Extended Windows 10 support means ditching your local account for a Microsoft Account

The drum heralding the end of support for Windows 10 has been beaten almost to death, but even at this late stage there is more news about the death of the operating system.
With the mid-October date for mainstream support fast-approaching, there are still plenty of people using Windows 10. Some have opted to take up Microsoft on its last-minute offer of extended support – but a new catch has just been revealed.
Microsoft Lens is the latest victim of AI

Users of Microsoft Lens – originally launched several years ago as Office Lens – have just a few short weeks left to use the tool.
Microsoft has announced that the incredibly popular iOS and Android app is to be “retired” (translation: killed off). Having started life under a different name over a decade ago, the app provides a way to convert images to PDF, Word, PowerPoint, and Excel files and much more. But not for very much longer.
Insider threats are getting costlier and harder to detect

A recent study from IBM revealed that insider threats were the costliest data breaches of 2024, averaging $4.99 million per incident.
Andrius Buinovskis, cybersecurity expert at security platform NordLayer, says that as more companies adopt a browser-first approach, mitigating insider threats will become even more challenging because of the limited visibility security administrators have into employee activity taking place within the browser.
Why the future of AI isn’t about better models -- it’s about better governance [Q&A]

The rise of generative and agentic AI is transforming how data is accessed and used, not just by humans but by non-human AI agents acting on their behalf. This shift is driving an unprecedented surge in data access demands, creating a governance challenge at a scale that traditional methods can’t handle.
If organizations can’t match the surge in access requests, innovation will stall, compliance risks will spike, and organizations will reach a breaking point. Joe Regensburger, VP of research at Immuta, argues that the solution isn’t more powerful AI models; it’s better governance. We talked to him to learn more.
AI-powered attacks, zero-days, and supply chain breaches -- the top cyber threats of 2025

New analysis of recent high-profile breaches and global threat patterns, reveals a cybersecurity landscape dominated by AI-enhanced attacks, organized cybercrime, and rapid exploitation of zero-day vulnerabilities.
The research, from compliance automation platform Secureframe, shows critical infrastructure, healthcare, and financial services have become primary targets as threat actors evolve faster than traditional defenses.
Microsoft warns of serious vulnerability in hybrid Exchange deployments

Microsoft has issued a warning about a high-severity vulnerability in hybrid Microsoft Exchange Server deployments.
Tracked as CVE-2025-53786, the vulnerability could allow for privilege escalation by cyber threat actors with administrative access to an on-premise Microsoft Exchange server. Although there is not currently any indication of active exploitation, the issue is considered extremely serious and requires immediate attention.
Microsoft brings AI to the Game Bar with Gaming Copilot
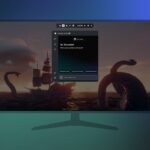
It seems that nothing is immune to being injected with AI – certainly not if Microsoft is involved. Now the company is bringing Gaming Copilot to the Game Bar.
Currently in beta testing, Gaming Copilot is now available in Game Bar for Windows PC for Xbox Insiders enrolled in the PC Gaming Preview. The arrival of Copilot in another Microsoft tool is far from being surprising, but just what does this mean for gamers?
Disney is killing off the Hulu app, bringing all content to Disney+

Disney has announced major plans for Hulu – in short, it is getting rid of the Hulu app. This does not mean, however, that Hulu itself is going away.
During an earnings call, Disney revealed that rather than maintain the Hulu app and Disney+ app separately, Hulu content will instead be made available via Disney+. This is a significant change, but it is not going to be happening immediately.
You can finally repost content on Instagram
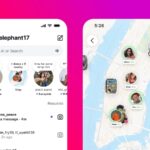
Whichever social media platform you prefer, the range of features is pretty similar across all of them. Instagram, however, has only just added the option to repost content.
Instagram has been testing the reposting of reels and posts for some time, but it has only just officially launched to all users. But this is not all. Reposting is just one of a trio of new features to hit Instagram.
Growing complexity means legacy security systems miss one in every 14 threats

Traditional detection methods are being outpaced, with a 127 percent rise in malware complexity and one in 14 files initially deemed ‘safe’ by legacy systems proving to be malicious.
A new report from OPSWAT uncovers layered threats designed to evade analysis, including obfuscated loaders such as NetReactor and evasive behaviors missed by traditional tools. These results show that modern malware intends to confuse rather than flood defenses.
New agentic AI platform helps teams fix cloud security problems faster

Security teams are often hampered by having to identify and fix issues while weeding out false positives. This is an area where AI can help and Sysdig has launched a new agentic platform designed to analyze cloud environments end-to-end and uncover hidden business risk so organizations can remediate crucial threats fast and deliver measurable improvements in their security posture.
Sysdig Sage, the company’s AI cloud security analyst, ultimately understands context from the entire business and provides clear, contextual remediation recommendations, reducing an organization’s exposure time to critical vulnerabilities.
WhatsApp launches new tools to stop scammers
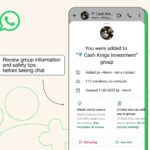
WhatsApp is now an essential communication tool for both personal and business use, and its popularity means that it is also a prime target for scammers. As such, the company has just announced the rollout of a new series of tools designed to help keep users informed and protected.
Among these new tools is a safety warning for group chats that warns about being added to new chat groups by unknown contacts. There are also tools and advice for individual chats, which are also targets for scams.
Microsoft says that it will make WinUI ‘truly’ open source

Microsoft has announced that it has plans to “truly open sourcing” WinUI, the user interface framework that is embedded in Windows. Although no specific timeframe has been mentioned, the company is “actively working toward it”.
Pointing out that making the WinUI repository open source is not just a “flip-the-switch moment” but a “deliberate process”, Microsoft lead software engineer Beth Pan says that the process is a complicated one. This is part of the reason for not being willing to commit to a specific end date for any particular milestone.
The rise of vishing and why enterprises need to be ready [Q&A]

Vishing (voice phishing) attacks have surged by over 1,600 percent so far this year, partly driven by a rise in AI-driven deepfake voice scams.
This is yet another way cybercriminals are seeking to impersonate those with access to company systems to disrupt organizations and hold data for ransom. We spoke to Anthony Cusimano, solutions director at Object First, to discover more about this trend and how businesses are at risk.
Could the UK government really ban VPNs?

As we’ve been reporting over the past week interest in VPN use in the UK has spiked following concerns about the Online Safety Act and its age verification rules.
Inevitably the government has noticed the surge in VPN use and while it insists it has no plans to ban their use the science secretary, Peter Kyle, says it will be looking “very closely” at how they’re being employed.
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.