a super-compact external solid state drive that features both USB-C and USB-A connectors. Weighing just 7.8g and measuring a mere 36mm in length, this SSD is smaller than many USB flash drives but delivers speeds up to 600MB/s.
The SC730’s dual-interface design means it works with everything from laptops and tablets to smartphones and gaming consoles like the PlayStation 5 and Xbox. ADATA is also highlighting its compatibility with iPhone 15 and newer models, letting users back up photos and videos directly without needing extra adapters.

Working with AI: When should humans be 'in the loop' or 'over the loop'?
It’s a fact that over 80 percent of AI projects fail. Not because of AI’s potential, but because businesses prioritize minor use cases over real transformation. Automated insights and meeting summaries may be impressive, but AI only drives impact when seamlessly integrated into workflows, turning insights into action.
Deploying AI successfully isn’t simple, and organizations are complex. Effective AI deployment requires a clear framework for human oversight. AI should usually enhance human decision-making, providing targeted, explainable, and interactive insights. But in some cases -- especially when decisions are time-sensitive or involve vast amounts of data -- humans cannot oversee every output in real time. This raises a key question: when should humans be ‘in the loop,’ actively making decisions, and when should they be ‘over the loop,’ overseeing AI without direct intervention? Getting this balance right is crucial for both AI’s effectiveness and its responsible use.

Understaffed but still delivering -- the reality of cybersecurity teams
A new survey of over 900 security decision makers across the US, Europe and Australia, finds 60 percent of security teams are small, with fewer than 10 members. But despite their size, 72 percent report taking on more work over the past year, and an impressive 88 percent are meeting or exceeding their goals.
The study, carried out by IDC for AI-powered workflow company Tines, also finds security leaders are bullish about AI with 98 percent embracing it and a mere five percent believing AI will replace their job outright.

ViewSonic ColorPro VP2788-5K is the 5K monitor Mac and Windows users have been waiting for
ViewSonic has just rolled out the ColorPro VP2788-5K, and this 27-inch monitor should absolutely be on your radar! The display features a 5K (5120x2880), plus a 99 percent DCI-P3 color gamut.
Mac users should love how well this monitor plays with macOS, offering what ViewSonic calls “Retina-like” sharpness. Of course, this isn’t just for Apple fans -- Windows users will get the same experience.
DeepSeek outperforms US models in new AI Trust Score
Chinese AI models (like DeepSeek) are outperforming US models like Meta Llama in specific categories such as sensitive information disclosure according to a new AI Trust Score introduced by Tumeryk.
It evaluates AI models across nine key factors, including data leakages, toxic content, truthfulness, and bias. This enables CISO’s to ensure their AI deployments are secure, compliant, and trustworthy, and offers developers solutions for addressing any issues in their AI applications.

Microsoft admits that a recent Windows update may have made your printer act erratically
If your printer has been spontaneously printing at random, you’re not alone – and you can almost certainly blame a wonky Windows update from Microsoft.
The company has acknowledged a strange print issue affecting some users of Windows 10 and Windows 11 who installed recent updates for the operating systems. The peculiar behavior affects USB connected dual-mode printers that support both USB Print and IPP Over USB protocols and Microsoft has been forced to resort to a Known Issue Rollback (KIR).
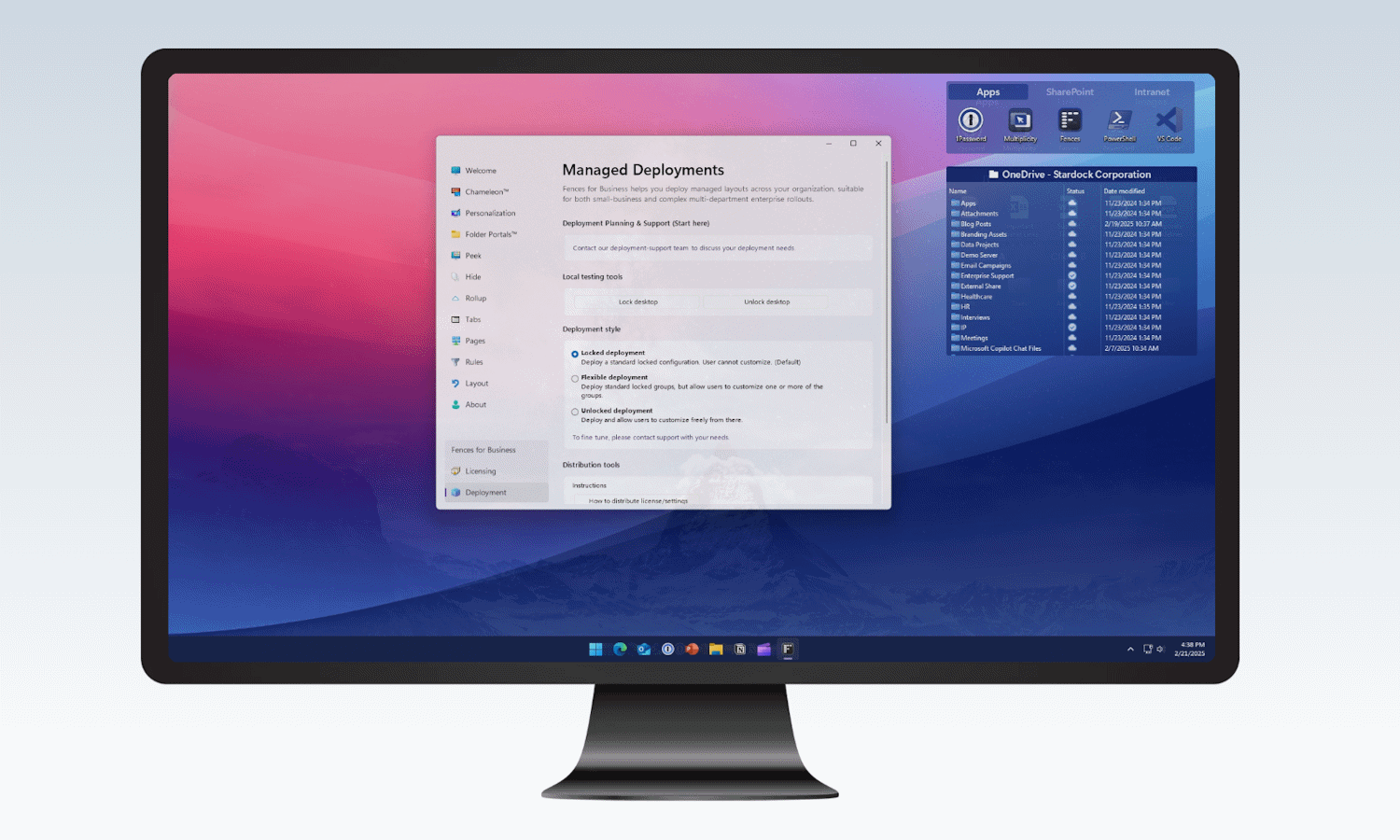
Take control of Windows 11 and save a tasty 10% off the incredible Stardock Fences 6 during beta testing
Few people would argue that Windows 11 is perfect; in fact, for many people the operating system has many flaws and failings. A lot of the weaknesses of Windows have been addressed by the developers of PowerToys, but this is far from being the only suite of utilities out there.
Stardock is a company with a history of producing handy tools for Windows, and Fences is a productivity, organization and workflow enhancing tool that can make Windows 11 work for you. To coincide with the release of the latest beta version of the utility, the company is giving 10 percent off Fences 6. Here’s what this incredible tool has to offer.
