
HyperX ships more than 60 million RAM sticks
HyperX -- Kingston's gaming brand -- is most well known for high quality RAM. With that said, it has expanded over the years to include gaming peripherals, such as mice, keyboards, headsets, and more. Still, despite a more diverse product offering, memory remains the crown jewel of its business.
To highlight just how important RAM is to HyperX, today, the company makes a shocking announcement. You see, the company has achieved an impressive milestone -- more than 60 million memory modules shipped since 2002!

Bad Intel audio driver kills sound in Windows 10 -- here's how to fix the problem
Microsoft has had a tough time of it lately. The Windows 10 October 2018 Update deleted files for some users, introduced display audio problems, and broke Edge and Windows Store apps. It was so awful, that Microsoft was forced to pause the update, and send it back for testing.
As if all that wasn’t bad enough, an Intel audio driver was incorrectly pushed to devices via Windows Update late last week, which unfortunately killed the audio for those who received it.

Enterprises still face roadblocks to using analytics
Business and IT decision makers are becoming increasingly frustrated by the complexity, bottlenecks and uncertainty of today's enterprise analytics, according to a survey of senior leaders at enterprise-sized organizations from around the world.
The study by research firm Vanson Bourne for data intelligence company Teradata finds significant roadblocks for enterprises looking to use intelligence across the organization.

New technology helps businesses to assess cyber risks
In a world of digital transformation projects that increasingly mean more links to suppliers and partners, it can be hard for companies to assess the risk presented by opening up their data to third-parties.
To address this problem RiskRecon is launching new asset valuation algorithms that automatically determine the inherent risk value of any internet facing system.

Cyberattacks shift their focus onto business in third quarter
After a relatively quiet first half of the year, cyberattacks have come back with a bang in the third quarter according to the latest report from Malwarebytes.
Businesses seem to have become the main focus of attacks, experiencing more cybercriminal activity this quarter, with detections up by 55 percent, while consumer detections increased by only four percent over the last quarter.

Malicious messages are locking up PlayStation 4 consoles
We've heard of problems with specially-crafted messages being used to lock up iPhones, and now a similar problem has been found with the PlayStation 4. Anyone who receives one of these messages will find that their console completely locks up -- and the only way out of it is to perform a factory reset.
The problem lies in messages that include unrecognized characters, and it is being exploited by some gamers to boot people offline in the middle of games -- Rainbow Six in particular. While there is no fix available at the moment, there are steps you can take to prevent the issue affecting you.

UK government launches guidance to help secure IoT devices
There are expected to be more than 420 million internet connected devices in use across the UK within the next three years and if poorly secured these can leave people exposed to security issues and even large scale cyberattacks.
To address this, a new voluntary Code of Practice is being launched by the UK government to help manufacturers boost the security of internet-connected devices such as smartwatches, virtual assistants and toys.

Privacy: Twitter is under investigation for data collection through its link-shortening system
Twitter is being investigated by the Irish Data Protection Commission (DPC) over concerns about how much data it collects through its t.co link-shortening tool.
The Irish privacy regulator is concerned about the amount of data Twitter is able to collect through the service -- something that was only heightened by the company's refusal to hand over information about link tracking when it was requested.

Microsoft employees use open letter to urge company not to get involved in JEDI military project
Last week, Google said that it had concerns about the use of AI in the US Department of Defense's JEDI (Joint Enterprise Defense Infrastructure) project, and as such it would not be bidding for the contract.
Now Microsoft employees have published an open letter expressing their concerns about JEDI, the secrecy it is shrouded in, and the potential for it to cause harm or human suffering. The letter has a simple message: "Microsoft, don't bid on JEDI".

An Unsend option is coming to Facebook Messenger
Mark Zuckerberg caused controversy around six months ago... nothing strange for Facebook you may think. On this occasion, the founder of the social network managed to upset people when it turned out he had deleted messages he had sent through Facebook Messenger: an option that wasn't -- and isn't -- available to other Facebook users.
At the time, when the matter came to light, Facebook said that the ability to unsend messages would ultimately give everyone the option to delete the messages they had sent. At long last, the feature is being tested, so we might see if released publicly in the not-too-distant future.
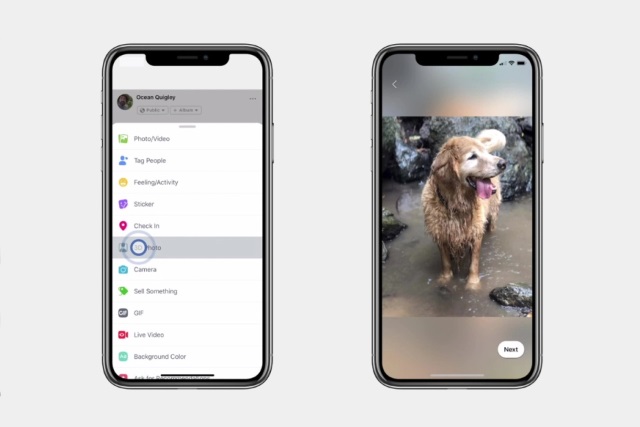
Now you can post 3D photos to Facebook from your smartphone
A new option is in the process of rolling out to Facebook users around the world: the ability to post 3D photographs. The key attraction here -- apart from the fact that 3D images look kind of cool -- is that no special equipment is needed.
Of course, you have to be realistic with your expectations. The new 3D photos feature does not create interactive, fly-through images or anything fancy like that. Rather it plays with parallax effects to create the illusion of depth that you can enjoy by scrolling, panning and tilting your phone.

UBports Foundation releases Linux-based Ubuntu Touch OTA-5
Ubuntu Touch never lit the world on fire as many Linux fans had hoped, but to be honest, most mainstream consumers didn’t even know it existed. So when Canonical canceled it, not many people cared. Luckily, since the project was open source, it was easy for another organization — in this case, UBports — to grab the torch and run with it.
Back in August, UBports surprised many with the Ubuntu Touch OTA-4 release, which breathed new life into tablets and smartphones that ran the Linux distro. Now, OTA-5 is here to take it up yet another notch. The new version gets a new web browser called Morph which is based on QtWebEngine. Best of all, OTA-5 gets improved adaptive scaling for a better experience regardless of screen size. From a superficial standpoint, there are new wallpapers based on community submitted artwork.

Thinkware F800 Pro review
The F800 Pro is the ultimate dash cam in Thinkware's lineup. The big brother to the excellent F800 that I reviewed last year brings some nice extra features to the table, the most interesting of which is Thinkware Cloud. It's designed to be used in conjunction with your smartphone, giving you access to your car's location and notifications when someone bumps into it, among other things.
That can come in handy when you lend your car to a friend or leave it unattended in a parking lot, for instance. But there's also geofencing available, which is designed with business customers in mind (or, concerned parents, if you will). This will send a notification when the car is driven outside of an approved area.
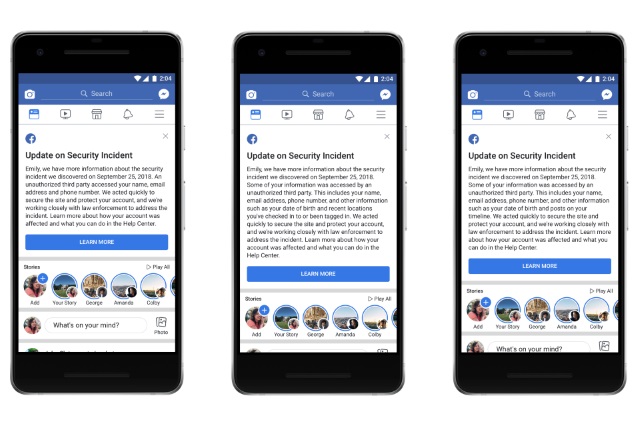
How to see if you were affected by the huge Facebook hack
The most recent Facebook security issue is one of the most serious yet for users of the social network. Depending on which numbers you are look at, the hackers who exploited a security flaw have impacted on anything between 14 and 30 million people.
Facebook is still -- with the help of law enforcement agencies -- investigating the incident, and in the meantime many people feel as those they are being left in the dark. If you want to find out if your account has been affected, here's what you need to do.

Facebook says hackers accessed highly-detailed personal data of 15 million users
In a news release with the bizarrely vague title of "An Update on the Security Issue", Facebook has revealed that the "View As" security breach it opened up about recently gave hackers access to the personal details of 15 million users.
Having previously advised that the access tokens stolen by hackers had not been used to infiltrate other apps and services, the social networking giant now says 15 million people have had their names and contact details exposed. 14 million users had significantly more details revealed, including username, relationship status, religion, hometown, birthdate, places they have checked into, and recent searches.
